Phishing prevention: How to spot, stop and respond to scams
From email scams to BEC attacks, phishing is one of the biggest fish organizations must fry. Get advice on how to identify, prevent and respond to phishing schemes.
As the old adage goes, there are plenty of fish in the sea. In cybersecurity, make that plenty of phishing scams in the cyber-sea. And despite all the warnings not to take the bait, too many people continue to fall for phishing attempts hook, line and sinker.
Phishing is a form of social engineering in which attackers trick users into providing access to data and systems. Attackers' motives range from getting users to download malware to stealing their login credentials to duping them into sharing sensitive data, such as credit card numbers, bank account info and company data.
Successful phishing attacks have repercussions on individuals and organizations alike. They can result in identity theft, data loss, financial loss, business disruptions, regulatory fines, damaged reputations and the risk of further attacks.
Phishing prevention requires a combination of people, processes and technologies:
- People. This refers to end users who are targets of -- and the first line of defense against -- phishing scams. It also includes the teams that conduct security awareness trainings in a company and the security team members who monitor, detect and respond to phishing incidents.
- Processes. They include the security awareness trainings and phishing simulations that train and test employees on phishing attempts. Processes also refer to incident response plans and security policies that establish how to react to and recover from phishing incidents.
- Technologies. These are the protocols, tools and services that scan and block phishing attempts, prevent account compromises, filter malicious websites, prevent malware from executing on devices and more.
Let's take a look at how to identify, respond to, report and prevent phishing.
How to identify phishing scams
Phishing emails used to be fairly easy to detect. The "Nigerian prince" scams of yesteryear are still rampant, but attacks today are more convincing and personalized than ever before.
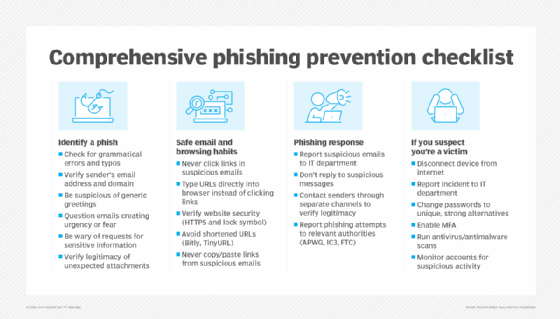
When you receive a suspicious email, do the following:
- Look for typos. Many phishing emails contain grammatical errors and misspelled words.
- Check the sender's address. If you don't recognize it, be wary. Attackers forge sender addresses to make their emails appear to be from legitimate sources. Check the IP address in the email source code to see if you can trace it to a legitimate contact. If the email comes from a genuine email address, reach out separately to the purported sender to ensure the email is real.
- Look at the greeting. Generic salutations, such as dear or customer, or the absence of a name could indicate a phishing attempt.
- Examine the sender's domain. Beware of illegitimate domains. Assess if the domain is indeed trusted or has been spoofed. For example, tectharget.com or tech1arget.com instead of the real techtarget.com.
- Beware of emails that create a sense of urgency. Many attackers try to rattle people by using urgent, time-sensitive wording or trying to scare them. Don't act hastily and without thinking; question the email and its legitimacy.
- Beware of emails that ask for sensitive information and never share data. Never trust an email, text or website that asks for personal, corporate or financial information. Legitimate companies never ask for such data. If you are concerned about an account, contact the organization using a telephone number you know is genuine. If you must enter sensitive data on a website, visit it by typing the URL into the browser. Never click the link in an email or copy and paste it. Also, ensure the site's security by checking for a lock symbol in the browser bar and making sure the URL starts with HTTPS. It should go without saying but bears repeating: Never share your passwords.
- Beware of impersonators. Phishing scams have evolved from spray-and-pray campaigns that use one tactic on multiple victims to more targeted, personalized attacks, as evidenced in spear phishing, whaling and business email compromise (BEC). In such attacks, malicious actors search the web to gather information that enables them to masquerade as known contacts and impersonate legitimate communications and transactions.
Always check who sent the email and, if in doubt, reach out separately to the purported sender to ensure the email is legitimate.
How to respond to a phishing attempt
If you suspect you have received a phishing scam, do the following:
- Look for indicators of phishing. Use the list above to identify a phish.
- Don't click links or download attachments. Never reply to a suspicious message, click on any links or download any attachments. All three actions can lead to malware being installed on your computer. In addition, never click untrusted shortened URLs, such as Bitly or TinyURL links.
- Don't copy and paste links. Never copy and paste links from suspicious emails. While you can hover over a link to see its destination, this is not always an indicator that the link is safe. Attackers can use coding to make the URL appear like a legitimate link.
- Report the phishing email to your organization. Some companies have a designated email address for users to report suspicious activity. If you receive phishing messages to your company email address, report them if possible. Likewise, some specific vendors and providers at risk of being spoofed have websites or email addresses to report scams, for example, Amazon, Netflix and Visa.
Industry groups also collect phishing attack data to shut down websites and take legal action against phishers. Report phishing scams to groups such as the Anti-Phishing Working Group (APWG), Internet Crime Complaint Center (IC3) or Federal Trade Commission (FTC).
What to do if you become a phishing victim
If you suspect you have acted on a phishing scam -- clicked a link, visited a malicious website or shared sensitive data -- do the following:
- Report it. If the incident occurred on your work device, inform your company's IT department. Report the incident to the APWG, IC3 or FTC. If you shared credit card or banking details, contact the relevant companies and one of the three major credit bureaus (Equifax, Experian or TransUnion). Monitor accounts for suspicious activity and identity theft.
- Disconnect the device. Disconnect from the internet to prevent infecting other devices and systems on the network.
- Change passwords. Update your password to a unique, never-before-used password. Implement MFA.
- Scan for malware. Run antivirus and antimalware to detect and remove any installed malware.
How to prevent and respond to phishing in organizations
Enterprise phishing prevention includes security awareness training programs, strong credential management, security tools and patch management.
Security awareness training
Phishing prevention in the form of security awareness training for employees is one of the most effective ways an organization can combat the increasingly voluminous and sophisticated threat. Teach employees how to identify and respond to phishing attacks. Security teams should hold regular trainings that not only reiterate the dangers of phishing but also cover new and existing threats.
During the training, cultivate a security culture. Explain to employees their role in securing the enterprise and maintaining cyber hygiene.
Credential management
Require employees to follow password hygiene best practices, such as creating passwords or passphrases that are easy to remember but difficult for attackers to guess. Don't rely on username/password combos. Use MFA to add more layers to password security.
Create a password policy that outlines the organization's guidelines.
Security tools
The following tools and controls won't eliminate phishing emails but help minimize them:
- Run antivirus and antimalware software.
- Deploy email filtering tools that scan and block suspicious emails before delivery.
- Use a firewall that can block suspicious IP addresses and websites.
- Use URL filtering to block known malicious websites.
- Install a web browser toolbar or extension that protects against known phishing websites.
- Use antispoofing protocols, including DMARC, SPF and DKIM to prevent email address forgery.
- Use phishing-resistant MFA.
Patch management
Install updates and patch software, systems and browsers. All the major web browsers have antiphishing features, but if not kept up to date, they will not catch the latest known malicious websites.
Likewise, keep all software and hardware up to date, including antimalware and other tools, to ensure their effective operation against threats.
Additional security measures
Supplemental phishing safeguards include the following:
- Implement the principle of least privilege.
- Conduct regular user access reviews.
- Use security monitoring technologies to detect attacks early.
- Have an incident response plan in place to react to phishing attacks.
- Use end-to-end encryption to protect communications.
Types of phishing attacks
Common phishing tactics include the following:

- Email phishing. This is the most common form of phishing. Attackers send emails with malicious links or attachments to infect their targets.
- Spear phishing. Spear phishing is more selective, with malicious hackers sending emails to a specific target.
- Whaling. Whaling targets a high-profile employee, such as the CEO or CFO, in a phishing scam.
- VoIP phishing. Also known as vishing, this is a phishing scam carried out using voice technology, such as over the phone.
- Pharming. Pharming is an attack that tricks a DNS server into replacing a legitimate cached IP address with a malicious one, thereby redirecting users to the malicious website when they type the legitimate one into the browser.
- SMS phishing. Also known as smishing, SMS phishing is a scam executed via text message.
- Social media phishing. This involves phishing messages sent via social media platforms.
- Search engine phishing. Also known as SEO poisoning, it involves attackers using search engine optimization to help their spoofed websites rank highly in online searches. Users who click the link to the spoofed site see a legitimate-looking page that is actually malicious.
- Clone phishing. This involves malicious actors replicating a previously delivered email but replacing the legitimate links or attachments with malicious ones.
- Angler phishing. Angler phishing occurs when an attacker masquerades as a customer service representative on a fake company social media account. For example, a customer who complains about a bank online might be contacted by a legitimate-looking social media account from that bank to resolve the issue when the attacker's true motive is to get the customer to download malware or share personal information.
- QR code phishing. Also known as quishing, QR phishing tricks users into scanning a QR code with their phone that leads them to download malware or tricks them into sharing sensitive data.
- Business email compromise. BEC involves attackers impersonating higher-level employees to trick employees who have access to corporate bank accounts into transferring money or sharing sensitive data with them.
- Deepfakes. These fake images, videos and audio files use AI to perform phishing attacks.
Sharon Shea is executive editor of Informa TechTarget's SearchSecurity site.








