What is vulnerability management? Definition, process and strategy
Vulnerability management is the process of identifying, assessing, remediating and mitigating security vulnerabilities in software and computer systems. It's a critical part of managing cybersecurity risk in IT environments, as vulnerabilities that are not found and fixed can expose an organization to damaging cyberattacks and data breaches.
A typical vulnerability management process involves continuously scanning IT assets for vulnerabilities, evaluating the risks of those that are found, and addressing the vulnerabilities in a prioritized order based on risk severity. The goals of vulnerability management include reducing attack surface, improving an organization's overall security posture management, meeting regulatory compliance requirements and minimizing business risks.
Vulnerability management vs. patch management
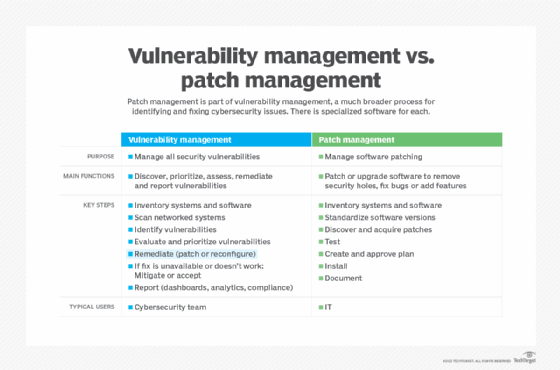
Patch management is a subset of systems management. It involves identifying, acquiring, testing and installing patches or code changes that are intended to fix bugs, close security holes or add features.
Vulnerability management is not the same as patch management. Although they overlap, there are differences between the two processes. Vulnerability management takes a big picture view to identify vulnerabilities and then resolve them across IT systems. Patch management provides a tactical fix for known bugs and security holes in software through the installation of patches typically issued by software vendors. Many practitioners view patch management as a part of vulnerability management.
Vulnerability management vs. risk management
Risk management is the process of identifying, assessing and controlling threats to an organization. These threats could stem from financial, legal, technology, strategic management, accidents or natural disaster-based risks.
Although they are related, vulnerability management differs from risk management. Together, they create risk-based vulnerability management. While vulnerability management focuses on finding and fixing technical security gaps, risk management is a broader initiative for dealing with potential cybersecurity threats and various issues that pose a risk to business operations.
Why vulnerability management is important for organizations
Malicious attackers constantly look for potential security gaps in IT systems. Finding an exploitable vulnerability makes it easier for an attacker to access systems and corporate data and disrupt business operations. Security vulnerabilities can occur in multiple areas, such as applications, endpoint devices, servers, networks and cloud services.
As a result, effective vulnerability management is essential to proactively secure increasingly complex IT environments, and it is a key contributor to a successful cybersecurity maturity strategy. Effectively managing vulnerabilities helps organizations reduce costs, drive more revenue and maintain customer trust. It also provides the following business benefits:
- Reduced attack surface. By finding and remediating vulnerabilities, organizations reduce the number of security flaws that attackers can potentially exploit to breach systems, install malware, steal data or cause operational issues, improving attack surface management processes.
- Less disruption to business operations. Finding and fixing vulnerabilities before they are exploited eliminates potential business disruptions from ransomware infections, distributed denial-of-service attacks and other types of cyberthreats.
- Resource optimization. As vulnerabilities are identified in an organization, prioritizing them based on risk severity as part of a vulnerability management program enables smarter allocation of IT resources to remediate the issues that have the biggest potential impact.
- Increased visibility into security risks. Vulnerability management dashboards provide executives with information on vulnerability trends, outstanding threats, mean time to remediate issues and other relevant security metrics to inform strategic decisions.
- Regulatory compliance documentation. Effective vulnerability management provides evidence of due diligence and cyber-risk reduction to compliance auditors.
No organization is immune to attack; even the smallest ones can benefit from a vulnerability management program. For larger organizations with more systems and applications in place, a single vulnerability could be a pathway to an enterprise-wide attack.
In various industries, including healthcare, financial services, retail and e-commerce, regulatory compliance measures require organizations to have vulnerability management initiatives in place. For example, vulnerability management practices are mandated by government and industry regulations such as the Health Insurance Portability and Accountability Act, the Gramm-Leach-Bliley Act and the Payment Card Industry Data Security Standard. These industries are also required to comply with ISO 27001, formally known as ISO/IEC 27001:2022, an information security management standard developed by the International Organization for Standardization.
How does vulnerability management work?
Vulnerability management is not a single task; it's a multistep process that IT security teams conduct on an ongoing basis. In addition to vulnerability scanning tools that probe IT systems for missing patches, misconfigurations, unprotected sensitive data and other issues, vulnerability management often includes penetration testing -- or pen testing for short -- that attempts to exploit vulnerabilities in systems to measure their risk level for an actual attack.
Using the results of scans and pen tests, vulnerability assessments are done to evaluate potential threats. As part of an assessment, information about identified vulnerabilities can be fed into a threat intelligence platform and scored based on potential impact and exploitability. For example, a missing patch that could enable a remote code execution attack would likely be deemed a high risk.
Security teams then prioritize and remediate the detected issues through various actions, depending on the nature of the vulnerabilities. In the case of the missing patch, an organization's security team generates a remediation workflow ticket for the IT operations staff that's responsible for the affected systems. After IT ops installs the patch, the security team commonly will run a scan to confirm that the vulnerability was patched properly.
Throughout the vulnerability management process, the status of vulnerabilities is tracked against remediation goals and service-level agreements (SLAs), giving an organization's security leaders and business executives real-time visibility into cybersecurity risk reduction and compliance efforts.
Who is responsible for vulnerability management?
Responsibility for vulnerability management typically falls under IT security teams and, more specifically, is shared across multiple roles in an organization. These include the following:
- Security officer. The security officer is accountable for designing the vulnerability management policies and ensuring their correct implementation.
- Vulnerability engineer. This person is accountable for conducting and managing vulnerability scans and scanning tools.
- Asset owners. Asset owners are accountable for the system assets that are scanned and any identified vulnerabilities that are addressed.
- IT system engineers. These engineers are accountable for implementing fixes to identified vulnerabilities.
Key steps in the vulnerability management process
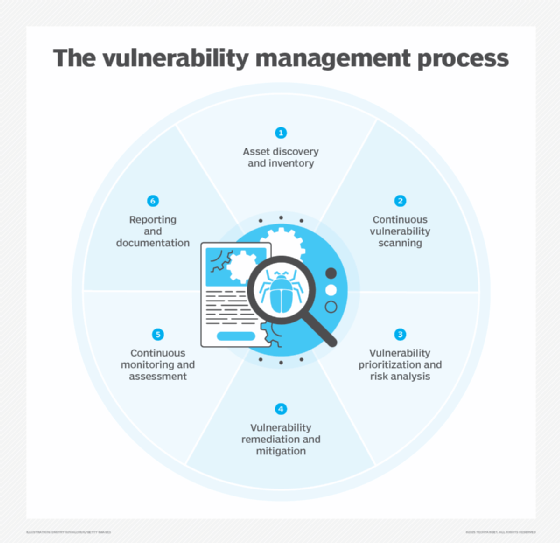
The following examines the core steps in a vulnerability management initiative:
- Asset discovery and inventory. Develop a comprehensive inventory of all the technology assets deployed in and connected to the organization's IT infrastructure, including servers, endpoints, cloud resources and networking equipment. This inventory provides the foundation for all subsequent vulnerability management activities.
- Continuous vulnerability scanning. Vulnerability scanners check the inventoried assets and identify potential vulnerabilities in them. Scanning is commonly performed by automated tools that probe for known vulnerabilities through lightweight agents installed on IT systems and devices. Pen testing, which can be automated or done manually, also helps find unknown flaws and gauge the extent to which vulnerabilities are exploitable.
- Vulnerability prioritization and risk analysis. Detected vulnerabilities are evaluated and prioritized based on the level of risk they pose to the organization. Factors such as vulnerability type, the business importance of affected assets and the potential impact of exploits are used to determine priority levels. Organizations can use the Common Vulnerability Scoring System, an open framework maintained by the Forum of Incident Response and Security Teams, to help rate risk severity.
- Vulnerability remediation and mitigation. The next step is to eliminate vulnerabilities by implementing remediation measures, such as patching, upgrading software, reconfiguring systems or retiring assets that are no longer needed. If full remediation is not feasible, mitigation techniques can be used to reduce risk -- for example, by isolating vulnerable systems.
- Continuous monitoring and assessment. Because vulnerability management is an ongoing cycle, scans must be run regularly to ensure that remediation work is effective and to identify new threats. Asset inventories are also updated on an ongoing basis, and various metrics are used to measure the effectiveness of the vulnerability management program.
- Reporting and documentation. Detailed reporting provides data on identified vulnerabilities, the progress of remediation and risk reduction efforts, and the program's overall status to help communicate security risks and resource needs to business stakeholders.
Common vulnerability management challenges
The vulnerability management process is not always smooth. Sometimes, the number of vulnerabilities and how quickly they can be exploited can put undue stress on IT teams when deciding what to handle first.
The following are some common challenges organizations face when implementing and running vulnerability management programs:
- Lack of a complete asset inventory. Not having full visibility into all the assets across complex IT environments can make comprehensive scanning difficult.
- Resource prioritization. With thousands of potential vulnerabilities to deal with in some cases, determining which ones should be fixed first requires mature processes.
- Interteam coordination. Effective vulnerability remediation requires collaboration between security and IT teams, which can be hampered by weak processes and poor communication.
- Reliance on manual processes. Manual workflows for vulnerability tracking and remediation often don't scale and lead to delays in addressing issues.
- Tool sprawl. Disjointed vulnerability management tools that are not integrated can cause workflow gaps and limited visibility into security risks.
- Difficulties getting a full view of vulnerabilities. Complex environments, especially in large organizations, make getting a unified view of vulnerabilities across the enterprise a challenge.
- Remediation gaps. Even when vulnerabilities are found, efforts to remediate them can be hampered by resource constraints and disparate systems.
- Dealing with dynamic attack surfaces. New vulnerabilities emerge continuously, complicating the process of monitoring and managing the attack surface in an organization.
How to evaluate your vulnerability management program
To properly evaluate enterprise vulnerability management programs, organizations should keep track of the following vulnerability-related metrics:
- Mean time to remediate. This is the average time it takes to fix a vulnerability after it has been discovered.
- Mean time to detect. This is the average time it takes to identify a vulnerability after initial discovery.
- Vulnerability discovery rate. This is the rate of new vulnerabilities scanned and detected over a given period.
- Coverage of vulnerability scans. This is a percentage of known assets that are scanned for vulnerabilities.
- Recurring vulnerabilities. This is a measure of how many previously remediated vulnerabilities reappear in scans.
- Mean open vulnerability age. This is the average number of vulnerabilities that go unresolved over time.
- Open vs. closed vulnerabilities. This compares total active vulnerabilities against remediated ones during the same time frame.
- Percentage of critical vulnerabilities addressed. This measures how many vulnerabilities have been mitigated or patched within a given time.
- SLA compliance. This tracks the percentage of vulnerabilities that are remediated within a defined service-level agreement.
Core features of vulnerability management tools
Various vulnerability management tools are available to help organizations identify and fix security weaknesses at scale. The following are some of the core features and capabilities that the tools provide, many of which correspond to steps in the vulnerability lifecycle:
- Asset discovery.
- Vulnerability scanning.
- Vulnerability prioritization and risk ratings.
- Built-in remediation workflows.
- Compliance mapping of vulnerabilities to regulatory frameworks.
- Alerting functions to notify security teams of critical new vulnerabilities and other high-priority issues.
- Application programming interface integrations to synchronize vulnerability data with other security tools.
- Customizable rules and policies to meet specific vulnerability management requirements.
- Dashboards and reporting tools.
When choosing a vulnerability management tool, organizations should look for features that can streamline their risk reduction goals and integrate well within their environment. The tool should provide contextual lists of vulnerabilities and risks based on priority. Likewise, to ensure that any potential vulnerabilities are addressed as quickly as possible, the chosen tool should be able to scan for vulnerabilities and risks continually. Performed vulnerability scans should also cover all relevant technologies the organization uses to ensure there are no remaining security gaps.
Some security tools are starting to integrate AI features to streamline management processes. Learn more about how AI is being integrated into vulnerability management.






