
tashatuvango - Fotolia
Editor's picks: Most pressing cybersecurity stories in 2019
As the year comes to an end, SearchSecurity takes a bird's-eye view of the sophisticated cyberthreat landscape and how it has changed over the past 12 months.
Some of the most popular coverage on SearchSecurity in 2019 highlighted current and emerging threats to organizations across verticals, while other articles offered insights to problems that have been plaguing enterprises for years, along with their well-known and new solutions.
Check out some of the most popular articles with readers this year that dig into the threat landscape of today and tomorrow, with expert advice on how to maneuver that balance.
Same security challenge, different day
Though it might have felt like cybersecurity stories in 2019 were dominated by discoveries of advanced and previously unknown attacks, existing threats to organizations remain formidable. To stay safe, security leaders must take stock of the most pressing and likely threats to their organizations.
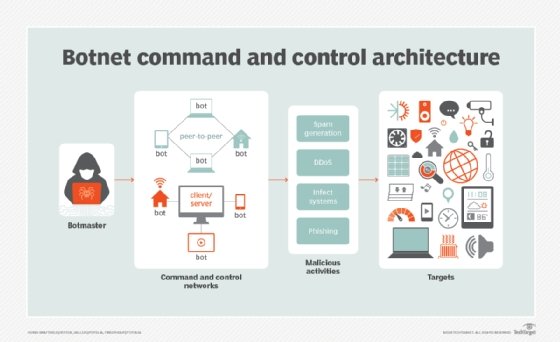
Not only do attack vectors vary, but there is a wide range of detection methods as well. Though organizations need to be ready for any risk, there are a few types of security incidents they must prioritize. Here, author Linda Rosencrance identifies insider threats, viruses, worms and botnets as a few of the top security incidents for IT teams in 2019.
Skills shortage: New solutions to age-old problems
The cybersecurity skills gap has been a well-known issue for ages -- and one that SearchSecurity readers were reading up on in 2019.
To fill the gap, cybersecurity researcher Bob Duhainy suggests seeking out individuals in other areas of IT -- specifically networking. In this article, he explains why networking knowledge is foundational to becoming a successful cybersecurity team member, and advises industry and government leaders on how to recruit the next generation of the security workforce.
The diversity of cyberthreats and threat actors calls for an equally diverse infosec team to mitigate them. But today, the tech pipeline often does not reflect the diversity of bad actors. Here, security leaders suggest widening the pool of candidates to attract people with nontraditional backgrounds.
While there's no magic solution for creating a more skilled workforce, the answer, argues expert Kevin Beaver, is not more technical knowledge. Common security challenges such as weak leadership, lack of financial support or a mediocre security culture within an organization are personnel and politics problems. Learn how your organization can benefit from focusing on the people problems.

Readers were also interested in learning new ways technology -- particularly automation -- can shrink the skills gap. Here, expert Mike Chapple explains how incorporating SOAR into security programs can help infosec pros work smarter, not harder.
Old threats, new methods (and attackees)
Cybersecurity stories in 2019 informed readers about ways old threats are still affecting businesses. The following editor's picks include stories about familiar threats with a new twist or method on the part of bad actors' intent on doing businesses harm.
Though brute-force threats, such as password spraying attacks, may not be considered sophisticated, that does not negate the damage that can result. In this Q&A, Justin Jett, director of audit and compliance at Plixer LLC., explains how to best bolster an organization's defense against password spraying attacks.
For such small devices, USBs can do enormous. In fact, researchers identified 29 different types of USB attacks in recent years. Here, read up on the most common types of USB attacks on industrial control systems and some recent examples, as well as how to prevent future USB attacks.
No, traditional phishing scams haven't gone away. Worse, there are newer, more sophisticated phishing campaigns that enterprises need to watch out for. Read the warning signs of one such campaign -- evasive spear phishing -- in this article, along with the months-long intelligence-gathering methods used by the bad actors employing it.
When it comes to motivated threat actors, even a well-protected organization's security measures will not stop hackers from trying to infiltrate. The third-party ecosystem is fertile ground for attackers to do so indirectly, through compromised vendor supply chains or remote contractors or employees. Here, Rick McElroy, head of security strategy at Carbon Black Inc., breaks down preventing island-hopping attacks.
Future security threats and mechanisms
Some of the top cybersecurity stories in 2019 centered on emerging mechanisms -- from quantum computers to zero trust -- and the threats they pose to infosec programs.
For example, quantum computers -- which some predict could come online as soon as 2020 -- could enable attackers to decrypt virtually all traditionally encrypted data. Learn how this technology is able to defeat traditional encryption, and why organizations must transition to new crypto algorithms to defend against quantum attacks.
Another challenge is IoT security. IoT often lacks a single "owner" because it is so fragmented. In many cases, the security responsibility falls in the lap of operational technology (OT) departments, making it difficult for IT to solve security-related IoT issues. In this article, Johna Till Johnson of Nemertes Research explains why it is vital that organizations implement an OT/IT convergence strategy. Read on for three steps to keeping IoT security challenges from falling through the cracks.
When 5G is deployed, it will revolutionize the speed and responsiveness of connected devices. However, the advancements in latency, capacity and speed open new avenues of potential manipulation and cyberattack -- especially distributed denial-of-service attacks. Learn how to prioritize DDoS protection in anticipation of 5G.
The zero-trust security model launched into popularity this year. SearchSecurity's primer on the what, why and how of zero trust was one of our top cybersecurity stories in 2019. While security used to be all about bad guys out, good guys in, the zero-trust approach assumes all users, devices and transactions are currently compromised. Explore why this approach has taken off and whether it would be a good a fit in your organization.







