How to create a SOAR playbook in Microsoft Sentinel
Using automation through tools such as SOAR and SIEM can improve incident response alert efficiency. One automated feature analysts can use is the SOAR playbook.
Security operations center analysts must acknowledge and triage cybersecurity incident alerts quickly. To prevent alert fatigue and avoid missing critical incidents, many SOCs are using security orchestration, automation and response platforms.
SOAR platforms use AI to help weed out false-positive alerts and prioritize incident alerts. Using automation, SOC analysts can get more information about an incident quicker and can, therefore, respond more accurately. SOAR tools also automate repetitious tasks, freeing SOC analysts to do more human-intensive work.
To help security practitioners use SOAR platforms, Benjamin Kovacevic, author and senior product manager at Microsoft, wrote Security Orchestration, Automation, and Response for Security Analysts. In the book, he explained how and why SOCs should use SOAR tools, as well as how the automation component improves incident response.
One key automation feature SOAR platforms include is the playbook. SOAR playbooks provide automation workflows for handling incident response alerts. The following excerpt from Chapter 5 of Security Orchestration, Automation, and Response for Security Analysts provides step-by-step instructions on how to create a custom SOAR playbook or find existing playbook templates. Download a PDF copy of Chapter 5 for more on Microsoft Sentinel automation, automation rules and playbooks.
From the author of Security Orchestration, Automation, and Response for Security Analysts
Read an interview with Kovacevic about how SOC analysts can use SOAR platforms to assist with and reduce mean time to detection and mean time to respond metrics.
All about playbooks
Playbooks are a list of actions that will be performed on the incident. They can include enrichment, response, remediation, and much more. To achieve this, Microsoft Sentinel utilizes a Microsoft Azure solution called Logic Apps -- a platform used to create and run automated workflows. This platform uses low- or no-code and focuses more on visual design. However, those who prefer to code more can utilize coding mode as well. Because of this, it is common to hear people refer to Microsoft Sentinel playbooks as Logic Apps.
There are two different types of Logic Apps that Microsoft Sentinel supports:
- Logic Apps Consumption: This is a single playbook that has only one workflow. It supports templates and custom connectors and is widely integrated into Microsoft Sentinel with template support. Logic Apps Consumption shares the same backend resources across different customer tenants. We will use the Logic Apps Consumption model in our hands-on examples.
- Logic Apps Standard: This is a single Logic App that can have multiple workflows. It doesn't support templates and custom connectors, which is why Microsoft Sentinel doesn't have playbook templates created in Logic Apps Standard. In Logic Apps Standard, workflows in the same Logic App share the same backend resources, and they are not shared across different Logic Apps like they are with Logic Apps Consumption. It's also important to note that when creating a Logic Apps Standard playbook, it must be stateful and cannot utilize private endpoints -- Microsoft Sentinel does not support these scenarios at the time of writing.
Microsoft Sentinel is a unified way to run a playbook, and it will make no difference whether Logic Apps Consumption or Logic Apps Standard is used.
Navigating the playbooks GUI
Microsoft Sentinel playbooks are located under the Automation tab in the Active playbooks sub-menu. In this menu, we have the option to create a playbook, open playbook details to edit or manage it, enable or disable a playbook, delete a playbook, as well as to filter playbooks by status, trigger kind, subscription, resource group, plan, and source name. If we have deployed the playbook using built-in templates, we will also get information on whether an update is available.
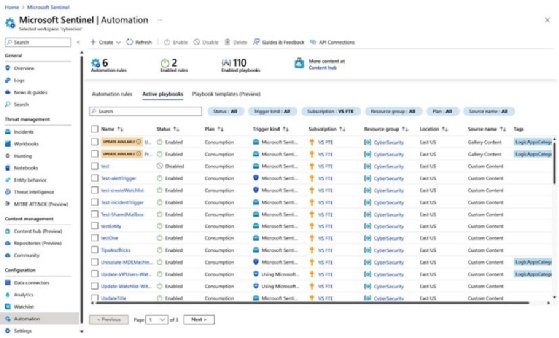
Playbooks support templates; all deployed templates can be found in the Playbooks templates (Preview) sub-menu. We can deploy any playbook, from templates to active state. We can filter templates by trigger, Logic App connector, entities, tags, and source name. If we have already deployed a playbook template, we will see a notification stating that a specific playbook is in use.
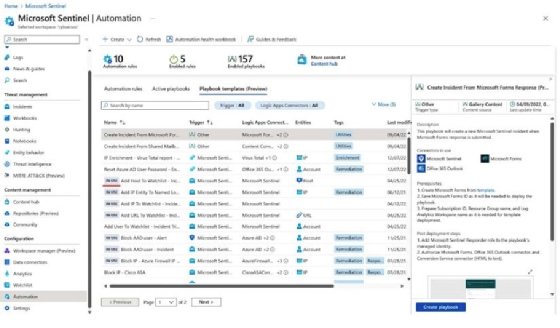
To access all templates in Microsoft Sentinel, we can utilize Content hub and the available solutions, where we can filter, among others, by the solution we need or solutions with playbook templates.

More templates can be found on GitHub and can be easily deployed to Microsoft Sentinel since they utilize Azure Resource Manager (ARM) templates. Microsoft Sentinel has an official repository with lots of content available that is ready to be deployed. The link to the official repository is https://github.com/Azure/Azure-Sentinel.
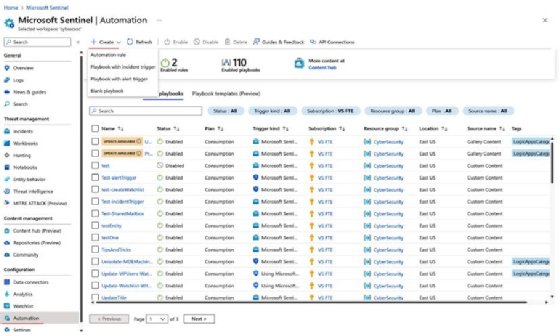
To create a new playbook, go to the Automation tab, click Create, and select one of the following options:
- Playbook with incident trigger
- Playbook with alert trigger
- Blank playbook
If we select Playbook with incident trigger or Playbook with alert trigger, we will create a Logic Apps Consumption Logic App. The first view is where we enter basic information, such as what subscription and resource we want to deploy the playbook in, the region, and the playbook's name. We can also enable diagnostic settings, which we will cover in the Monitoring automation rules and playbook health section:

In the next window, we can select how we want to authenticate a Microsoft Sentinel connection. By default, playbook creation will enable a system-assigned managed identity from the playbook and utilize it (the recommended method). However, we can utilize any pre-existing connection or change it once the playbook has been deployed.

The last step is to review the configuration and create our playbook.

Once the playbook has been deployed, we can navigate to Logic app designer, where we can start our playbook design.

From here, we can also access the code view of the playbook if we prefer to work with code.

We will go through the whole process of creation and explanation in Chapters 6 to 8, where we will cover hands-on examples.
When we want to create a blank playbook, we can choose between creating a Logic Apps Standard or Logic Apps Consumption Logic App. We can also utilize any other trigger available in Logic Apps, such as a recurrence to perform a regular playbook run, and a Microsoft Forms trigger to create an incident when a new form is filled in and when an email is received.

To run the created playbook, we have a few options:
- Attach the playbook to an automation rule for automatic triggering (which will require the Microsoft Sentinel Automation Contributor role to be assigned to a Microsoft Sentinel identity; more about this in the subsequent Permissions section)
- Run the playbook manually on the incident (which will require the Microsoft Sentinel Automation Contributor role assigned to a Microsoft Sentinel identity)
- Run the playbook manually on the alert
To create, edit, and run playbooks in Microsoft Sentinel, you will need certain permissions to perform these actions.







