peshkov - stock.adobe.com
3 types of PKI certificates and their use cases
Public key infrastructure helps authenticate senders via cryptography and digital certificates. Learn about three types of PKI certificates and their use cases.
Data can pass through many networks and systems before it reaches its destination. Securing data and ensuring the authenticity of the sender behind the data are essential. This is where public key infrastructure comes into play.
PKI is a collection of systems and procedures that enables PKI certificates, also known as digital certificates. These certificates are electronic documents, which, via the underlying PKI that binds the public key in a key pair to its entity, verify the authenticity of the entity.
The digital world's equivalent of a passport or driver's license, a PKI certificate also enables digital signatures and authentication mechanisms, such as two-factor authentication (2FA).
PKI certificates are essential to the functioning of an organization, but not all certificates are the same. There are three common types of PKI certificates:
Below, review the three varieties of certificates and their use cases, along with a list of other important PKI certificate-related terms.
1. SSL/TLS certificates
SSL and TLS are two well-known network protocols that use certificates to authenticate a server's identity and encrypt transfers between a browser and a server. Although SSL was superseded by TLS in 1999 and fully deprecated by the Internet Engineering Task Force in favor of TLS in 2015, the certificates are still often referred to as SSL, SSL/TLS or TLS/SSL certificates.
SSL/TLS certificates are issued by a certificate authority (CA). When a user visits a website, the browser connects to a server, and the server shares its certificate and public key with the user. The certificate is then verified to ensure it can be trusted. Next, the browser sends back a public key, which the server decrypts with its private key. The server then sends back a session key to start the encrypted session. This key is only valid for one session. So, if a user tries to interact with the same server again, the process is repeated, and a new session key is created. This transaction is referred to as an SSL/TLS handshake.
SSL/TLS certificates are most commonly used to encrypt and authenticate exchange of data between web servers and web browsers. Websites with an SSL/TLS certificate display HTTPS in the front of their URLs. This certifies the domain is protected by an SSL/TLS certificate, meaning the website can be verified as legitimate and the user's information remains protected when interacting with the site.
SSL/TLS certificates can be used to encrypt communications between any application client and server. This includes web browsers and web servers, using HTTPS, as well as exchanges of data by other client-server applications, including email, file transfer, IM and more. Note, however, that SSL/TLS certificates don't encrypt emails or messages; they encrypt the connection between the sender and recipient.
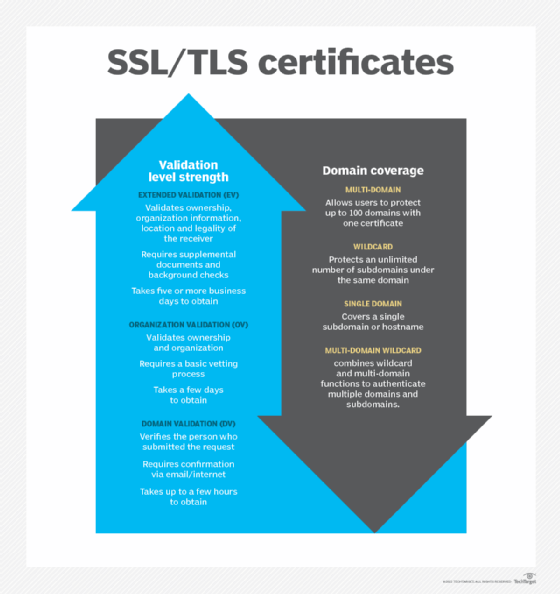
Types of SSL/TLS certificates
The most common types of SSL/TLS certificates are the following:
- Domain validation is a low-level SSL/TLS certificate that validates the certificate holder has the rights to use the domain name. It does not validate who the certificate holder is.
- Organization validation is a midlevel certificate that verifies an organization has the rights to use a domain. The certificate includes the organization's name and address.
- Extended validation is a high-level certificate that verifies the legitimacy of an organization's legal, operational and physical existence.
- Single domain is a certificate that authenticates one domain.
- Wildcard is a certificate that authenticates one domain and an unlimited number of its subdomains.
- Multi-domain is a certificate that authenticates multiple domains.
- Multi-domain wildcard is a certificate that combines wildcard and multi-domain functions to authenticate multiple domains and subdomains.
2. Code signing certificates
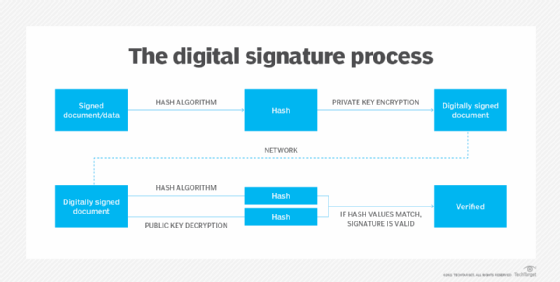
A code signing certificate, also known as a software signing certificate, uses a digital signature to verify the owner of software. The software developer signs the application and any executables -- for example, patches or software updates -- to verify the software code comes from who they say it does and to ensure code has not been altered or tampered with before it reaches end users. A timestamp can be added to the certificate when it's signed, so even if the certificate expires, users know the digital signature is valid.
Software developers and publishers use private keys to add digital signatures to their code. The signature is decrypted by a public key on an end user's device. The user's device then looks for a root certificate to authenticate the digital signature. The device then verifies the hash from the digital signature matches the hash from the code. Only then is the software downloaded.
Code signing certificates protect developer's intellectual property, while also ensuring the integrity of the code and protecting end users from downloading corrupted code. These certificates are mostly used for code published on the internet or third-party platforms. Apple, for example, requires all iOS apps be signed by an Apple-issued certificate.
3. Client certificates
Unlike an SSL/TLS certificate, which authenticates a server's identity and secures data in transit, a client certificate only authenticates an end user's or device's identity. A client certificate, also known as a digital ID or personal ID certificate, connects an ID to a public key. Servers using client certificate authentication use those digital IDs to ensure only allowed people and devices can access systems. Once authenticated, the certificate's private key is used to create a secure connection where users and devices can encrypt data, email and other communications.
Client certificates can be used as an alternative authentication method to passwords, where organizations grant access based on digital IDs. Client certificates can also be used in addition to a password to enable 2FA.
Other terms to know
- Certificate authority. A CA is a trusted entity that issues different types of PKI certificates. CAs also verify certificate information and maintain certificate revocation lists.
- Root certificates. A root certificate is the highest level of certificate. It is used by CAs to create intermediate certificates.
- Intermediate certificates. An intermediate certificate is used to digitally sign certificates issued by a CA.
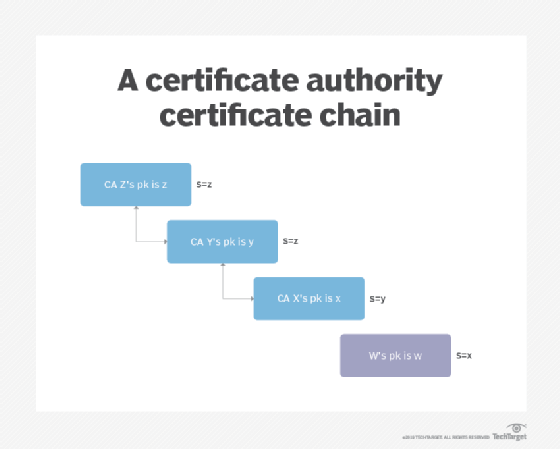
- Certificate chain. A certificate chain starts with a root certificate, which is used to sign the subsequent intermediate certificate, which is used to sign the next certificate and so on. If the top certificate is approved, the entire chain is verified.
![Certificate authority certificate chain]()
In a certificate chain, each certificate is validated by the previous certificate. If the top certificate is verified, the chain can be trusted. - Verified mark certificate. A digital certificate issued by a CA that validates a logo belongs to its owner is called a verified mark certificate. Verified mark certificates enable organizations to display registered trademarks in the avatar slot when sending emails.
- 509 certificate. A digital certificate that uses the X.509 PKI standard to verify the identity of a certificate owner is called an X.509 certificate. Most SSL/TLS certificates are X.509 certificates.