- Share this item with your network:
- Download
Information Security
- Editor's letterIndustries seek to improve third-party security risk controls
- Cover storyCloud-first? User and entity behavior analytics takes flight
- InfographicBeware of the gray hat hacker, survey warns
- FeatureCISOs face third-party risk management challenges
- ColumnKurt Huhn discusses the role of CISO in the Ocean State
- ColumnWhite hat Dave Kennedy on purple teaming, penetration testing

Sergey Nivens - Fotolia
Cloud-first? User and entity behavior analytics takes flight
The power and cost savings associated with software as a service are tempting companies to consider applications for security analytics both on premises and in the public cloud.
One of these things is not like the others.
The shift toward algorithms could lead to better information security. If only companies across industries could recognize patterns and do the math.
Organizations are investing in user and entity behavior analytics for on premises and cloud; endpoints are gaining intelligence; and UEBA integration with SIEM, data loss prevention and other security technologies continues to broaden the functionality of security operations centers.
"Learn normal, find weird," said David Swift, principal architect for security analytics at Securonix. The startup, based in Addison, Texas, offers UEBA, UEBA as a service and SIEM. Convergence of UEBA and SIEM has continued in recent years, but they serve distinct functions. "I agree with merging, but one is not going to replace the other," Swift said. "What you are really trying to do with user and entity behavior analytics is like Sesame Street: apple, apple, apple, orange…"
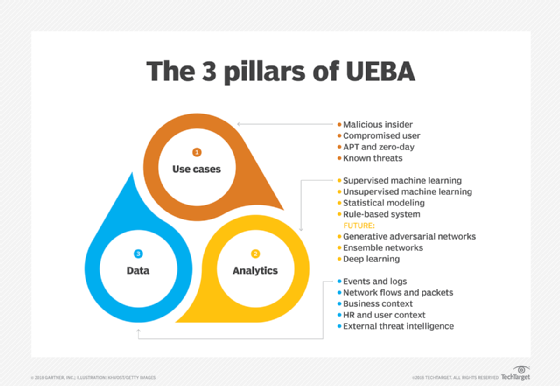
User and entity behavior analytics can develop baselines of activity and then use risk scores based on threat events, user and entity context, and peer analytics to alert security analysts of unusual activity.
CISOs and security managers have to worry about three control policies, as Swift sees it: "Did you do something known bad? Did you do something unknown bad? Did you do something weird? And that's when UEBA comes in -- the user did something that it has never done before and it's interesting."
Employees who search for jobs online aren't that unusual. However, if a "flight risk" starts to access a critical system with confidential data and then sends multiple emails to their personal account, they would get flagged. In addition to insider threats, user and entity behavior analytics can find privileged account misuse and aid in app and cloud security monitoring.
Developments in the cloud
"Within the last year, but it's really in the past six months, more and more companies are willing to actually do the processing of the analytics in the cloud," said Stephan Jou, the CTO of Interset Software Inc., a security analytics company in Ottawa. "Two or three years ago, this was a non-starter."
Previously, everything had to be processed on premises, behind the company's firewall. Now, large customers -- and many prospects -- are asking about software as a service and the public cloud.
Interset is one of the software companies backed by In-Q-Tel, a government-funded venture capitalist firm in Arlington, Va., that develops technology for the Central Intelligence Agency. It offers a cloud-hosted version of its on-premises technology, but the company is working on a cloud-optimized version of its analytics, in beta now with general availability expected by year's end.
"It's been interesting to architect the analytics to run well when it's completely offline, no connection to the internet at all, versus something that is optimized to run on top of Amazon, Azure or Google," Jou said.
Optimization for the cloud involves not only the analytics -- looking at access patterns, for example -- but performance and cost. "When you properly optimize analytics, the bill that you get from Amazon can be orders of magnitude smaller," Jou said. And fewer people are needed to manage a complex system; instead of running eight virtual machines, logical clusters show up inside your cloud dashboard as single line items.
To protect data privacy, any field that is sensitive is tokenized using a one-way hashing function before it passes through (leaves) the firewall. Security is largely handled by Amazon Web Services, Microsoft Azure and Google Cloud security teams.
More integration
Integration of user and entity behavior analytics with SIEM, data loss prevention, cloud access security brokers and other security technology shows no sign of slowing down. According to Gartner, "UEBA will cease to exist as a stand-alone market" by 2021. The previous forecast pegged it at 2022. Now analysts expect UEBA techniques to become "embedded" in 80% of the threat detection and incident response products by that year.
RSA Security, owned by Dell Technologies, announced in April 2018 its plans to acquire Israeli UEBA startup Fortscale. Terms of the deal were not disclosed. The company updated its RSA NetWitness SIEM and threat detection platform around the same time, with several modules aimed at security operation centers, including RSA NetWitness UEBA Essentials, RSA NetWitness Endpoint and RSA NetWitness Orchestrator.
Endpoint behavioral data, in general, is getting a closer examination. This data is critical for monitoring threats, such as privilege escalation, but most companies didn't really want another software agent running on their endpoints. That changed, however, with the emergence of endpoint detection and response. Collection of endpoint behavioral data, including that of third parties, is increasing, which benefits UEBA. "We can see people copy and paste data from documents into other documents," Jou said.
The endpoint agents are also starting to "play better with the operating system," according to Jou. Microsoft has made allowances within the operating system to detect fileless malware, for example.
Early adoption and lessons learned
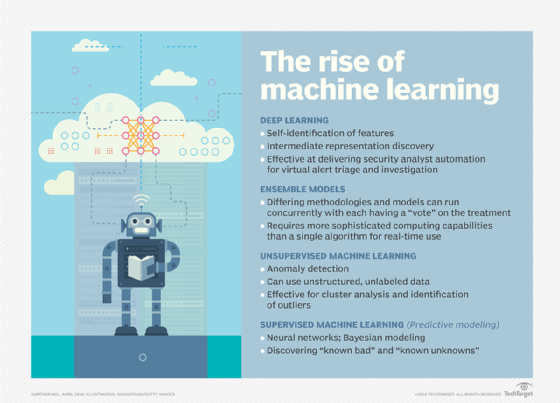
Detection techniques, according to Securonix's Swift, can include unsupervised machine learning; peer analysis; supervised learning, which uses training data sets; and robotic patterns to identify beaconing, command-and-control traffic, and user or system-generated behavior.
But data on UEBA's effectiveness against real-world threats is hard to find. Some companies adopt user and entity behavior analytics to meet regulations and compliance requirements to have security in place to detect anomalous behavior. Others purchase the software from an existing vendor. CISOs are advised to firm up their use cases and select a specific set of users to monitor before selecting these tools. A UEBA tool may need specific functionality to be effective -- for example, connecting to all of your required data sources (such as agents and syslogs). Sometimes, an existing SIEM can meet your needs.
Gartner found that the two prominent uses for user and entity behavior analytics technology are insider threats and external threats that are trying to infiltrate corporate networks. The analysts advised users to get clear answers to questions around data support for priority use cases and to require a proof-of-concept phase as part of the selection process.
"[A]dding custom or edge use cases can be an arduous process, requiring expertise such as data science and data analytics," stated the authors of Gartner's "Market Guide for User and Entity Behavior Analytics," published in April 2018.
Several companies, such as Gurucul and Interset, have started to introduce studio or drag-and-drop interfaces that help non-data scientists customize their machine learning algorithms. "As good as our algorithms are, there will always be the need for customized algorithms and customized use cases," Jou said. "Can what you are thinking of doing be described as a rule, or does it require modeling?" Companies that have data scientists can combine proprietary models with those from the vendor. Security data scientists in general understand how to code and usually prefer an API or language-driven way of interacting with the software.
It's also a good idea to run a pilot with actual data. "Simulated data does not work with these systems," Jou said. It's important to dig into how the system is maintained over time. If it is a fancy set of rules, you have to update it every month, because the business has changed. If it has machine learning, it will actually learn based on the data set.
What's coming next
In the future, Gartner expects user and entity behavior analytics systems to use analytical models based on "ensemble networks," "deep learning" and "generative adversarial networks."
Securonix released ResponseBot for its security analytics platform, SNYPR 6.2, in August at Black Hat. The machine learning technology is designed to offer suggestions to tier-one security operations center analysts so that they can address alerts related to complex threats based on past data collected from senior analysts.
Some of Interset's clients are already requesting deep learning, a subset of machine learning, for their current analytical models. Deep learning uses a neural network -- layers of algorithms, similar to the human brain -- to apply a logic structure to a problem. In active installations, the company is also focused on operational concerns, such as connecting results to automated systems to create tickets.
User and entity behavior analytics is data-driven and viewed by some like Securonix's Swift as the rebirth of data loss prevention. "It's about protecting my data," Swift said. "Move away from protecting machines and start protecting data -- stop looking for known good and start looking for the unknown. Those are the reasons that a CISO looks at UEBA. It's about the big-picture issues."























