
jayzynism - stock.adobe.com
Enterprise communication security a growing risk, priority
Enterprise Strategy Group's Dave Gruber discusses survey results on security threats related to the use of email and other communication and collaboration tools.
Most organizations support the use of various communication and collaboration tools, according to a 2023 survey of IT and cybersecurity professionals conducted by TechTarget's Enterprise Strategy Group (ESG). A combined total of 82% of the 490 respondents said their organization has formally sanctioned six or more tools for use by employees, with 35% approving 11 or more.
The many different tools being used increases the risk of cybersecurity attacks targeting email and other communication and collaboration channels. Sixteen percent of the survey respondents estimated that their organization faces attacks looking to exploit multiple channels on a daily basis, while 36% said such attacks occur weekly. Just 7% said they haven't been hit by any attacks of that sort.
As a result, enterprise communication security is becoming a bigger priority in organizations -- or it should be, said Dave Gruber, an analyst at ESG. Gruber co-authored a report on the survey titled "Challenges in Securing an Overabundance of Communication and Collaboration Tools" that ESG published in July 2023. In this Q&A, Gruber discusses some of the key survey findings and what they mean for IT and security teams in organizations.
Editor's note: The following was edited for length and clarity.
How big of a security risk do organizations face with the various enterprise communication and collaboration tools that are now being used in addition to email?
 Dave Gruber
Dave Gruber
Dave Gruber: These expanded channels can allow adversaries to evade some very good security controls that have already been implemented in the email channel. It provides a new path for adversaries to trick end users into sharing or clicking on phishing links or sharing credentials and other [information] while flying completely under the radar from IT and security teams, who have no visibility and no mechanism to put policies in place to control these additional channels.
Is email more secure then? Are you making a distinction between where email security is at and where security for the other channels is at?
Gruber: Yeah. Email is the center of the universe when people think about communication and collaboration -- at least, it still is today, as the foundation for business communication and collaboration. But certainly, over the last three years, as people moved into this hybrid work environment, it spawned work across many devices now.
From an earlier piece of research I did in mid-2022, we saw that, on average, people used five or six different devices every day as part of their business operations. We know that people are now using different types of devices, and what's familiar to them on those devices may be non-sanctioned tools. Our ability to extend the security controls we've been working so hard on in the email channel to these other communication and collaboration mechanisms is super important.
Taking email and the other communication and collaboration channels together, how seriously are organizations taking this and making it a security priority? Have they bought into it as a risk category on a widespread basis, or is it still an emerging one?
Gruber: For most, this is an emerging risk vector. While roughly 25% of organizations have recognized the importance of gaining control over this particular threat vector, there's another 50% who have eyes on this and are thinking about how to control this but haven't pulled the trigger and moved forward with any sort of security actions yet. I expect this to evolve fairly quickly over the next 6 to 18 or 24 months. I think if we were having this conversation again 18 to 24 months from now, we would see that two-thirds to three-quarters of organizations are all over this threat vector.
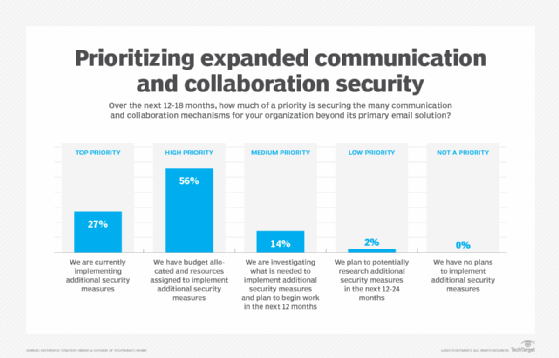
The survey data shows that IT teams have more responsibility for enterprise communication security than security teams do. Does that surprise you?
Gruber: One of the interesting findings in the research is that IT and security teams are often in a collaborative role when it comes to securing communication and collaboration channels. But IT, more often than not, ultimately owns responsibility for them as core IT infrastructure mechanisms. Security is a bit of an add-on to that. While the security teams are key advisors, even after all these years of using email security, we still see a more IT-slanted ownership of this function.
That said, as the threat landscape is made up of more advanced attack types that leverage these communication and collaboration channels as a tactic to carry out credential theft or some other early stage part of an attack structure, security teams are paying attention. That's why we see more security operations functions pulling in security telemetry from email systems. As they paint a picture of the attack chain, they can see various parts of it that involved email, whether it's in the body of the email for business email compromise type threats or when someone landed a successful phishing URL or a successful malware deployment through email and somehow evaded the email security controls.
Native security controls in email applications get more than 50% approval ratings on visibility, ease of use and integration with other security solutions -- but just barely over 50% in each case. Are those good numbers, relatively speaking, or not so good?
Gruber: They're pretty solid for the most part. They're consistent with what we've seen over time. Most IT and security practitioners are excited to see the investment that the key vendors have made in security controls, policy controls, [data loss prevention] controls and the rest of the capabilities now being built into cloud-delivered email solutions. But in the spirit of layered security, there's always gaps. Despite people being confident in what is provided natively, it doesn't necessarily mean that it's a 100% solution and it covers off every possible threat.
Anecdotally, in my conversations, people are generally excited about the level of progress that Microsoft and Google and others have made in the security capabilities that are now natively available. Many of them are being questioned: "Is that enough? Maybe I can stop investing in third-party controls?" But for most organizations, there's still a need for third-party controls.
Most respondents were extremely or mostly confident that their email security solution provider will address the challenges or gaps in its tools in the next 12 to 24 months. But 93% are implementing additional third-party controls or plan to use a managed service provider to fill the gaps in the meantime. How much of a hassle is that for organizations?
Gruber: This is a trend that we understand well in the industry -- that we'll always be chasing the adversary with new threat types and new tactics, techniques and procedures. Remember, their objective is to evade existing security controls at all costs. This is how the adversary wins. As defenders and people that provide solutions to help defend, it forces us to stay on par with or stay ahead of the adversary, which we don't have a great track record of in the security industry.
Given this ongoing trend, I expect that there will always be a need for somebody who's super nimble and can move quickly to add layered controls to strengthen [security measures] to a higher level than maybe the native controls will be able to keep up with. Native controls are going to keep getting better, and third parties are going to keep providing solutions that fill the gaps. Collectively it'll be up to security architects and security leaders to make the decision on how much is good enough.
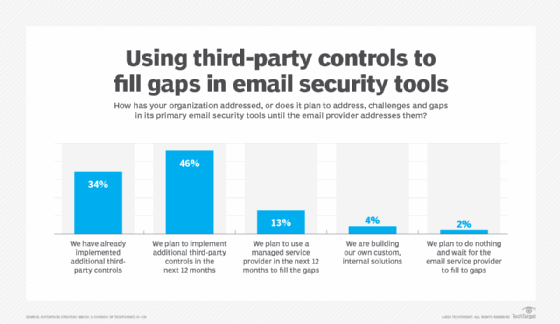
What are your key takeaways or recommendations for user organizations based on the survey results?
Gruber: I don't think any IT or security team will ever have total control over every aspect of communication and collaboration. As human communicators, we find every path we can to get our job done and to communicate with other people. As a result, you have to look at strategies that are as inclusive as possible and can be deployed at a low enough level that covers off, on a more horizontal basis, all these different channels. There are mechanisms emerging in the industry to help us do those things.
I also believe that a strategy of tool consolidation continues to make sense. Let's offer our end users the best possible integrated set of communication and collaboration capabilities we can -- that pares down the potential attack surface in this particular threat vector. But at the same time, continue to explore security solutions that are more horizontal and can provide the level of control and visibility we need to keep up with the adversary over time.
Read the full report
Enterprise Strategy Group subscribers can click here to access the research report on the survey covered in this Q&A.








