CASB vs. CSPM vs. CWPP: Comparing cloud security tool types
Let's break down some cloud security alphabet soup. CASB, CSPM and CWPP overlap to an extent, but you'll want to pay close attention to how they accomplish different things.
To tap the flexibility of the cloud computing model, organizations continue to move operationally important workloads off premises. This shift to cloud makes safeguarding these assets a top priority.
Organizations need to be aware of potential vulnerabilities that could put their cloud environments at risk. The IBM-sponsored "Cost of a Data Breach Report 2023," conducted by Ponemon Institute, found that 82% of all reported security incidents were associated with data running in private, public or multiple clouds. Thirty-nine percent of all breaches traversed multiple clouds, according to the study, and carried a per-incident cost of $4.75 million.
While these risks and costs elevate cloud security as a corporate priority, the complexity associated with protecting workloads and infrastructure in virtual environments can be daunting. And the myriad acronyms don't make it easy to understand the functionality of the various options available to address cloud security risks.
Let's explore the similarities and differences of CASB vs. CSPM vs. CWPP.
CASB: Cloud access security broker
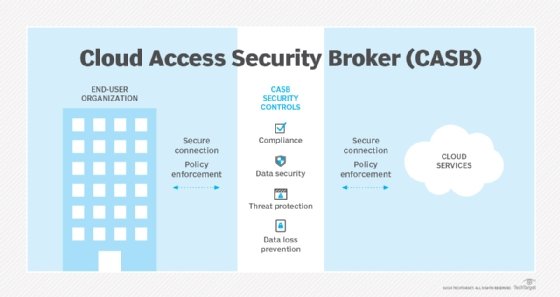
To protect on-premises access to cloud resources, organizations might choose to deploy a cloud access security broker (CASB). This tool enforces policies in the transactions between users accessing cloud assets and the cloud services to which they are connecting. CASBs provide a mechanism to protect interactions with SaaS and other cloud services beyond the organization's perimeter. CASB products deliver insights into cloud access and policy enforcement of these interactions.
CSPM: Cloud security posture management
Cloud security posture management (CSPM) products monitor cloud infrastructure, including on-demand compute and storage, and PaaS and SaaS implementations, looking for vulnerabilities and compliance problems that could expose cloud assets to risk.
CSPM tools offer custom rules built on various regulatory constructs, including Center for Internet Security, HIPAA, International Organization for Standardization, GDPR, NIST and PCI DSS. Because these tools can work across multi-cloud environments, they provide important protections. A CSPM product can also recommend fixes if it finds a vulnerability or misconfiguration.
CWPP: Cloud workload protection platform
A cloud workload protection platform (CWPP) offers ongoing threat management for cloud workloads.
CWPPs protect workloads from a range of vulnerabilities and risks, including configuration errors, DDoS attacks, data leakage, exfiltration and malware. Organizations use CWPPs to track and identify threats on an ongoing basis, looking at software configurations, network connections and end-user access privileges.
CWPPs also provide insights into and management of the infrastructure the workloads run on, including virtual and physical machines, as well as container and serverless workloads. CWPPs run security configuration checks and audits to verify compliance with regulatory requirements and corporate mandates.
CASB vs. CSPM vs. CWPP: Key differences and areas of overlap
CASBs, CSPMs and CWPPs have their own roles to play in cloud security. There is some overlap in functionality, but each focuses on securing specific aspects of cloud deployments.
CASB tools deliver an accurate perspective of end-user cloud interactions, both in terms of sanctioned and unsanctioned applications. This gives administrators insight into shadow IT activity and can help inform security policy creation and enforcement.
A CASB can discern if corporate data is accessed and disseminated in a secure manner, detect non-compliance and use data loss prevention controls to deflect breaches or accidental leakage. A business can use a CASB tool to detect malware and sandbox dangerous content.
A CASB will have some overlap in functionality with CSPM products, as both look for noncompliance.
CSPM tracks infrastructure within cloud environments and assesses potential issues based on a catalog of security risks. CSPM tools can make remediation recommendations, and some also apply automation to remediate certain types of events without manual involvement. Security engineers and IT administrators use CSPM particularly for hybrid and multi-cloud environments because the tools can work across infrastructure. A downside to using CSPM tools is that they capture a point in time, missing configuration and other minor changes that might create points of exposure over the longer term.
CWPPs provide a consolidated perspective on monitoring and identification of threats to cloud workloads. CWPPs give IT organizations insight into workload vulnerabilities across public, private and hybrid deployments. IT administrators use these insights to prioritize remediations and meet compliance requirements.
Other elements associated with cloud security include secure access service edge products, which merge security with WAN connectivity to protect access. Newer product categories are also emerging, such as cloud-native application protection platforms that combine aspects of CASBs, CWPPs and CSPMs to protect cloud-native applications and workloads.
Amy Larsen DeCarlo has covered the IT industry for more than 30 years, as a journalist, editor and analyst. As a principal analyst at GlobalData, she covers managed security and cloud services.






