
stock.adobe.com
Cybersecurity new normal needs change in process, CISOs say
As CISOs face an increasingly remote workforce, they need to confront past security mistakes, while adjusting to cybersecurity's new normal.
After months of working with an increasingly remote workforce due to the pandemic, CISOs are now forced to confront cybersecurity's new normal and decide how to modernize corporate data protection that may never be centralized again.
Cyberattacks rose as coronavirus quarantines began, and research predicted the increase in malicious activity will continue.
Increasing attacks pose complicated threats because the old security perimeter model based on firewalls and VPNs is obsolete, according to Leo Taddeo, CISO and president of Cyxtera Federal Group, a security infrastructure vendor focused on serving government agencies.
"Security staff and security tools do not have the same monitoring and incident response capabilities while operating remotely," Taddeo said. "Many organizations rely on a security operations center to coordinate teams of analysts and engineers, but many of these SOCs are shut down due to social distancing requirements."
The move to workforces going remote was abrupt and required many quick changes to how organizations were structured. Organizations struggled because they didn't have time to appropriately prepare processes and technology when the pandemic hit.
"A three- to five-year plan turned into five months in terms of virtualizing the workforce, distributing employees and trying to do so in as safe a way as possible," said Rich Mogull, CISO at DisruptOps, a cloud security automation management firm based in Kansas City, Mo. "That's a huge challenge from just the capacity level and getting laptops into people's hands, then making sure those devices are provisioned and secured appropriately."
Cleaning up security
Now that organizations have had more time to adjust to the new cybersecurity normal, the question becomes how to move forward. Experts said the main challenge was not only to design a new cybersecurity plan, but identifying how to fix mistakes from the past.
Candy Alexander, board president for Information Systems Security Association International, said CISOs should seize this opportunity to demonstrate the value of a business continuity plan.
"For organizations that were not prepared, the response to the COVID-19 shutdown was painful," Alexander said. "Use this as a life lesson to the business as to why it is important to factor in all scenarios when developing business continuity plans."
These plans also must be tested often so they can be distributed quickly and in an orderly manner, Alexander added.
In addition to developing new plans, visible management support is the key to success when new security programs are put in place, said Sherry Ryan, vice president and CISO at Juniper Networks, a networking vendor based in Sunnyvale, Calif.
"We need management to walk the talk and convey to employees the importance of protecting the information assets of the company, its employees and its customers," Ryan said. "Managing risks and making data protection a priority [need] to cascade from leadership during good and challenging times."
In addition to rethinking what security products are being used in an organization, Mogull said now is also the perfect time to right any wrongs that may be contributing to a toxic security culture.
Mogull suggested companies aim for a "fair and just" organizational culture rather than one that looks to place blame when there's a security flaw because systemic issues might be the ultimate cause.
Mogull pointed to shadow IT as an example of blame culture. In blame culture, the definition of shadow IT puts the onus on employees for using apps, services or software that are outside of what the company provides to complete their work rather than on IT for not providing the necessary tools an employee needs.
"In just culture, we try to find out why they did not feel they could do their job in the authorized way, and we solve that part of the problem," Mogull said.
Moving forward
The general consensus among experts is that software-defined perimeter (SDP) and zero-trust models are the best options moving forward in cybersecurity's new normal. These models' flexibility and adaptability can better meet the needs of a workforce that may never return to a traditional office.
Adding additional layers of complexity to an aging technology stack only adds significant costs and burdens to an already task-saturated workforce, according to Retired Brigadier General Gregory J. Touhill, the first U.S. federal CISO under President Obama and current president of AppGate Federal Group, a firm aimed at helping government agencies adopt zero-trust security models.
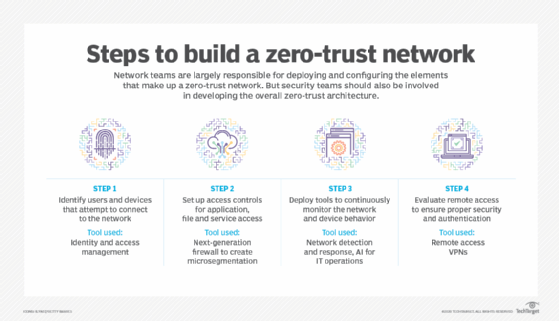
"Look to retire aging, expensive and increasingly vulnerable technologies, such as VPNs and network access control, and replacing them with modern, less expensive and more capable technologies, such as software-defined perimeters," he added. A transition to a remote workforce requires rethinking the entire traditional security infrastructure of an organization with cloud-native technologies.
As IaaS replaces data centers, security as a service replaces the back office and endpoints get more secure but with less direct control, the zero-trust model will only grow more attractive, Mogull said.
"The first place that I recommend companies focus on is dealing with their directories and identity management and getting a federated identity broker," Mogull said.
Once organizations have a plan in place to create the security culture and processes they want with the right tools, another challenge moving forward will be adapting to the lack of physical interaction.
"On a daily basis, employees talk to who they need to for their specific function to get their job done. This can cause attention to security practices to be put on the back burner, where employees will do things on their own and create future security challenges," said Peter Romano, CISO at eSentire, a cloud managed detection and response company. "For a CISO, this could tip the scales to be reactive and not proactive."




