Identity and access management tools and features for 2025
The IAM tool marketplace is complex and ever-changing. Learn about key features and how to discern what your organization needs before approaching potential providers.
Identity and access management is taking on an important role as organizations move more and more critical processes to the cloud. This, plus adoption of a zero-trust approach to security, has increased the need for strong authentication and authorization.
In response, the security marketplace provides a variety of identity and access management (IAM) tools and services. The trick is identifying the features your organization needs.
A sampling of the IAM tool market
First, let's take a quick look at some of the growing IAM market's major players, highlighting their more noteworthy features. In alphabetical order, here are some of the major vendors you're likely to encounter:
CyberArk
Historically, CyberArk was best known for its privileged access management (PAM) capabilities and secrets management. In 2017, the vendor acquired Conjur to help extend PAM capabilities into cloud environments. The 2020 purchase of Idaptive expanded CyberArk's capabilities in single sign-on (SSO), multifactor authentication (MFA) and identity lifecycle management, and also supplemented those capabilities with AI.
Entrust
Long known for its strong focus on encryption, authentication and digital certificates, Entrust offers MFA, SSO, federation and PAM. Entrust has been investing heavily in IAM the past few years, purchasing WorldReach Software -- an identity vendor focused on immigration -- in 2021 and AI identity-fraud player Onfido in 2024.
IBM
IBM's history in the identity space dates to before the firm's acquisition of Tivoli in 1996. In addition to supporting SSO and MFA use cases, IBM provides strong governance and PAM capabilities. IBM Security Verify, launched in 2018, includes AI-driven risk analysis, aiding in threat detection.
Microsoft
Microsoft IAM products are primarily offered through Entra ID -- formerly Azure Active Directory -- and include SSO, MFA, conditional access and identity governance.
Okta
Okta, a longstanding player in IAM, is known for its flexibility, integration, and SSO and MFA capabilities. The vendor is also recognized for its efforts to help reduce dependence on passwords and its easy-to-navigate UI. While Okta has a strong presence with SaaS applications, Okta Secure Gateway helps extend the vendor's SSO capabilities to on-premises applications. In 2021, Okta bought Auth0, a vendor with strong customer-focused identity management offerings, bolstering its capabilities in customer-facing offerings.
OneLogin by One Identity
OneLogin -- a long-running, well-known member of the IAM space -- was purchased in 2021 by IAM vendor One Identity. Product features include identity governance, access management, PAM and the ability to help automate and manage Entra (Active Directory). AI-backed threat management promises to help identify and address IAM risks.
Ping Identity
Ping Identity, now owned by private equity firm Thoma Bravo, has a long history in the IAM space. The vendor specializes in SSO, MFA and federation. It's a strong player across cloud, hybrid and on-premises environments. One notable offering is PingOne DaVinci, a low-code orchestration product resulting from Ping Identity's purchase of Singular Key in late 2021.
SailPoint Technologies
SailPoint Technologies, another vendor owned by Thoma Bravo, is a strong player in identity governance and orchestration, especially in automated provisioning and deprovisioning. They also offer machine identity, AI-driven identity governance with it SailPoint Atlas platform and automated IAM risk management.
Strivacity
Founded in 2019, Strivacity focuses predominantly on customer identity and access management as opposed to workforce and organizational IAM. Like Ping Identity's PingOne DaVinci, the no-code/low-code approach in Strivacity's platform can streamline adoption. Product capabilities include SSO, MFA, self-service and customizable UI and workflow experiences.
Use cases and features
The list above represents a fraction of IAM vendors in the market, so how can you identify the right IAM tools or services for your organization?
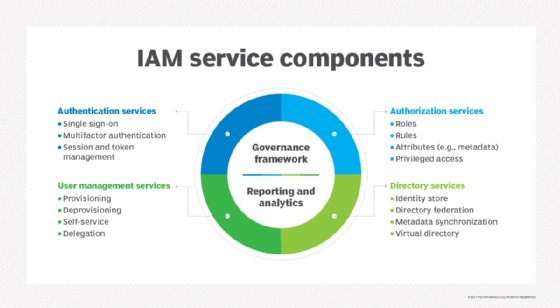
First, IAM products provide two core capabilities: authentication, which confirms a user is who they claim to be; and authorization, which controls what a user can or can't access.
Your organization's use case determines which IAM tools will work best for your needs. For example, are you looking for a system to authenticate and authorize internal users? Or are you looking for a system to authenticate and authorize customers? These might be different systems with diverse features and capabilities. Some software packages overlap, some offerings target both capabilities, while others specialize in one or the other.
In most cases, the best way to begin is to gather your requirements. That is, you'll want to know in a general way at least, the primary use case or cases for a potential identity and access management tool.
Typical IAM product features include one or more of the following:
- Authentication of users, including MFA. These processes validate users by authenticating them using one or more of the following factors:
- What you are using a biometric.
- What you know through use of a PIN or password.
- What you have using a token or mobile phone.
- SSO. Single sign-on allows users to log on once rather than individually for each application they use.
- Privileged access management. PAM manages privileged credential use and credential holders, such as root and administrator accounts, domain admin credentials and application super users.
- Automated user provisioning and deprovisioning. These processes automatically create, remove or modify user accounts, such as when onboarding new employees.
- Access control. Users are assigned rights and privileges dynamically rather than on a per-user basis. This includes the following:
- Role-based access control. RBAC assigns rights based on who the users are, the role they have and the function they perform in the organization.
- Attribute-based access control. ABAC assigns rights based on user attributes such as geographic location, and which business unit or department a user is in.
- Automation and workflow of access. Establishes workflow and/or processes to approve access -- such as a periodic manager review -- and audits assigned rights against current responsibilities.
- Policy management. Establishes central technical enforcement of policies such as password characteristics, history, timeout and conditional access.
- Self-service capabilities. Automates various tasks so users can complete them without administrator or help desk intervention. This includes, for example, password reset, lockouts and forgotten password issues.
- Audit and reporting. Provides capabilities such as tracking and reporting on account use, compliance with policy and enforcement statistics.
- Federated identity. Provides capabilities such as Security Assertion Markup Language (SAML), OpenID Connect or other facilities to identity federation throughout an organization and with partners and SaaS applications.
The above list represents a lot of potential features, but not all vendors support each one of them equally -- and some are better than others at certain things. Therefore, you'll want to get a clear idea of which features are most important to your organization by reviewing the use cases you have previously defined.
So now what?
As you attempt to understand your organization's requirements, you should aim to understand -- with a high degree of specificity -- at least two things:
- Your use case. Are you looking for an employee SSO platform? Mapping out a no-code/low-code customer identity solution? Do you need a partner that can support both? Your use case will dictate the capabilities you most require.
- Needed capabilities. You'll want to understand what you need from your toolset. While most, if not all, vendors provide the basics -- such as SSO, MFA and federation -- some provide niche features such as orchestration or PAM, while others incorporate emerging technologies such as AI to underpin features.
Once you have established these two things, you're ready to evaluate the specific capabilities of individual vendors. Bear in mind, this market sector can be a turbulent one, with frequent acquisitions and consolidations.
Ed Moyle is a technical writer with more than 25 years of experience in information security. He is currently the CISO at Drake Software.








