Cyber Reconnaissance, Surveillance and Defense
In this excerpt of Cyber Reconnaissance, Surveillance and Defense, author Robert Shimonski describes commonly used mobile technology and how phone tracking works.

The following is an excerpt from Cyber Reconnaissance, Surveillance and Defense written by author Robert Shimonski and published by Syngress. This section from chapter four discusses commonly used mobile technology and how it can be used to track individuals.
Mobile Phones
Since this book is about digital surveillance and reconnaissance and how to defend against attacks, we will not get too deep into the architecture of the devices themselves; however, we will cover the specific phone types and the specific attacks leveraged against them. It's important to know how they are used to track your movements and how they can be used against you.
Why is spying on mobile devices so important to understand? If you are a victim, let's look at what could be at risk:
- View SMS messages -- Applications can record all SMS activities from the target phone. All sent and received messages can be recorded in an online account, even if the messages are deleted from the mobile phone.
- View call logs -- Each call can also be logged by the application that will also be uploaded to your online account. This provides the caller and the time of call.
- Track GPS location -- GPS tracking can provide your location at any time and be recorded to an online account.
- View photos and videos -- All photos and videos taken can be recorded and sent to an online account.
- View contact list -- A contact list of phone numbers can also be viewed and sent to an online account.
- Website URL logs -- This can show that websites are visited and sent to an online account.
- Call recording -- Your calls and messages can be recorded and retrieved and sent to an online account.
As you can see, with a simple application, your privacy is no longer secure and everything you say and do as well as where you go can be tracked.
Apple iPhone
Proprietary hardware, tightly controlled software, and a tightly controlled application store called iTunes makes up the Apple iPhone experience. This does not mean that you're safe from surveillance, far from it. It just means that it's less likely that malware will immediately infect your phone and allow you to be tracked.
As seen in Figure 4.1, the Apple iPhone is a handheld computer/phone that allows you to collaborate via applications, texts, e-mails, and phone conversations.
Tools and software (specifically Cydia) can be used to "crack" into the phone so that you can use it more freely; however, by doing so you open yourself up to more possibilities of being infected with malware. Regardless, many applications are available to load on the phone to track others beyond how they are already tracked via location services and tower acknowledgments.

Any mobile device can be tracked in numerous ways; however, those that are more commonly used (such as the iPhone) have more applications developed for that specific purpose.
Google Android
Open Source driven, Linux-based Google Android phones are widely used next to Apple iPhones. Having multiple hardware vendors and a variety of operating system types, Android is extremely flexible. Google Play allows for application download and installation and many applications are available for tracking and reconnaissance of the phone.
As seen in Figure 4.2, the Android platform is highly customizable and if you are a professional at mobile phone development, many options exist to place a tracker on the phone without your knowledge. Also subject to malware attacks, the mobile devices produced can be easily tracked.
Android (as well as iPhone) allows for an attacker to download applications from their application stores to use for tracking such as Spying Droid that covertly allows an attacker to use one Android device as a camera unit and another Android device to view live audio and video from the first device. If conveniently placed, it could provide covert surveillance for information gathering. Another app that can be downloaded is called Couple Tracker, which allows an attacker to spy on another person such as a spouse for the purposes to get their location, see their messages, or to verify their location.
Just like iPhone, you may need a higher privilege level on your phone that may require you to root it or use super user access.
Windows Phone
Similar to Apple and Google, Microsoft has a mobile device called Windows Phone. The marketplace is where you can get applications for your mobile device and among them are the same spy applications that are available for all other major phones. It is susceptible to the exact same surveillance risks associated with Apple and Google devices.
As seen in Figure 4.3, Windows Phone is Microsoft's line of mobile phone devices. Recently, Microsoft acquired Nokia who is the primary maker of Windows Phone hardware and the merger has rebranded these companies as Microsoft Mobile.
Although it's a different company, it's the same exact set of risks, problems, and concerns associated around privacy.
Blackberry
An older mobile device type that has significantly evolved is the Blackberry from RIM Research in Motion (RIM). As seen in Figure 4.4, the Blackberry offers many of the same features as does Apple, Google, and Microsoft; however, the Blackberry has predominately been used in the business world of enterprise companies and generally married to a Blackberry Enterprise Server that allows for advanced functionality. In the past few years, the Blackberry has undergone significant graphic user interface changes and enhancements in order to stay competitive with the other device offerings from Apple and others.
That being said, it too can be hacked and tracked just as easily as the others. Other devices exist and can be tracked as well. Following the same concepts as we covered, anything that works by providing an Internet protocol (IP) address, an assigned phone number, or an e-mail account can be easily tracked. Other device types and software packages allow for tracking ability. GPS devices, pads, and other mobile devices can be tracked. Microsoft's XBOX game console can not only be tracked but also can be viewed by an attacker inside your home through its sensor.
You should be concerned because what we just briefly covered is only half of the story. The other half is how the mobile devices you use give your location away without any application usage of any kind.
Phone Tracking
Phone tracking can be simply done by carrying your phone with you as you go about your day. So how is it done?
When a mobile device connects to a cell network, it registers with the carrier. When your mobile device is powered on, it emits a signal that is picked up by multiples towers. Your phone is triangulated by its distance from multiple towers. GPS receivers provide tracking information as well. Wireless signals can also be tracked in the same fashion. Shockingly, even if it is powered off, it may still be susceptible. In foreign countries, viruses (malware) have been distributed to keep the phone on enough to produce a signal for tracking.
As seen in Figure 4.5, when you carry your phone, it emits a signal that works with carrier cell towers and/or GPS satellites that provide you with the service, but also keep a log of your location within the system. This means that government agencies, law enforcement, or, if hacked, an attacker can also verify and validate your position at any time.
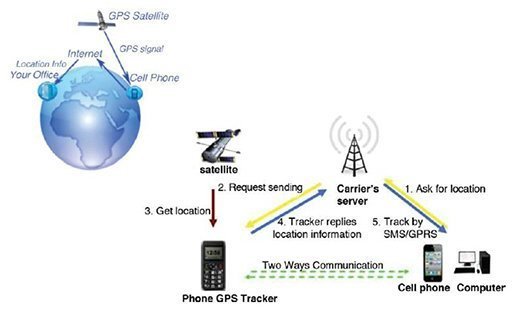
There are ways to also review these logs to trace your movements. So, if you travel from New York to New Jersey five days a week, your path to and from could be articulated from review logs at tower locations along that path. Of course, this is all deemed to be legal unless misused, but as we have learned, the government is collecting data to track the behaviors of suspected terrorists. They do this by collecting all data and then filtering on what they need. What seems to evade our private lives is that the information is in fact captured and available. It could be misused if an opportunity arose.
The Patriot Act
Immediately after the September 11 attack on the United States, the Congress passed the Patriot Act. The Patriot Act is an expansion of the surveillance laws allowing the government to spy on its citizens while reducing the oversight required to do so, fairly and with accountability. The bill was sent to vote without time for review, debate, or discussion and the threat of attacks was used to create a fear vote.
This act was created to expand surveillance laws by the government so that it had expanded record searching ability held by third parties (such as a telecom carrier), secret searches of private property without the need to inform the owner, and other expanded intelligence searches.
Malicious tracking
As we can see, tracking can be done without your knowledge and at many different levels. Your mobile device although helpful and a needed fixture of your person, is now a mobile tracking device that can be used to find you, evade your privacy at any moment, or as a tracking tool for another malicious user, stalker, attacker, or threat.
Cyber Reconnaissance, Surveillance and Defense
Author: Robert Shimonski
Learn more about Cyber Reconnaissance, Surveillance and Defense from publisher Syngress
At checkout, use discount code PBTY15 for 25%
Before we get into how to track a phone by example, it's important to understand the first steps to protecting yourself as much as possible. First, do not leave your phone unattended. Do not leave it unlocked. Do not leave it without a password. Use a strong password scheme. Make sure nobody is shoulder surfing you when you use your phone. In Chapter 8, mitigation strategies will be covered in detail; however, it's important to note here that by practicing simple security steps, such as those just listed, you significantly lessen the attack surface.
Tracking for Reconnaissance
Not all phone tracking is bad. Many applications exist today to help you find a lost or a stolen mobile device. Other tracking applications are used to keep tabs on children you are responsible for. They can be (and often are) used for wrongdoing. As mentioned earlier, applications exist such as Google Play's Track Your Wife by Tryfon to track the activities of a possible cheating spouse. In the last section of this chapter, we will discuss how this type of action is handled legally but before we do, let's review why it's done and specifically how it's done. Technology has expanded our ability to keep tabs on others we distrust. In a relationship where someone is suspected of wrongdoing, applications exist to validate this malicious behavior to those willing to track it. Those who track it, usually the other party in the relationship, may be able to ascertain facts that they had first suspected but could not prove.
A tool that can be (and is commonly) used is one that does not appear on the phone itself, if hidden, is MSpy. This is a great tracking tool that once installed will basically give you all of the information about anyone's mobile device use. Although this tool can be used for good, such as tracking a child by phone, it can also be used to secretly spy on someone without their knowledge. Some of the features included with MSpy are:
- Dashboard tool -- Overall dashboard used to get an overview of the tracked mobile device.
- Listen to incoming and outgoing calls -- This will allow you not only see incoming and outgoing calls but also listen to them.
- Run SMS tracking -- You can track all incoming and outgoing SMS text messages.
- Read e-mails -- This tool allows you to see and read all e-mails associated with the target device.
- Perform GPS tracking of the target device -- You can track the device via GPS and show locations via map.
- View photos and videos -- You can view all digital media photos and videos on the target device.
- See calendar events and contacts -- You can see all calendar-related information on the target device.
- Read chat and Instant Message (IM) conversations -- Review all chat and IM conversations specifically via text.
- Track browsing history -- You can see what websites are being used on the target device.
- View Skype messages -- You can track all Skype data on the target device.
- Monitor WhatsApp messages -- You can track all WhatsApp data on the target device.
You can also track Facebook data, Viber data, and much more. That being said, privacy is no longer an option to the unsuspecting user of the mobile device with a product such as MSpy configured on it. Again, it can also be used for good security reasons when you give a child a mobile device so that you can track usage as well as location. You can also restrict data being used on the target device with MSpy. However, when considering the surveillance that can be done especially without your knowledge, it could be worrisome to someone who does not know it is there.

As seen in Figure 4.6, we will begin to prepare an Apple iPhone for surveillance tracking. First, if you are attempting to track someone, you need to get access to the device itself. To do so, you can get access to the device in many ways. In this example, we will look at what many users are attempting to do as of the writing of this book -- track a significant other or spouse. First, get the device and if password protected, you can either crack the password, of shoulder surf to get it. There are many ways to easily bypass the password of an Apple iPhone. Once you do, you need to jailbreak the phone. Jailbreaking a phone is done quickly and easily, by downloading a package online that matches your iOS version, you can run the program, the phone will reboot and you will have full access to the phone.
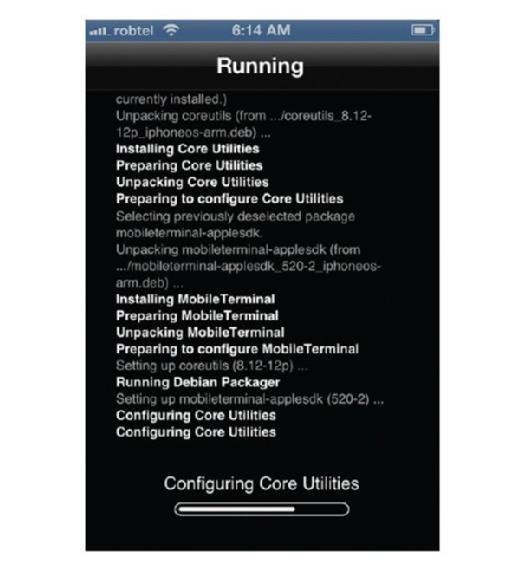
Once Cydia is installed (part of Jailbreaking routine), you can open it and install and configure MSpy. You will have to purchase a subscription for their services and they can assist you with this process as well. Once you get a subscription and register the phone, you can configure the phone for tracking.
As seen in Figure 4.7, installing MSpy is quick and painless. You download the package and it installs on your phone and will drop an icon on the iPhone home page; however, it will be removed once the registration is completed.
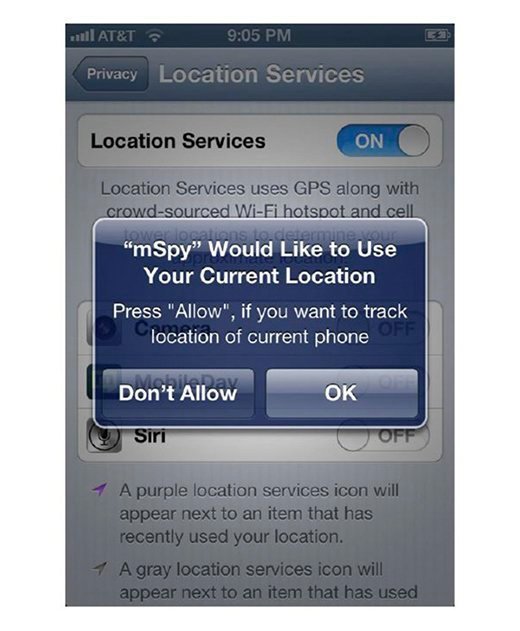
Once MSpy is installed and you have registered the service, you can begin to customize the mobile device so that it can be tracked. As seen in Figure 4.8, you will need to turn on location services for MSpy in order to physically track the phone.
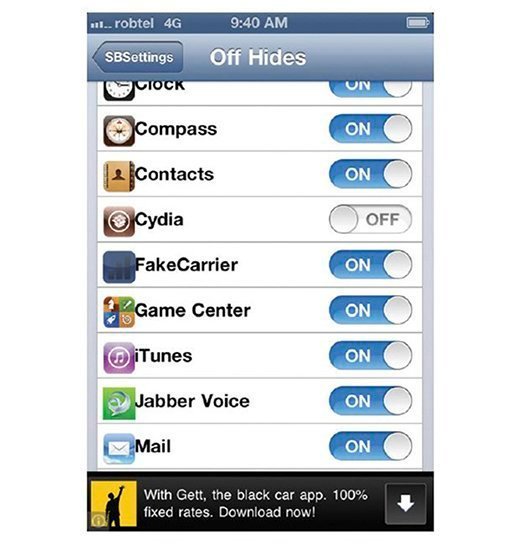
As seen in Figure 4.9, you can then hide the applications on the home page so whoever is using the device does not see the applications installed. This can be helpful so that once the victim uses the phone, they will not know that MSpy is installed on it. There is no visual existence so it can be hidden and kept secret.
Once MSpy is installed, you can access the online dashboard to view all of the data and track the phone.
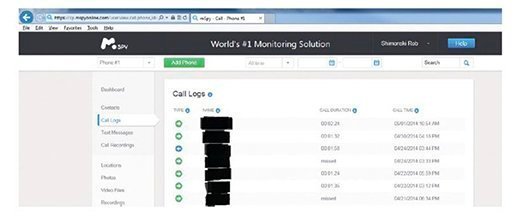
As seen in Figure 4.10, the dashboard can be used to view call logs (shown), text messages, listen to calls, track movement, and so on. As you can see, whoever is being tracked will not know and all interactions on the phone will be logged for viewing by the attacker.
It is possible that a very savvy user who knows how to go into the settings of their phone and nose around may stumble across the changes; however, it can be easily played off as an update from Apple as an example. It's rare that these changes are found unless the person who you are victimizing really know what to look for.
Lastly, for safety and possible furthering the attacks on the target phone, you should change the default password.
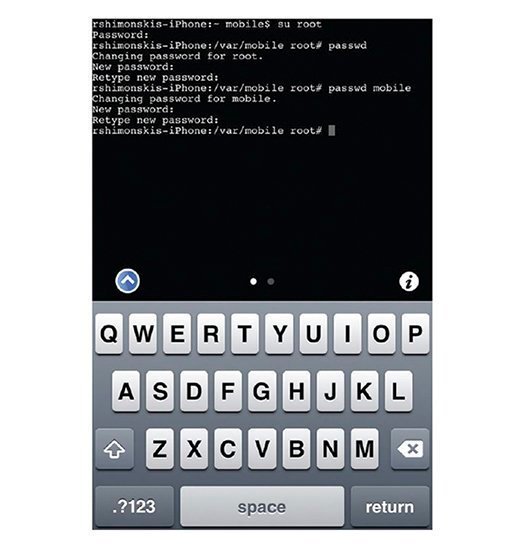
As seen in Figure 4.11, it is recommended that you change the default Apple password of Alpine as well as the default mobile password on your device. This can be done, obviously, for security, but it can also be used to configure an Secure Shell (SSH) tool for remote access into the device from your personal computer.
You can of course use other tools such as StealthGenie and Mobile Spy instead of MSpy; however, MSpy provided the features needed for this example.
Read an excerpt
Download the PDF of chapter four to learn more
As well, although we configure this tool for use on an Apple iPhone, you can also configure this system on mobile devices from Microsoft, Google, and others; however, the services are the same and the outcome is similar, your privacy has been evaded.
Location-Based Services
Embedded within the mobile phones technology is a service called LBS. This allows location data to assist with providing enhanced functionality. The applications are developed so that you do not have to input information; the information required is simply queried from your device.
With Apple's iPhone, the operating system (iOS) is deployed with a standard LBS functionality that allows applications to be able to track where you are and report it to the querying application. For example, as seen in Figure 4.12, Maps can use LBS to track your current location on a map for the purpose of making your life easier.
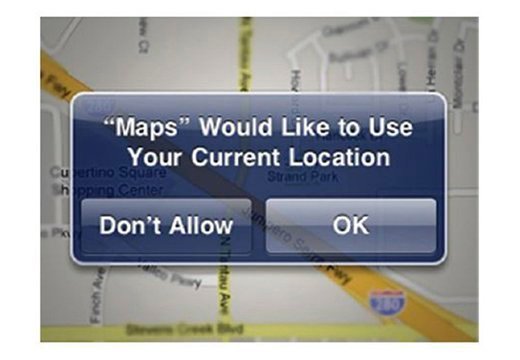
This functionality, however, evades your privacy. When you use LBS, Apple is collecting real-time tracking location information on its user base. Privacy policies released by Apple have said that the data is collected anonymously; however, how do you know this to be factual? And even if it was collected anonymously, it could be reconstructed to identify individuals. Why would Apple need this information in the first place? When considering the amount of questions that come up about protecting privacy, it's easier to opt out and simply not allow any application to do your thinking for you.
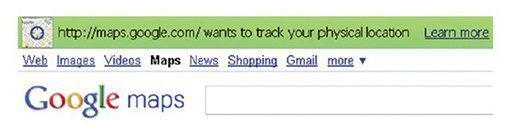
Other legal concerns are raised about LBS. For example, with LBS enabled, someone who gains access to your mobile device could possibly use the device to trace back your steps through your social media accounts that also use this technology to "map" your traveling habits. As seen in Figure 4.13, other applications such as Google Maps also attempt to track your location through LBS.
It should be clear that your privacy is affected when you choose to allow software to track you; it should not come as a surprise that this data and the data stored on the servers that collect the data could be used to track you and gather information about your habits.
Tracking a SIM
Each mobile device used as a phone will have a subscriber identity module (SIM) card installed that uniquely identifies the device. The SIM card (or chip) will store information and allows the device to be tracked. The SIM will send out a signal to the carrier network in order to be used on the carrier network, but can also be misused. For good purposes, you can track your phone if stolen or lost. However, a phone can also be tracked maliciously through the SIM. As seen in Figure 4.14, SIM chips are commonly used in most if not all mobile phone devices.

To track a SIM easily, report your device stolen and contact your service provider or carrier. They may be able to track your device for you. You can also install GPS software (covered in the next section) to pinpoint the devices location via satellite. Apple uses a program called MobileMe that is a cloud-based solution to back up your phone; however, it can also be used to track your phone if lost. You can also install a SIM tracker application on a phone so that the movements of the phone can be tracked both in real time and historically.
Global Positioning System and Geolocation
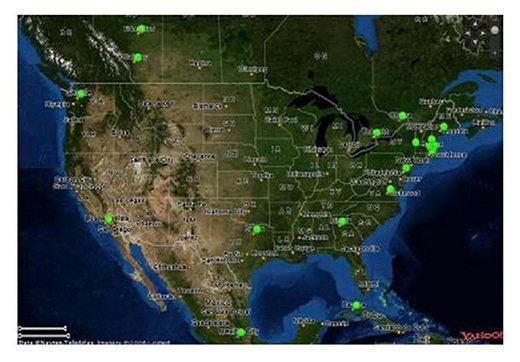
A GPS is used to pinpoint the physical device location directly or through triangulation. As discussed earlier in this chapter, a GPS can use a satellite or a series of satellites to track movement of a device. For good purposes, GPS can provide you with mapping data for trips as well as to find a lost device. However, for malicious purposes, GPS can show an attacker your exact position worldwide. Geolocation data can also be used to track device usage; however, it does so using information from other sources as well. TCP/IP can be used to assist with Geolocation. As seen in Figure 4.15, other applications such as Yahoo maps provide Geolocation data.
About the author:
Rob Shimonski (www.shimonski.com) is an experienced entrepreneur and an active participant in the business community. Rob is a best-selling author and editor with over 15 years experience developing, producing and distributing print media in the form of books, magazines and periodicals. To date, Rob has successfully created over 100 books that are currently in circulation. Rob has worked for countless companies to include CompTIA, Entrepreneur Magazine, Microsoft, McGraw Hill Education, Cisco, the National Security Agency and Digidesign. Rob has an extremely diverse background in the print media industry filling roles such as author, co-author, technical editor, copy editor and developmental editor. Since print media shifted to the digital domain, Rob has focused the past decade on developing all of the needed skills to produce professional audio and video media. An expert in Digital Audio Workstation (DAW) design and video production, Rob has created over 500 different media packages to include commercials for TV, online advertising clips, audio podcasts and much more. Rob started to train others while in the US Marine Corps. Since, Rob has held a NY State teaching certificate as well as multiple trainer roles in colleges and trade schools across the world.
http://store.elsevier.com/authorDetails.jsp?authorId=ELS_1032226 http://store.elsevier.com/authorDetails.jsp?authorId=ELS_1032226







