- Share this item with your network:
- Download
Information Security
- FeatureStranger things: IoT security concerns extend CISOs' reach
- SurveyInsider threat report tracks annual cost of theft, carelessness
- FeatureBusiness email compromise moves closer to advanced threats
- OpinionCybercrime study: Growing economic ecosystem spells trouble
- OpinionWalmart's Jerry Geisler on the CISO position, retail challenges
- OpinionQ&A: Why data security controls are a hard problem to solve

Fotolia
Business email compromise moves closer to advanced threats
The sophisticated techniques used in BEC scams differ from other email fraud in the steps taken to construct the criminal campaign. Here's how to stop these APT-style attacks.
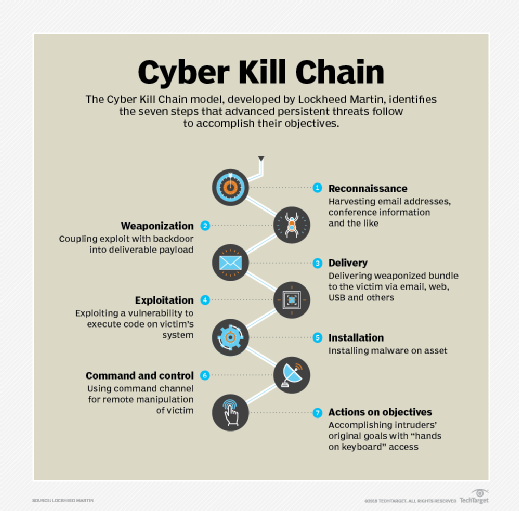
Business email compromise is on the rise and costing companies billions of dollars. In 2017, the FBI Internet Crime Center started to track BEC and email account compromise as a "single crime type" because of the similarities of the techniques. Business email compromise distinguishes itself from other email fraud by the steps, time and effort taken to construct the criminal campaign. These steps closely follow the kill chain framework used by advanced persistent threats, and that is what makes BEC dangerous.
It has been known for years that, no matter how well an enterprise is protected, security professionals cannot guarantee that the network will not be breached by advanced adversaries. Russia's and China's state-sponsored cyberespionage groups are just too well funded and resourced. If nation-state threat actors want to get into your network, and time and money are not a concern, it is safe to say they could.
Advanced persistent threats (APTs) are well-known for using the seven steps spelled out in Lockheed Martin's Cyber Kill Chain. Nation-state actors study a company by conducting extensive research on how it is structured and staffed to identify targets. They often use an email vector to drop malware or drive-by links on a network. Then, depending on the value of the target, they burn a zero-day -- or near zero-day -- vulnerability or a brand-new command-and-control site to ensure any proactive defense lacks indicators of compromise to alert the network security team. Scary stuff if you are charged with protecting that network.
APT attacks tend to work. And it is because they work that more sophisticated groups in the cybercriminal world have taken notice and aligned their tactics, techniques and procedures with those traditionally found in APT attacks.
In a February report, "Economic Impact of Cybercrime -- No Slowing Down," the Center for Strategic and International Studies, in partnership with McAfee, called the proliferation of sophisticated cybercrime an economic burden worldwide, estimated at $600 billion in losses annually. Many companies have been victims of cyberfraud, but most do not report it.
BEC scams
Although few companies publicly admit they were defrauded, sometimes the consequences of a successful attack cannot be hidden. Aerospace and defense company FACC AG, which sells equipment to Airbus and Boeing, lost $54 million in 2016 to a BEC scam. In an incident known as a "fake president" fraud, hackers used email to impersonate the CEO and initiate a wire transfer to an account controlled by cybercriminals. The CEO and the CFO of the Austrian company were fired by the board of directors as a direct result of the cyberfraud.
SecureWorks, a managed security service provider based in Atlanta, noticed unusual email activity in 2017. Researchers at the company issued a report earlier this year pointing to a BEC scam targeting the maritime shipping industry. The threat actors, dubbed Gold Galleon, out of Nigeria, used fake payment requests to steal close to $4 million. The attacks at multiple companies used some combination of social engineering and malware.
In 2017, the FBI issued a PSA alert on BEC as a financial cyberthreat, stating that attacks worldwide resulted in losses of $5.3 billion from 40,203 domestic and international incidents reported to the Internet Crime Center and other sources between October 2013 and December 2016. In May 2018, the FBI released its "2017 Internet Crime Report," which noted that BEC and email account compromise complaints reached 15,690 in 2017, representing $676 million in losses. The FBI estimated that business email compromise has cost American companies millions of dollars in its various schemes since 2013, when the Internet Crime Center first tracked spear phishing, identity theft, email spoofing and malware that led to financial cyberfraud.
Business email compromise does not mean the company's email services have been compromised -- the attack vector is via email directed at business operations. However, if your company's email is an open source email service like Google mail, then it can lack advanced protections available at a premium.
BEC's goal is to get people in an organization to take action on a request from a "senior employee" or "supplier" to wire money to a fraudulent account. These campaigns often start during tax time or at the end of the fiscal year so that cybercriminals can take advantage of pressured financial teams. To pull this off takes detailed understanding of how an organization is structured. These criminal groups use lawyers, linguists with native language training, private investigators and research analysts to gain insight into the targeted organization. They also use spear phishing and malware to access the targeted organization's internal networks and billing systems to figure out how the payment protocols work.
Here is a common script for a BEC event: The accounts payable (AP) manager in Acme Widget Corp. (AW) is getting clobbered by end-of-year work. AW is a publicly traded company worth several billion in revenue. It has an international division. In the rush to close out the fiscal year expenses, the manager has authorized overtime to the staff. In the middle of this crush, she receives an email directly from the general manager of the division she works to support. It is not unusual for her to get these email messages. The general manager is requesting that the AP manager pay an invoice to a law firm that has supported AW in the past. The invoice is for some merger and acquisition (M&A) consulting. The AP manager has no direct knowledge of any M&A work, but that is also not unusual because this type of activity is confidential in the early stages.
She takes a look at the invoice. It is payable to a bank in Hong Kong. The email appears to be from Patty Smith <[email protected]>, which is correct. As she is considering the invoice, another email appears in her inbox from the general manager expressing some urgency to pay the invoice. The AP manager, busy already, sends the invoice to the payment team and authorizes the payment, with a note to expedite it. She replies to the email that the payment is scheduled for the next day.
Later in the week, the AP manager sees Patty in the office and lets her know the M&A invoice has been paid. Patty has no idea what she is talking about. A quick phone call to the outside law firm confirms the invoice, which appeared legitimate, is not from the firm. The money was wire transferred two days ago.
The security team from AW analyzes the email, examines the extended headers and sees the mail is from [email protected]. But the "address" is Patty Smith <[email protected]> so it is displaying the correct email syntax as part of the name, tricking the AP manager into believing it was legitimate. Some research and a few phone calls to the Hong Kong police show that the money is no longer at the bank. The bank account was closed shortly after the money was wired. To discover where the money went would require the Hong Kong police to investigate the crime, which they will not do because the amount of loss is less than US$1 million. The money is gone.
Unknown targets
For this campaign to work, the criminal organization will have to pick target companies. The FBI reported that it is a mystery how targets are selected -- large and small companies in every U.S. state and more than 131 countries have experienced BEC attempts. The cybercriminals have to conduct a lot of research on the target, primarily via LinkedIn and other social media sites. They have to find the accounts payable organization and then a decision-maker who could authorize a financial wire transfer. LinkedIn's search tools help make this an easy task. While this is happening, the cybercriminals have to construct the invoices with the electronic payment instructions to transfer money to a bank account that they control. This process suggests there are people working as part of the conspiracy in the jurisdictions where the banks are located. These "money mules" are paid to open a legitimate bank account and then forward monies onto another bank when instructed, in return for a payment of some kind. Mules are recruited without ever meeting the criminals, who often hire mules using "work from home" schemes.
This is not a "Nigerian prince" email scheme. The email messages are put together professionally with the expected syntax and grammar of a native speaker. The invoices look just like the real thing, and the inclusion of the purported sender's real email in the name line suggest some planning. The email messages are not blasted into the company. They are sent to a specific number of targeted people. This means the campaign requires resources to monitor the bank accounts and replies to the email. These multinational criminal groups are spending resources to mount the attacks. So how do you defend yourself from business email compromise?
Unlike APT attacks, where organizations use threat intelligence as the main defense, there is a lack of actionable threat intelligence for advanced criminal enterprises. Information sharing and analysis centers established by the U.S. government (for critical infrastructure) and by private industry groups focus on APT defense against nation-states, not criminal threats.
Without actionable threat intelligence, it is very difficult to mount an effective defense against BEC attacks. Technical controls are hit or miss. Filters can flag email sent "on behalf of" and with doppelganger domains. The FBI recommends that companies set up rules in intrusion detection systems to flag email messages whose extension varies slightly from the company's as well as ones with a "reply" address that differs from the sender's "from" address. Organizations should also use color coding to differentiate between internal and external email. But because the email messages are not sent to large groups, filters may not catch these attacks. Email often lands on the employee's desktop, and inevitably, someone will be social engineered into sending the invoice.
The key to fighting BEC is training and education. This strategy has proven to be the most effective means of stopping these attacks. The targets of BEC are almost always someone who can send a wire transfer, so training should be supported by, and directed from, the finance director, CFO or other senior leader to the staff. The CISO's primary role is to identify the risk and vector and to provide the background on BEC to the finance teams. The security training should alert executives and staff to the warning signs of typical BEC email and how to prevent these attacks:
- Never use email as the sole source for invoice approval. Establish an awareness campaign to educate the AP team on a multistep authorization process.
- Be leery of email requests from C-level executives requiring an urgent payment outside of AP processes.
- Look at the wiring details of invoices that accompany email messages for payment. If the bank is in Hong Kong, China or Eastern Europe, proceed with caution; BEC uses banks in countries with limited regulation.
- Train your finance team on BEC. Establish an accounts payable process that requires some diligence to confirm invoices.
Most companies have established payment policies and procedures that involve purchase orders and approvals, but many organizations forgo this authorization process for senior staff. To prevent business email compromise, CISOs should work with CFOs and the finance team -- bookkeepers, accountants and controllers -- to establish a business process that does not permit authorization of requested payments based on an email exchange alone. The FBI recommends voice-to-voice and face-to-face communications to authorize payments, and two-factor authentication for any changes in vendor payment locations. Annual awareness training on business email compromise should be mandatory for all executives and accounts payable staff to keep the threat of cyberfraud top of mind.
Next Steps
COVID, gift cards and phony acquisitions top BEC attack trends
Related Resources
- Kaspersky Container Security –Kaspersky
- 7 cybersecurity trends for 2026 –SHI International
- Reimagining Security for the AI Era –Cisco
- Risk-Based IT Compliance: The Case for Business-Driven Cyber Risk Quantification –Talk
Dig Deeper on Threats and vulnerabilities
-
![]()
‘Dual-channel’ attacks are the new face of BEC in 2026
By: Alex Scroxton
-
![]()
How to prevent vendor email compromise attacks
By: Amanda Scheldt
-
![]()
Meet the professional BEC op that targeted Microsoft 365 users for years
By: Alex Scroxton
-
![]()
Business Email Compromise (BEC) Attacks Continue to Increase in Healthcare
By: Jill Hughes



















