10 biggest data breaches in history, and how to prevent them
Did you know the biggest data breach in history exposed a whopping 3 billion user records? Don't make the same mistakes these companies did in the largest data breaches in history.
Data breaches don't discriminate -- victims include organizations of all shapes and sizes spanning every industry. Attackers are at the ready with both new and tried-and-true tactics, techniques and procedures to break into networks and steal precious data.
From outdated or vulnerable networks to employees clicking phishing emails to misconfigured cloud instances, all organizations would benefit from learning lessons from past data breaches. In fact, many of the biggest data breaches in history could have been prevented if organizations had followed simple cybersecurity hygiene best practices.
Learn more about the largest data breaches, based on the number of records compromised, and get advice on the data protection and data security measures that can help prevent a similar incident at your organization.
1. Yahoo
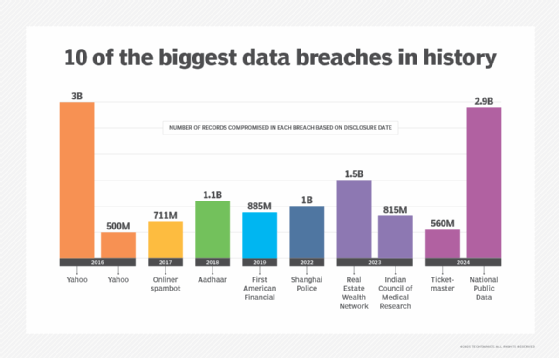
Records compromised: 3 billion
Breach date: August 2013
Disclosure date: December 2016
Yahoo originally announced in December 2016 that its 2013 breach affected only 1 billion user accounts. After Verizon acquired Yahoo, news broke in October 2017 that the figure was actually 3 billion. The breach affected Yahoo email accounts and other company services, including Tumblr, Flickr, Yahoo Fantasy Sports and Yahoo Finance.
This article is part of
What is data security? The ultimate guide
Malicious hackers obtained users' names, dates of birth, phone numbers and passwords, as well as security questions and email addresses used to reset passwords. No financial data -- such as credit card numbers or bank account details -- was exposed. Yahoo announced in its initial disclosure that it forced password resets for all accounts that had been changed since 2013 and invalidated old security questions and accounts. To date, the cause of the breach has not been disclosed.
How to prevent this type of attack
- Conduct continuous security monitoring and testing.
- Perform regular vulnerability scanning and penetration testing.
- Teach employees how to spot phishing attacks.
- Create a cybersecurity awareness training program.
2. National Public Data
Records compromised: 2.9 billion
Breach date: December 2023, April 2024, summer 2024
Disclosure date: August 2024
In August 2024, data aggregator National Public Data (NPD) confirmed it sustained a breach in April 2024. The company, which performed background checks for organizations, private investigators and staffing agencies, later reported that cybercriminals hacked its systems in December 2023, with leaks occurring in April and summer of 2024.
Attackers obtained 2.9 billion records from users in the U.S., U.K. and Canada, including users' names, email addresses, phone numbers, Social Security numbers, mailing addresses and dates of birth. In April 2024, USDoD, the threat group allegedly behind the cyberattack, put the data, which it claimed was from 2019-2024, up for sale on the dark web for $3.5 million in bitcoin or Monero.
Days after NPD acknowledged the breach, security researcher Brian Krebs reported RecordsCheck.net, a sister NPD site, hosted a publicly available database containing source code and site admins' plaintext credentials. Krebs said RecordsCheck.net and NPD were "visually similar" and had "identical login pages." In investigating the database, Krebs said it appeared admins were assigned default passwords, many of which were not changed.
In October 2024, NPD filed for Chapter 11 bankruptcy, and in December 2024 shuttered operations. RecordsCheck.net is also now defunct.
How to prevent this type of attack
- Protect all databases with passwords.
- Encrypt all sensitive data.
- Require users to change default passwords.
3. Real Estate Wealth Network
Records compromised: 1.5 billion
Breach date: Unknown
Disclosure date: December 2023
In December 2023, cybersecurity researcher Jeremiah Fowler reported an unsecured database belonging to Real Estate Wealth Network, an online real estate education and services provider, was publicly available online. The 1.16 TB database, which was not password protected, contained more than 1.5 billion records on users and companies, including celebrities, politicians and Fowler himself.
Exposed personal data included physical addresses, purchase price and date, mortgage company, mortgage loan amount, tax ID numbers, and taxes owed, paid and due.
Fowler said he contacted Real Estate Wealth Network and that the company protected the database "shortly after."
It is unclear how long the database was exposed, but Fowler said it included daily logging records from April 22 to October 23, 2023.
How to prevent this type of attack
- Follow database security best practices.
- Protect all databases with passwords.
- Use encryption to secure data in use, in transit and at rest.
4. Aadhaar
Records compromised: 1.1 billion
Breach date: Unknown
Disclosure date: January 2018
The records of 1.1 billion Indian citizens were exposed after a breach of Aadhaar, the country's government ID database. While citizens aren't required to register with the database, it is required for those who want access to certain government resources or assistance.
The Tribune reported the breach after reporters paid someone on WhatsApp 500 Indian rupees (approximately $8 in 2018) for a code that provided unauthorized access to names, birthdates, email addresses, phone numbers and postal codes from the database. The seller offered reporters -- for an additional Rs 300 (approximately $5 in 2018) -- software that would enable them to print unique ID cards.
The seller was part of a group that gained access to the database through former Aadhaar employees, according to The Tribune. ZDNet later reported the database contained biometric data, including fingerprints and iris scans. ZDNet also said the leak was on a system run by a state-owned utility company that had access to the database via an unsecured API used to verify customers' identities.
How to prevent this type of attack
- Follow API security testing best practices.
- Use API security tools to mitigate risk.
- Adhere to identity and access management best practices.
- Enforce policies to detect and prevent insider threats.
5. Shanghai Police
Records compromised: 1 billion
Breach date: Unknown
Disclosure date: June 2022
In June 2022, a threat actor under the profile name of ChinaDan put an alleged 1 billion users' records from the Shanghai National Police database up for sale on a hacker forum. The 23 TB of data, allegedly from a database hosted on Alibaba Cloud, contained names, addresses, birthplaces, phone numbers, photos, national IDs and criminal records.
Both the New York Times and CNN reported they had verified with multiple individuals the information obtained from samples posted by ChinaDan.
Cybersecurity company LeakIX reported the database used a Kibana instance running version 5.5.3 -- an outdated and unprotected instance of Elastic Stack (formerly known as the ELK Stack). The gateway was not password protected.
Access to the database was revoked soon after ChinaDan posted the listing online.
The exact breach date is unknown, but several researchers have said the database was accessible since April 2021. LeakIX reported that Alibaba privatized or shut down all Kibana servers running version 5.5.3 in July 2022.
Shanghai authorities have not acknowledged or addressed the incident.
How to prevent this type of attack
- Regularly conduct network anomaly detection.
- Protect all databases with passwords.
- Encrypt all sensitive information.
- Regularly patch and update software and systems.
6. First American Financial
Records compromised: 885 million
Breach date: Unknown
Disclosure date: May 2019
In May 2019, Brian Krebs reported 885 million of First American Financials' files were leaked on the insurance company's website. The records, which dated back to 2003, included bank account information, Social Security numbers, mortgage records, tax documents and photocopies of drivers' licenses. The website didn't require a password to access the files.
First American said it had "learned of a design defect in an application that made possible unauthorized access to customer data." The design error, known as insecure direct object reference, is an access control vulnerability where a link meant for a specific viewer is made but does not verify the viewer's identity to allow access.
How to prevent this kind of attack
- Keep insecure direct object references and uniform resource identifiers in mind when securing APIs.
- Follow API security best practices.
7. Indian Council of Medical Research
Records compromised: 815 million
Breach date: Unknown
Disclosure date: October 2023
In October 2023, a threat actor under the alias pwn001 advertised a database containing 815 million records on a dark web forum. They claimed the information, which included users' names, addresses, phone numbers, Aadhaar ID numbers and passport information, was gathered from the COVID-19 test details of citizens, sourced from the Indian Council of Medical Research, a biomedical research organization in India.
Cybersecurity company Resecurity's research team, Resecurity Hunter Unit, said it contacted the threat actor, who said they would sell the data set for $80,000. The team acquired 400,000 sample records from pwn001 and verified the user data with several victims.
Resecurity Hunter updated its October 15, 2023, report saying that pwn001's post was removed by October 31.
The Indian government has not publicly commented on the incident, and no cause for the breach has been published.
How to prevent this type of attack
- Protect all databases with passwords.
- Encrypt all sensitive information.
- Regularly conduct network anomaly detection.
8. Onliner spambot
Records compromised: 711 million
Breach date: Unknown
Disclosure date: August 2017
In August 2017, security researcher Troy Hunt reported that Benkow, a Paris-based security researcher, discovered an exposed spam server known as Onliner. Benkow gave Hunt the spambot's list of 711 million exposed records, which included email addresses and passwords.
Onliner spread via a data-stealing Trojan horse for at least a year before its detection.
How to prevent this kind of attack
- Require employees to change their passwords after a suspected breach.
- Enforce an enterprise password policy.
- Don't reuse passwords.
- Follow password security hygiene best practices.
9. Ticketmaster
Records compromised: 560 million
Breach date: May 2024
Disclosure date: May 2024
On May 27, 2024, hacker group ShinyHunters posted a message on the dark web selling an alleged 1.3 TB of compromised data containing records of 560 million Ticketmaster users for $500,000.
In a Securities and Exchange Commission filing dated May 31, 2024, Live Nation, the parent company of Ticketmaster, confirmed it identified unauthorized activity in a third-party cloud database on May 20. The company said the database contained company data primarily from Ticketmaster and that Live Nation had launched an investigation into the event.
Ticketmaster later reported the breach affected users in the U.S., Canada and Mexico. In a notice to affected customers, Ticketmaster said personal information stolen included customer names, basic contact information and payment card information, such as encrypted credit or debit card numbers and expiration dates.
While Ticketmaster did not reveal the third-party provider, members of the threat intelligence community confirmed with Dark Reading that it was Snowflake, which saw many of its customers under attack during the same time period. In a May 2024 post, Snowflake said it became aware of unauthorized access experienced by some of its customers on May 23, though the company did not name Ticketmaster or any other specific customer.
After an investigation in conjunction with CrowdStrike and Mandiant, Snowflake said it did not find any vulnerabilities, misconfigurations, credential leaks or breaches of its product. It later reported that customers with single-factor authentication appeared to be targeted and that the accounts compromised had credentials previously purchased or obtained through other malware attacks. It named threat group UNC5537 as the perpetrator.
How to prevent this type of attack
- Use MFA.
- Conduct third-party risk management.
- Understand the shared responsibility model.
10. Yahoo
Records compromised: 500 million
Breach date: November/December 2014
Disclosure date: September 2016
Yahoo announced in September 2016 that 500 million of its accounts were compromised in a 2014 state-sponsored attack. Bob Lord, Yahoo CISO at the time, said the stolen data "may have" included names, email addresses, birthdates, phone numbers, passwords hashed with Bcrypt and, in some cases, encrypted and unencrypted security questions and answers. Lord said payment card data and bank account information was not involved.
In 2018, Karim Baratov received a five-year prison sentence for the breach after he was found guilty of helping Russian intelligence officers access the accounts of "individuals of interest." Three other defendants were also named, but remain out of reach of U.S. law enforcement agencies.
Yahoo attributed the attack to a spear phishing email, following an internal investigation.
How to prevent this kind of attack
- Use MFA.
- Teach employees how to spot phishing attacks.
- Create a cybersecurity awareness training program.
- Enforce policies to detect and prevent insider threats.
Sharon Shea is executive editor of Informa TechTarget's SearchSecurity site.
Isabella Harford previously contributed to writing this article.








