What is user authentication?
User authentication refers to the process of verifying the identity of a user attempting to gain access to a computer network, system or device. This process runs in the background and can be done through different means, such as asking the user to enter a password, provide a personal identification number (PIN) or provide a fingerprint.
The goal of user authentication is to confirm that the user is who they say they are before allowing them to access a specific computing resource. The term contrasts with machine authentication, which is an automated authentication method that does not require user input to verify their identity and allows or blocks their access to a computing resource.
Why is user authentication important?
Authentication ensures only authorized users with the right privileges can gain access to a system by verifying the information that they provide. In this way, it plays a role in enhancing users' digital experiences while protecting the computing resources. Authentication is crucial in preventing data breaches and cyber attacks. It prevents unauthorized users from gaining access to resources, ensuring that they cannot damage or compromise the system, steal information, or cause other problems.
Apart from guest accounts and automatically logged-in accounts, almost all human-to-computer interactions on wired and wireless networks perform authentication to enable users to access networked and internet-connected systems and resources. The authentication process can be as simple as requiring a user to provide a unique identifier, such as a user ID and a password. The authentication mechanism can also be complex. For example, it may require a user to provide information about physical objects or the environment or take specific actions, such as placing a finger or thumb on a fingerprint reader.
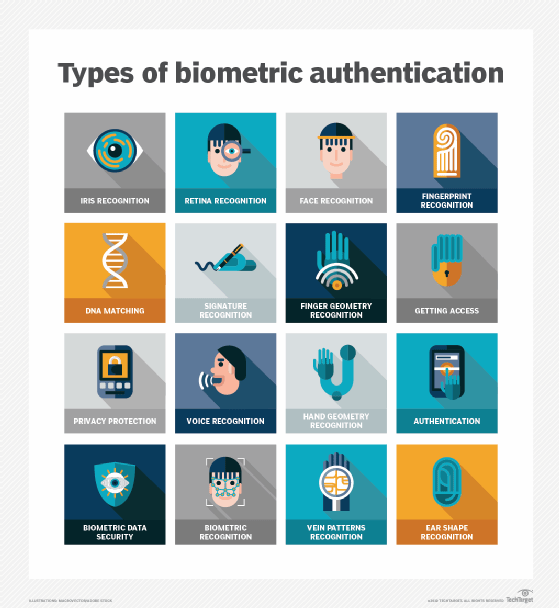
User authentication methods
There are many ways to implement user authentication and ensure that the right users have access to the right resources. The most common method is password-based authentication, which requires users to provide a unique user ID and password. This is also one of the weakest authentication methods because most users tend to do the following:
- Use weak passwords that can be easily guessed by unauthorized or malicious parties (cybercriminals).
- Use the same password across multiple accounts, increasing the likelihood of compromise of all those accounts if the password is stolen.
- Share or write down passwords, increasing the chances of password theft and account compromise.
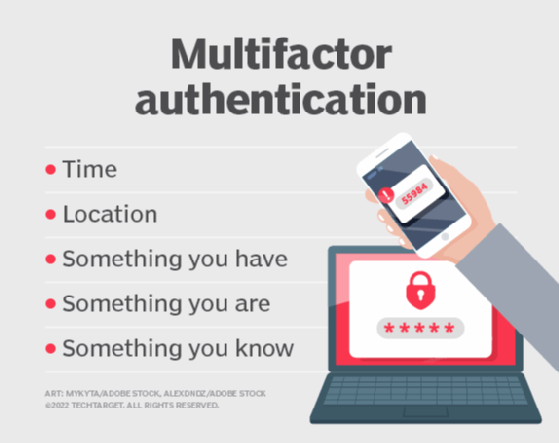
Multi-factor authentication (MFA) provides a stronger authentication mechanism than password-only authentication, also known as single-factor authentication, SFA or 1FA. MFA requires users to provide additional factors to gain access to a system or account. For example, a two-factor authentication (2FA) system might require the user to provide a password and mobile token; a three-factor authentication (3FA) system might mandate a password, mobile token and thumbprint; and so on. Thumbprints, iris prints, handprints, voiceprints, etc. are all types of biometric authentication, in which an individual's unique biological characteristics are used to authenticate them and facilitate their access to digital resources.
Two other authentication methods are becoming increasingly popular. Certificate-based authentication uses digital certificates to identify and authenticate users. The certificate contains the user's digital identity and the digital signature of a trusted certification authority (CA). This is a reliable way to establish trust in digital transactions and confirm that the entities involved are who they say they are. Finally, token-based authentication involves the use of randomly-generated characters on a physical security token device. The user must use the token to gain access to a certain system. This method provides a secure method of access and enhances user experiences because users don't have to repeatedly provide their access credentials.
Authentication factors
Almost all authentication mechanisms use one or more factors to verify user identities and enable access to digital resources. These factors can be one of five types:
- Knowledge factors include all things users must know to log in to gain access to a system. Usernames, IDs, passwords and PINs all fall under this category.
- Possession factors consist of anything users must have in their possession to log in. This category includes one-time password tokens, key fobs, smartphone apps and employee ID cards.
- Inherence factors include characteristics inherent and unique to individuals that confirm their identity. This category includes biometrics, such as retina scans, fingerprint scans, facial recognition and voice prints.
Other possible authentication factors include location and time factors, which are typically used together or in conjunction with another authentication factor:
- Location factors confirm users' identities through their location For example, the location factor can help prevent an unauthorized person, such as a cyber attacker from logging into a user's system because the attacker and authorized user are in different locations. In such systems, location and password are typically used together to confirm a user's identity and to keep out unauthorized users.
- Time factors add time-based access characteristics to confirm identity. Similar to the location factor, the time factor is not adequate on its own but can be helpful when used with another factor. For example, if a system last authenticated a user at noon in the U.S., an attempt to log in an hour later from Asia would be rejected based on the combination of travel time and location. A time factor can also only permit access within a scheduled time interval such as normal business days.
Single-factor authentication vs. multifactor authentication
Single-factor and multifactor authentication differ significantly.
SFA requires verification of only one piece of information from a user, such as a password. Because SFA commonly employs knowledge factors, which require only a single piece of information, it usually cannot stop unauthorized parties from gaining access to a user's system.
Multifactor authentication uses more than one method of authentication to verify and minimize the potential for account compromise.
User authentication limitations and improvements
Several issues affect the security of an authentication system. In addition to the number of factors involved, the specific technologies used and the way they are implemented affect reliability. Well-designed and appropriately enforced implementation rules can help ensure the security of user authentication.
For example, passwords -- among the most vulnerable methods of authentication -- are relatively insecure because knowledgeable hackers can easily guess and crack them. To alleviate the problem, several industries and organizations have implemented strong password standards and rules. One common rule is to mandate that all users create passwords of a certain minimum length. Another is to include at least one number, letter and symbol (special character) in each password.
The ubiquity of mobile devices and cloud computing today affects how enterprises implement authentication. In the past, a simple password authentication system was sufficient to keep networks and data secure. However, the increased risk of data breaches has forced more companies to reevaluate their authentication strategies. Specifically, many are adopting authentication processes involving two or more factors to ensure a higher level of security
That said, it's important to find a balance between security and user experiences. While MFA provides added security and a more reliable way to confirm a user's identity, it also can overburden users by requiring them to provide multiple factors to prove their identities. Forcing users into difficult authentication routines can inconvenience them and lead to noncompliance with rules, which might then undermine the purpose of the authentication system. Implementing automation with MFA or single sign-on can enhance security while minimizing the effort required by the user.
User authentication is key to securing networks. Learn about the different authentication types available, including 2FA, biometrics and certificates. Also, explore the best enterprise mobile app authentication methods.








