How cyber warfare laws limit risk on a digital battleground
Retired Navy cryptologist implores enterprises to build key cyber warfare laws into their infosec strategy to improve survivability on the digital battleground in his new book.
What good are laws in war?
It's true that war is what happens when traditional discipline and diplomacy are abandoned or violated -- the same is true for cyber warfare. But, if organizations think of cyber warfare laws as guiding principles to bolster defensive strategic planning, there may be a place for laws in digital conflict zones after all.
In his book Cyber Warfare -- Truth, Tactics and Strategies, author and principal analyst at Forrester Research Chase Cunningham opined on the growing dangers of connecting to the internet today, which he described as "a live fire battlefield."
Cunningham, a retired Navy Chief cryptologist, drew on his experiences in the service, as well as historical military examples, in the book. He emphasized the solemn responsibilities organizations and security leaders have in crafting survivability strategies and explained how adopting cyber warfare laws can help. These laws of survivability are important because, Cunningham wrote, to win a war is all about being "the last one standing when the digital smoke clears."
The following excerpt from Chapter 10 of Cyber Warfare -- Truth, Tactics and Strategies published by Packt serves as a manual for organizations to increase resiliency and defense against the growing threat of cyber warfare.
Cyber Warfare -- Truth, Tactics and Strategies
Download a PDF of Chapter 10.
Read a Q&A with author Chase Cunningham.
In this chapter, we will explore the laws of survivability for operations inside this combat arena. Notice we don't say perfection, or dominance, or something like that. Instead, we speak about a pragmatic approach that is focused on using the best technology and approaches to the problem while still being honest about the fact that there is no perfection here. This is about survivability and working to keep moving forward in a never-ending onslaught of attacks. Focusing on a perfect solution and struggling to have a bullet proof network is part of what has led us collectively to the state we find ourselves in. In battle and in war, the best outcome is to survive long enough and with enough continued gas in the tank to keep moving forward. There is no perfection, and there are no perfect tools, but there are ways to be the "last one standing" when the digital smoke clears.
In this chapter, we will walk through what is and isn't necessary for continual improvement and growth and discuss what tactics, technologies, and approaches to the future state of cyber warfare are most beneficial if adopted now. Buckle up; the ride into battle is always a bit bumpy.
…
"Law 1" -- Default means dead
One of the main issues with technology in the space today is the prevalence of default configurations and accounts. Manufacturers today always set the default configurations of new software and devices to be as open and functional as possible, to enable ease of use and hopefully promote adoption of their particular product. Routers, for example, often will have a predefined password and default username. For other devices, this might mean applications that come preinstalled, again usually having "hardcoded" default login credentials available to the tool or technology.
The reason for this is because it is easier and more convenient to start using new devices or software if it has easy-to-configure default settings. But this does not help the tool or application to be secure. Default settings that are never changed and made safe creates serious security issues and provides adversaries with easy, authorized access to data and networks. Web servers, containers, and application server configurations can also be configured with default accounts that will lead to a variety of security problems.
To demonstrate just how easy this is, during the research for this chapter, I created a custom script containing thousands of Google dorks, simple requests on Google that are crafted to send back specific responses, and ran a few of them to see how many easy targets were available. In a matter of less than 3 minutes, hundreds of vulnerable applications and logins for a wide variety of devices and applications were found. A sample (with all pertinent identifying data removed) is provided here:
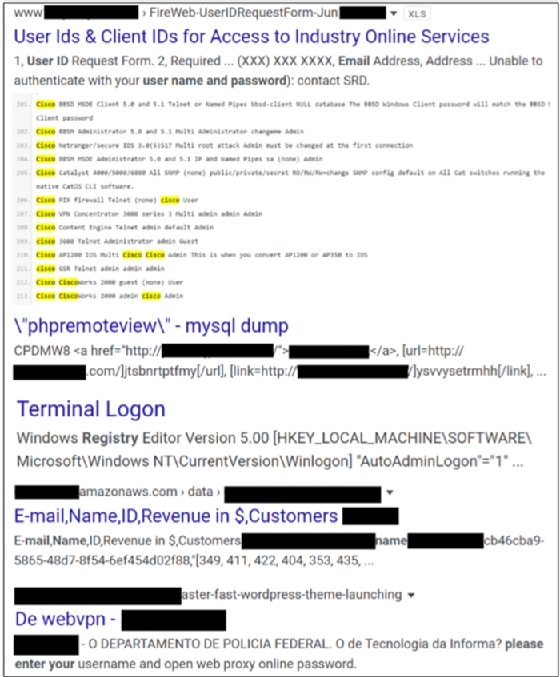
While the information found might seem somewhat non-threatening at first glance, what should be evident is the fact that with no more than an hours' worth of time, a researcher working from home was able to find large amounts of misconfigured, open, touchable resources and logins with just a script. Odds are that with a bit more time, and some targeted programming, the results could be infinitely better. And because of the interconnected nature of most networks and the usual lack of internal security controls, any one of those potential accesses could have led to further exploitation.
A point of note is that in the sample screenshots that were provided, some of the results had VPN login credentials, email and user IDs, login information, and a variety of other intelligence that could have been used for attack vectors. And all those results were based on the script looking for default configurations and user accounts, nothing spectacular. Were this script to be better programmed and tied into an automated ML backend that could expedite and tailor the commands and parse the responses, the potential for problems increases exponentially.
Looking at GitHub, one popular tool is changeme.py:
https://github.com/ztgrace/changeme
Changeme.py focuses on detecting default and backdoor credentials, and not just common account credentials. The tool's default mode is to scan HTTP default credentials, but it can scan for other credentials if the script is modified slightly. Changeme.py stores collected credential data in yaml files. Changeme.py can gather information or intel from almost every protocol that is used on systems today. Targets can be specified by using a single IP address or host, a subnet, a list of hosts, a network scanner output like an Nmap xml file, or a Shodan (a popular device polling database for hackers and penetration testers) query:
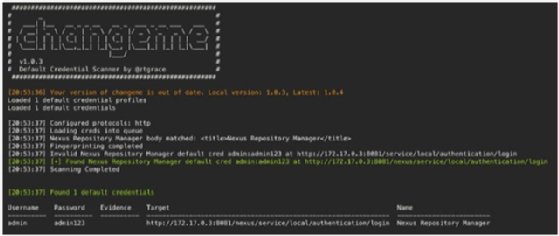
The following are common scan examples:
- Scan a single host: ./changeme.py 192.168.59.100
- Scan a subnet for default creds: ./changeme.py 192.168.59.0/24
- Scan using an Nmap file: ./changeme.py subnet.xml
- Scan a subnet for Tomcat default creds and set the timeout to 5 seconds: ./changeme.py -n "Apache Tomcat" --timeout 5 192.168.59.0/24
- Use Shodan to populate a targets list and check them for default credentials: ./changeme.py --shodan_query "Server: SQ-WEBCAM" --shodan_key keygoeshere -c camera
- Scan for SSH and known SSH keys: ./changeme.py --protocols ssh, ssh_key 192.168.59.0/24
- Scan a host for SNMP creds using the protocol syntax: ./changeme. py snmp://192.168.1.20
The point of these examples is that if it is this easy for someone conducting research to find access to such resources, it should be evident to anyone that it should be a matter of the highest priority to remove default configurations. Not doing so threatens the entire network that the default item is connected to, and almost guarantees that a compromise will occur.
Bots and automated AI/ML tools are available to make this intelligence collection even easier and do not require nation state-level capabilities to use.
"Law 2" -- Think strategically, move tactically
In warfare, the importance of the need for movement within the battlespace is accepted as critical to survivability. Most of the time, the chaos of the space and the ever changing, and innovating, enemies' actions dominate the thoughts and plans of the defenders. The ways in which actions are being taken by each party result in a constant game of cat and mouse. It is only when one side recognizes that they must more cautiously engage in strategic thinking while enabling tactical movement that the balance of power begins to shift.
This is especially true in cyber warfare. For the last two decades, the major power player nation states on the planet have been engaging with one another in the tactical sense. A constant back and forth of who has the best intelligence and which unit has the newest and most powerful exploitation solution has continually been part of the tactical firefight between nation states. While there could be some argument that the strategy side of these engagements have been part of the equation, in reality the strategic outcomes from those tactical engagements have been tangential to the never-ending game of chess in cyber warfare. No major "wins" have been realized for any nation to date. Yes, there have been some gains and some losses, but, if you look at what has resulted from nation state-level strategic engagement in cyber warfare, no real net gain has been realized.
For any unit or organization to survive -- and hopefully thrive -- in a warfare environment, there must be an adoption of a strategy at the grandest level. Failure to realize the overarching intricacies and dependencies that are present between actors and their command and control systems and infrastructures is an exercise in failure.
A classic example of how tactical movements based on a lack of patience and strategic thinking can lead to exceptionally bad outcomes can be found by observing the scenario of Custer's Last Stand. On June 22, 1876 General Terry sent Colonel George A. Custer and his 7th Cavalry in pursuit of the Indian leader, Sitting Bull. That pursuit would lead to Little Bighorn Valley. General Terry's plan was for Colonel Custer to attack the Lakota and Cheyenne Indians from the south. This would splinter the Indian forces into a smaller force that could be dominated by Custer's more mobile cavalry forces. On June 25, Custer's scouts discovered the location of Sitting Bull's forces. Colonel Custer maneuvered to a position that would allow his forces to attack Sitting Bull's forces at dawn the following day. Unfortunately for Custer, Sitting Bull's scouts spotted Custer's forces moving into position and moved to inform Sitting Bull of the coming attack.
Instead of retreating at the realization that he'd been discovered, reorganizing his forces, and strategically planning his next move, Custer attacked. At noon on June 25, a day earlier than his planned attack, Custer split his regiment into three battalions. Custer split his forces and sent three companies straight into the village. He then dispatched three companies to the south to cut off the Indian retreat, and he used five companies to attack the village from the north. Those tactical choices proved to be disastrous. By reacting and splitting his forces, Custer left its three main components unable to provide each other support.
As the Battle of the Little Bighorn unfolded, Custer and the entire 7th Cavalry fell victim to a series of surprises, not the least of which was the number of warriors that they encountered. Custer's intelligence group estimated Sitting Bull's force at fewer than 800 fighting men. The real number was over 2,000 Sioux and Cheyenne warriors. His intelligence also stated that the Indian warriors likely only had hand weapons and bows and arrows for their defenses. This was incorrect intelligence as well. Sitting Bull's soldiers had procured advanced repeating rifles and had a large contingent of cavalry as well.
General George Armstrong Custer made a strategic underestimation of the forces he was about to engage with at the battle of Little Big Horn and was outflanked and overrun by a force of over 10 to 1. The intelligence he had gathered was faulty and led his decision making to be flawed. A tactical judgement based on only partially validated data points and best estimates resulted in a folly that has transcended military history for over a century. His rush to respond to perceived actions of the enemy and to engage them in a tactical pursuit played directly into the hands of his adversaries and cost him and all his men their lives.
In Custer's case, he acted tactically based on partial data about the enemy, and he and his forces never had a true understanding of what they were facing. They did not know how large the enemy force was, they did not know about the technology they were facing, and they had little, if any, actual knowledge of what areas of the battlespace were defensible. They just reacted tactically to the stimuli they had received, and everything went to hell. Avoiding that same engagement model is what should be the focus of those who are engaged in cyber warfare.
The key to survival for any group is to adopt the concept of strategy first, and then tactics, not the other way around. Far too often, it is apparent that the organization that is outed as being breached or exploited has focused on implementing tactical controls that are adopted because of vendor marketing, not necessarily the realities of the space. It is rare that the leadership and the defenders can cite a singular statement that details the organizational strategy to secure the infrastructure. In physical warfare, that statement might have been "we will win the war on terror" or "dominate the air, control the battlespace." These statements sound simplistic, but that is the point of a good strategic statement. Clarity of vision and simplicity.
In cyber warfare, this must happen as well. An organizational strategic statement might be as simple as "we secure our users as we secure our infrastructure," or "we defend the edge and entity first." Those are not perfect, but they are simple, concise, and are easy to detail for the defenders who will engage with that strategy.
Once that strategy is shared and understood by the entirety of the defender group, the tactics that align and help to tactically make that strategy employable can be adopted. The strategy should be continually updated and adapted as the space and the tactics and tooling evolves, but there should always be a clear and useful strategy in place. And, contrary to Custer's example, the strategy should be based on a slow and careful response to actual enemy actions based on applied data points from a variety of validated sources. In cyber warfare, functional strategic defense is the correct approach, not half-baked tactical responses.
About the author
 Chase Cunningham
Chase Cunningham
Chase Cunningham focuses on helping senior technology executives with their plans to leverage comprehensive security controls and the use of a variety of standards, frameworks and tools to enable secure business operations. His work focuses on integrating security into operations, leveraging advanced security solutions, empowering operations through artificial intelligence and machine learning, and planning for future growth within secure systems.
Cunningham served as a director of cyber threat intelligence operations at Armor. He was the computer network exploitation lead for Telecommunication Systems and the chief of cyber analytics for Decisive Analytics. Cunningham is a retired U.S. Navy chief with more than 20 years' experience in cyber forensic and cyber analytic operations. He has past operations experience, stemming from time spent in work centers within the NSA, CIA, FBI and other government agencies. In those roles, he helped clients operationalize security controls, install and leverage encryption and analytic systems, and grow and optimize their security operations command systems and centers.
Chase holds a Ph.D. and M.S. in computer science from Colorado Technical University and a B.S. from American Military University focused on counterterrorism operations in cyberspace.








