12 types of wireless network attacks and how to prevent them
From packet sniffing and rogue access points to spoofing attacks and encryption cracking, learn about common wireless network attacks and how to prevent them.
It's time to get serious about wireless network security.
The temptation is real. Most of us have at least considered using an open wireless network when we're traveling or at a local store or restaurant, despite knowing that "open wireless network" means "not secured." We know the risks, but we consider connecting -- or connect -- nonetheless. The risks of being attacked may seem hypothetical, but they're real.
Network, IT and security admins involved in managing wireless networks have to secure those networks to protect the users, devices and services using them. One of the best ways to do this is to make users aware of the different types of wireless network attacks they may encounter, as well as putting the appropriate safeguards in place.
Let's take a look at the most common forms of wireless network attacks and specific types within each category, and then talk about how to prevent them.
3 categories of wireless network attacks
Wireless network attacks can be bucketed into three categories: passive attacks, active attacks and attacks against wireless network components:
- Passive attacks take place when an attacker is within range of a wireless network and can monitor wireless communications. The most common passive attack is packet sniffing. Passive attacks generally can't be detected because attackers are only listening and not transmitting.
- Active attacks often involve attackers deploying rogue wireless access points -- for example, setting up an open network named "Free Wi-Fi" -- in hopes that people connect to it. Active attacks are often used to perform man-in-the-middle (MitM) attacks because they can intercept, monitor and alter communications passing through them.
- Attacks against wireless network components involve attackers targeting individual components of a network, such as exploiting an access point's unpatched firmware or using an access point's default password to gain unauthorized administrative access to it.
12 common types of wireless network attacks
Each category can be broken down into more specific attacks. The most common types of wireless network attacks are the following:
- packet sniffing
- rogue access points
- Wi-Fi phishing and evil twins
- spoofing attacks
- encryption cracking
- MitM attacks
- DoS attacks
- Wi-Fi jamming
- war driving attacks
- war shipping attacks
- theft and tampering
- default passwords and service set identifiers (SSIDs)
1. Packet sniffing
Packet sniffing is the act of gaining access to raw network traffic. Packet sniffers, such as Wireshark, detect, monitor and gather network packets. While packet sniffing is a legitimate activity, packet sniffers can also be used by attackers to spy on network traffic.
2. Rogue access points
A rogue access point is any unauthorized access point connected to a network. If an attacker successfully places a rogue access point, the attacker can then access the network it connects to.
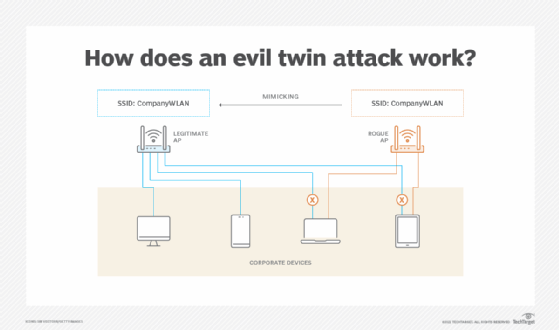
3. Wi-Fi phishing and evil twins
Wi-Fi phishing is when malicious actors create access points that imitate legitimate Wi-Fi access points.
An evil twin is a type of rogue access point used for Wi-Fi phishing. It advertises itself as an existing, authorized access point. It uses the SSID of an authorized access point to trick users into connecting to it. Sometimes, attackers disable the authorized access point to subvert the entire network. Even if the authorized access point isn't disabled, the evil twin still often gets access to some network traffic.
4. Spoofing attacks
Spoofing attacks involve malicious actors pretending to be legitimate users or services. Types of spoofing attacks include the following:
- MAC address spoofing happens when attackers detect network adapter MAC addresses on authorized devices and attempt to start new connections impersonating the authorized devices.
- Frame spoofing, also known as frame injection, occurs when attackers send malicious frames that appear to be from legitimate senders.
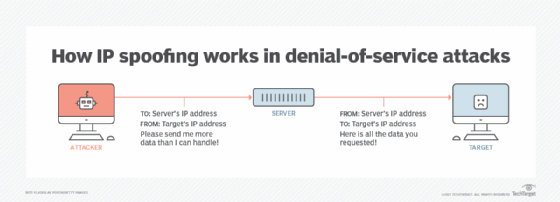
- IP spoofing takes place when attackers use modified IP packets to hide where the packets originate.
- Data replay occurs when attackers capture wireless data transmission, modify the transmission and resend the modified transmission to a target system.
- Authentication replay happens when attackers capture authentication exchanges between users and reuse those exchange in attacks.
5. Encryption cracking -- WEP/WPA attacks
Many older, outdated security protocols, including Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA), are vulnerable to attack. WEP, introduced in the 1990s, encrypts data transmitted over a LAN. It is flawed, however, and should never be used in enterprise networks.
WPA, introduced in 2003, was created to be more effective than WEP. It uses stronger encryption and better authentication than WEP. WPA is also vulnerable to attacks, however, and should also never be used. WPA2 was introduced in 2004 to formally replace WEP. It includes AES encryption. WPA3, introduced in 2018, offers even stronger encryption than WPA2.
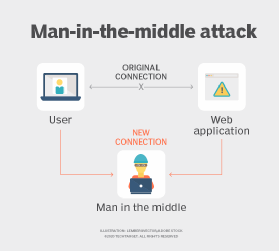
6. MitM attacks
MitM attacks occur when cybercriminals eavesdrop on communications between two parties -- for example, two users communicating with each other or a user communicating with an application or service. Attackers can intercept sensitive information and relay information by pretending to be one of the legitimate parties.
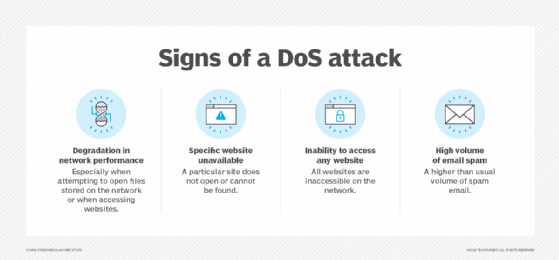
7. DoS attacks
DoS attacks occur when malicious actors flood a network with traffic, thus overwhelming the network and making it impossible for legitimate users to access it.
8. Wi-Fi jamming
Like DoS attacks, Wi-Fi jamming attacks overwhelm a network and prevent legitimate users from connecting to it. An example of a Wi-Fi jamming attack is flooding access points to "jam" the connection.
9. War driving attacks
War driving occurs when attackers search for open or vulnerable wireless networks to exploit. Also known as access point mapping, attacks involve nefarious actors driving around with wireless devices -- usually, computers or mobile devices -- searching for open networks to connect to.
10. War shipping attacks
War shipping attacks involve attackers sending physical spying devices to companies, which, once within the company's building, connect to the target network to exfiltrate data. An example of this attack could be an attacker sending a wireless-enabled device to a mailroom. Once it arrives, the device scans for networks to connect to and attack.
11. Theft and tampering
Attackers can conduct physical attacks on wireless networks by stealing or damaging wireless access points and routers. These attacks not only prevent users from accessing networks and cause network downtime -- and, therefore, business disruption and potential revenue loss -- but also can be costly for the companies replacing the stolen or damaged devices.
12. Default passwords and SSIDs
Corporate networks should never use default passwords and SSIDs. Employees who work from home should also be advised to change default passwords and SSIDs. Default SSIDs enable attackers to find out which router an employee is using and, in turn, find potential vulnerabilities specific to that router. Default and manufacturer-provided passwords, which are often printed on the side of consumer routers, should be changed to prevent unauthorized users from seeing and using them. Password security best practices -- such as not using easy-to-guess passwords -- should be followed.
How to safeguard wireless networks and network usage
Home and workplace routers should be protected with the following basic steps:
- Use WPA3, the latest standard for wireless network security, if your access points and client devices support it. WPA2 is still a decent alternative, but move to WPA3 as support for it increases.
- Set a unique, hard-to-guess password for each wireless network.
- Keep all network components up to date, patched and properly configured to minimize their exploitable vulnerabilities.
- Minimize or prohibit remote access to your access points, and always change default access point passwords to unique, hard-to-guess ones. This prevents arbitrary attackers from reaching your access points over the internet and easily gaining control over them.
In addition to those safeguards, implement the following security controls for corporate networks:
- Separate the wireless networks from other networks. This is most often done by using firewalls, virtual LANs or other network boundary-enforcing technologies to separate networks and enforce security policies that restrict traffic going to and from each network.
- Deploy wireless-specific security technologies. Examples of these include wireless intrusion prevention systems, which look for attacks and suspicious activity, and wireless controllers, which manage and monitor access points throughout an enterprise.
Last but not least, tell employees about wireless network attacks and security best practices during regularly scheduled security awareness trainings. Advise them to avoid using open networks. It's often much more secure to set up a hotspot for your laptop through your smartphone -- with a unique, hard-to-guess password for hotspot access -- than it is to use an open Wi-Fi network.






