How ransomware kill chains help detect attacks
Reconstructing cyber attacks is a key step in incident response. Learn how ransomware kill chains can help security teams detect and mitigate the consequences of an attack.
Ransomware is on the rise, but unfortunately it's impossible to prevent all these attacks, or even detect them before they wreak havoc on an organization. This is where kill chains come in.
Adapted from the military concept that helps identify the structure of an attack, a kill chain in cybersecurity is a framework used in incident response for attack analysis and reconstruction.
The most well-known one is Lockheed Martin's Cyber Kill Chain, introduced in 2011. Problem is, said Oleg Skulkin, head of the digital forensics and incident response team at Group-IB and author of Incident Response Techniques for Ransomware Attacks, the model is outdated. "Threat actors typically targeted one host and didn't try to move laterally," he said. "Nowadays, threat actors don't try to compromise one machine but entire networks. We need more steps in a cyber kill chain to explain these evolving threats."
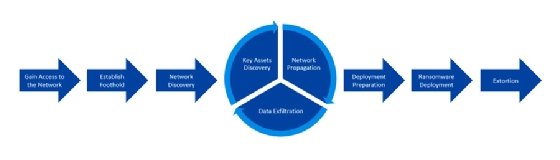
To remedy this, in his book Skulkin introduced his own kill chain: the Unified Ransomware Kill Chain, a model based on his experience with ransomware attacks.
In this Q&A, Skulkin discusses the importance of kill chains and reconstructing ransomware attacks, including why it's important to understand how attacks work in general rather than how specific threat actors work.
 Oleg Skulkin
Oleg Skulkin
Editor's note: This text has been edited for length and clarity.
How does the Unified Ransomware Kill Chain differ from other kill chains?
Oleg Skulkin: There are additional steps involved with ransomware compared to other attacks. The Unified Ransomware Kill Chain accounts for these differences. Threat actors using ransomware, for example, have ransom demands. If the victim refuses to pay, then the threat actor may try other tactics, like a DDoS attack. So, the attack might not be completed after the initial deployment of ransomware.
Traditional threat actors and state-sponsored groups also try to remain stealthy -- they usually don't post their victims' data. Ransomware gangs do the opposite because they want as much hype as possible. That's one reason why we hear a lot about ransomware attacks. In the past, few people knew about incidents. It was usually just the security team or a team that was directly engaged in the incident. Nowadays, everybody can easily install Tor, for example, and access websites to find out who the victim was, what gang was responsible and what ransomware strain was used.
Why is reconstructing an attack helpful for incident response?
Skulkin: Incident response teams need to reconstruct attacks to understand how they work. It allows you to not only detect, but also prevent such attacks and understand where your security controls and products are not working. Most enterprises have antivirus software, but many are still successfully attacked. All these ransomware attacks, unfortunately, prove that it's not enough to have basic security controls. Organizations need more advanced technology and, more importantly, a team. You can only stop human-operated attacks if you have humans to monitor and detect these attacks.
How many people should work on reconstructing attacks?
Skulkin: It depends on how many hosts you have. If you have 10,000 employees, then you need at least 10 people on your team. Many vendors provide managed detection and response services. Vendors tend to have lots of hands-on experience and greater access to cyber threat intelligence. In-house security teams usually don't have as much experience with real incidents; however, they tend to know the infrastructure better. Vendors are also responsible for monitoring a lot of organizations, whereas the in-house team can just focus on their own organization. Therefore, a combination of the two usually provides the best results.
Discover how social media can help detect cyber attacks in an excerpt from Chapter 6 of Incident Response Techniques for Ransomware Attacks by Oleg Skulkin, published by Packt.
What is your top advice for incident response teams dealing with a ransomware attack?
Skulkin: It depends on the incident, but my main piece of advice is to detect an attack as early as possible. It's also important to understand how ransomware attacks work. It's quite easy to detect attacks, even if you can't prevent one. Let's say you prevent 90% of attacks, but you still have 5% or 10% that result in enterprise-wide deployments. Once you detect an attack, you can use cyber threat intelligence to understand what else to look for, including malware families and threat actors' techniques, before they impact your infrastructure.
How do kill chains help organizations create threat profiles?
Skulkin: On each stage of the cyber kill chain -- I prefer to name it attack lifecycle because you can use different kill chains -- you should collect data based on the tactics, techniques and procedures (TTPs) used by the threat actor. This information can help you understand what group is responsible for the attack.
Nowadays, however, many affiliates jump from one ransomware-as-a-service program to another. For example, two years ago, we knew exactly when we were dealing with Maze ransomware. It's more complicated today because most threat actors merge their TTPs and infrastructures. You may check the exact procedures, but threat actors may still share the same scripts, commands or infrastructure because they often purchase their infrastructure from a third party. That's why the Unified Kill Chain is a good idea. If you understand how these attacks work, you can detect any threat actor, and it doesn't matter if they change some of their TTPs.

 Click to learn more about
Click to learn more about 





