Handbook of System Safety and Security
In this excerpt from chapter 10 of Handbook of System Safety and Security, editor Edward Griffor discusses cloud and mobile cloud architecture and security.

The following is an excerpt from Handbook of System Safety and Security from editor Edward Griffor and published by Syngress. This section from chapter 10 explores cloud and mobile security.
In this section we present a "big picture" description of the concept of Cloud computing and we define the layers and the Cloud services provided by each layer. We introduce the differences between the types of the Cloud computing and present features, business benefits, metrics, and the key platforms from the vendors. We discuss also Cloud caching, as a base for MCC, and the integration of Cyber-Physical systems (CPSs) into the Cloud. We conclude the section with guidance as best practices to define a robust Cloud architecture.
The Cloud computing paradigm is based on a layered architecture. Each layer offers a collection of services, which can be presented as a layered Cloud computing architecture illustrated in Fig. 10.2. On the bottom of the stack, Infrastructure as a Service (IaaS) refers to computing resources as a service. This
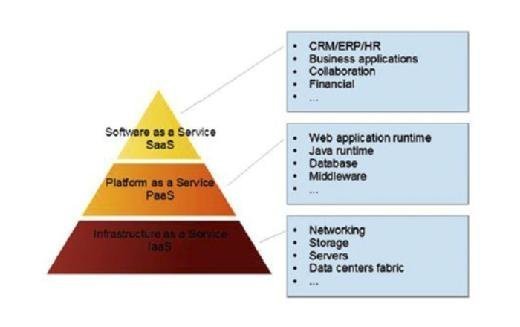
includes virtualized computers, processing power, reserved networking bandwidth, and storage services. IaaS services are offered by a variety of providers like Amazon AWS, Windows Azure, Google Compute Engine, Rackspace Open Cloud, and IBM SmartCloud Enterprise. Amazon Web Services, for example, offers a full range of computing and storage offerings in the IaaS layer. This offering includes on-demand instances such as virtual machines. Moreover it offers specialized services such as Cluster GPU instances, Amazon Elastic Map Reduce (EMR), high-performance SSDs on the storage side, and Elastic Block Storage (EBS). In addition the Amazon AWS IaaS solution offers infrastructure services such as archival storage called Amazon Glacier, in-memory caching services called ElastiCache, and both NoSQL and relational databases.
The middle layer of the stack is the Platform as a Service (PaaS) layer; this layer shows some similarities to IaaS. However, the PaaS includes required services, including the operating system needed for a particular application. The PaaS layer offers programming languages support for your application, server side technologies, and data storage options. The support for developer tools and applications integration is also very important. PaaS services are offered by a variety of providers like Engine Yard, Red Hat OpenShift, Google App Engine, Heroku, AppFog, Windows Azure Cloud Services, Amazon AWS, and Caspio. To illustrate the PaaS services, we give as example the services offered by Engine Yard. This provider is designed for web application developers using Ruby on Rails, PHP, and Node.js. Engine Yard allows developers to take advantage of Cloud computing without responsibility for the management operations in the infrastructure level. Engine Yard runs its PaaS platform on top of the Amazon Cloud and provides key operations tasks such as performing backups, load balancing, managing clusters, administering databases, and managing snapshots.
Handbook of System Safety and Security
Editor: Edward Griffor
Learn more about Handbook of System Safety and Security from publisher Syngress
At checkout, use discount code PBTY25 for 25% off this and other Elsevier titles
The top layer on the Cloud stack is Software as a Service (SaaS). At this level businesses delegate the hosting and the management of their applications to Cloud providers. The applications are available on-demand and typically paid for on a subscription basis. SaaS providers offer solutions including anywhere access, minimal administration, minimal maintenance, and improved communication.
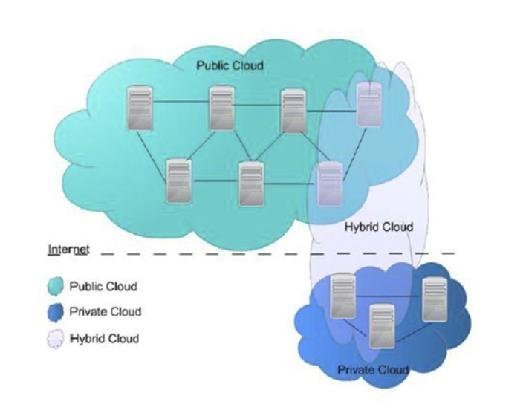
When we talk about the Cloud layers, they may be implemented in three different ways: as a public, private, or hybrid Cloud. An implementation on a public Cloud means that the complete computing infrastructure is located on an external Cloud computing provider that offers the Cloud service. In this type of Cloud the provider has the physical control over the infrastructure and the location of the resources allocated to the consumer. The advantages of the public Clouds are the usage of shared resources, they do excel mostly in performance. However, the drawback is vulnerability to various attacks. In the private Cloud, the infrastructure is used solely by one organization and those resources are not shared with any others. The organization acts at the same time as a Cloud producer and consumer. The resources may be local or remotely located. Some Cloud providers, such as a private Cloud externally hosted, offer solutions. To keep a physical control over the infrastructure, the organizations have an option of choosing an on-premise (or locally hosted) private Cloud as well which is more expensive. The advantages of the private Cloud reside in the usage of private network that introduces a higher level of security and control. The drawback is the cost of the infrastructure. Thus the cost reduction is minimal in such solution where the organization needs to invest in an on-premise Cloud infrastructure. In the hybrid Cloud the organization uses an environment that combines multiple public and private Cloud solutions. A typical usage of the hybrid Cloud is to use the public Cloud to interact with customers and keeps the data secured through an on-premise infrastructure in the private Cloud. However, this kind of usage introduces a drawback in the additional complexity of determining the distribution of applications across both a public and private Cloud.
The hybrid Cloud is used nowadays as a basis for the MCC. Mobile devices have more constraints on their processing power, battery life, and storage than regular computers. Cloud computing is used to provide an illusion of infinite computing resources for those devices. MCC is thus a platform combining the mobile devices and Cloud computing to create a new infrastructure and architecture for the development and the usage of the mobile applications. This architecture delegates the heavy lifting of computing-intensive tasks and storage of massive amounts of data to the Cloud infrastructure. Fig. 10.3 illustrates the architecture proposed for the MCC and its position in the general Cloud architecture.
Mobile devices are increasingly essential to everyday human life as the most effective and convenient communication tools. The unbounded time and place usage introduced by those devices allows mobile users to accumulate a rich experience of various services and applications. The execution of those services is not limited to the mobile device itself, more and more applications use nowadays remote servers via wireless networks
to interact with services. Architectures based on n-tier computing have become a powerful trend in the development of information technology as well as in commerce and industry fields on mobile computing. Such systems can accept any (finite) number of layers (or tiers). Presentation, application processing, and data management tiers function is physically separated from the others.
However, mobile devices have considerable hardware limitations. Mobile computing faces many challenges in attempting to provide the various applications living on a single device with limited resources such as battery, storage, and bandwidth. Communication challenges like mobility and security arise, too. Those challenges motivate the delegation of the resource-consuming application modules to remote servers using Cloud service platforms. Google offers one of the major solutions called AppEngine allowing developers who do not need to have any previous understanding or knowledge of Cloud technology infrastructure to deploy services and use the Cloud. This platform executes the deployed services and exposes them as a remote service. This approach is used to delegate massive computation pieces of mobile software to the Cloud infrastructure.
Indeed, the mobile Cloud is a hybrid Cloud that offers services for mobile devices and CPSs like smart cars and more
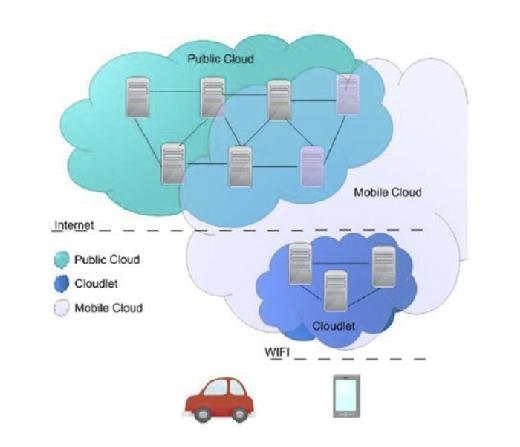
generally to smart devices in the transportation domain. Automobile makers are already in the process of migrating navigation services to the Cloud. This Cloud extends the processing capabilities for those devices using the Cloud paradigm. As illustrated in Fig. 10.4, the mobile Cloud uses a hybrid Cloud composed of a public Cloud and a private Cloud, sometimes referred to as a "Cloudlet." The Cloudlet is a private Cloud infrastructure directly accessible from the mobile devices and contains virtualization capabilities adapted to mobile systems. The mobile Cloud allows consumers to access the Cloudlet when possible -- if the Cloudlet is not available, the public Cloud is used to run the mobile applications.
Read an excerpt
Download the PDF of chapter 10 in full to learn more!
In the case of CPSs the mobile Cloud offers virtually unlimited resources to the "Cyber" part of the CPS. CPSs are systems that integrate decision/computation and the ability to sense or impact physical processes, where the measurement of physical processes may provide inputs to decisions or computations whose outputs may trigger actions that modify the energy and material flows that make up the physical world. The mobile Cloud offers a solution that extends these feedback loops to the Cloud in a way that can integrate remote computing infrastructure with the sensors and actuators. Cloudlets offer a way to have an on-premise infrastructure that is available even if the remote access to the public Cloud is unavailable. Such mechanisms are very important for CPSs as they may be part of systems that help the rescue efforts to organize evacuation after an earthquake of in other situation in environments qualified as hostile. Because they operate in hostile environments, CPSs need to be agnostic to the global network, for example, in case of emergency response systems. Using mobile Cloud services for CPS gives many benefits. In addition to the security introduced by using a private network, the continuity of services is clear benefit of such a solution. Moreover the Cloud offers a level of scalability that cannot be achieved by using embedded microcontrollers for the CPS. In the case of important updates of the CPSs, the Cloud offers also the possibility to remotely update all the cyber parts at a vastly reduced cost.
About the author:
Dr. Edward Griffor is the Associate Director for Cyber Physical Systems at the National Institute of Standards and Technology (NIST) in the US Department of Commerce. Prior to joining NIST in July of 2016, he was a Walter P. Chrysler Technical Fellow, one of the highest technical positions in the automotive industry and one that exists in multiple industry sectors, including transportation, aerospace, science, defense, energy and medical. He served as Chairman of the Chrysler Technology Council until 2015 and continues to serve as Chairman of The MIT Alliance, a professional association of scientists, engineers, and business experts trained at the Massachusetts Institute of Technology. Dr. Griffor completed doctoral studies in Mathematics at MIT and was awarded Habilitation in Mathematics and Electrical Engineering by the University of Oslo. He was named National Science Foundation/NATO Postdoctoral Fellow in Science and Engineering. Dr. Griffor was on the faculty of Uppsala University in Uppsala, Sweden from 1980 to 1997 and returned to the US to lead advanced research in Electrical Engineering in the automotive industry.







