
What is triple extortion ransomware?
Triple extortion ransomware is a type of ransomware attack where a cybercriminal extorts their victim multiple times -- namely by encrypting data, exposing exfiltrated data and then threatening an additional third attack vector.
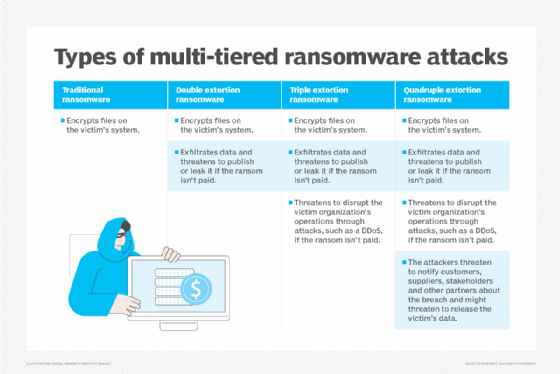
In a traditional ransomware attack, an attacker encrypts the victim's data, preventing them from accessing it.
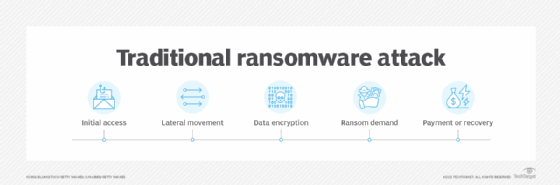
In a double extortion ransomware attack, a second attack vector is added. Typically, a copy of an organization's data is stolen or removed. Victim organizations can often recover from a traditional ransomware attack using backups. However, by exfiltrating data in a double extortion attack, the attacker has another chance to extort the victim -- or demand two ransoms.
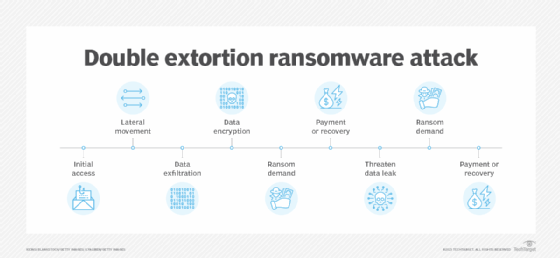
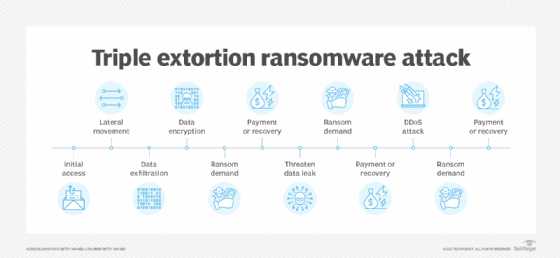
A triple extortion ransomware attack adds a third attack vector and the potential for a second -- or third -- ransom. This third attack vector could be a distributed denial-of-service (DDoS) attack or intimidating the victim's customers, employees and stakeholders into paying a ransom.
With the triple extortion approach, attackers aim to compel victims into paying multiple ransoms by introducing extra threats and risks beyond blocking access to data. This approach is harder to recover from and can also incur reputational harm.
Ransomware is becoming more common, with double and triple extortion incidents on the rise. According to Verizon's "2024 Data Breach Investigations Report," ransomware and data extortion accounted for 32% of reported attacks. According to Sophos' "The State of Ransomware 2024" report, ransomware affected 59% of organizations in 2024.
How does a triple extortion ransomware attack work?
At the initial stages, a triple extortion ransomware attack follows the same basic attack sequence as a common ransomware attack but adds the second and third attack vectors. A typical triple extortion ransomware attack includes the following steps:
- Initial access. Attackers gain entry into their victim's network, often through phishing, malware, vulnerabilities or stolen credentials.
- Lateral movement and asset discovery. Once they have access to the network, attackers probe deeper into an environment to elevate privileges and find potentially valuable data.
- Data exfiltration. Once identified, high-value assets are stolen to use in a double extortion attack.
- Encryption of files. Attackers encrypt the data to prevent the victim from accessing it.
- Ransom demand. With the data encrypted and exfiltrated, attackers send a ransom note to the victim demanding payment, typically in cryptocurrency, to receive the decryption key and regain access.
- Double extortion ransom demand. If the victim organization can restore its data from backups -- or even if it has paid the first ransom -- the malicious actors return for a second attack and demand a second ransom payment to prevent them from publishing or leaking the victim's sensitive data.
- Triple extortion ransom demand. In the third attack, attackers threaten additional exploitation, such as a DDoS attack or even approaching the victim organization's customers, employees and third parties to demand payment. If the victim organization has yet to pay the ransom, this would exert additional pressure on it to do so, and if it has already paid, it could be used to squeeze an additional ransom.
Beware: Malicious actors often demand increasingly higher payments with each additional ransom. Law enforcement agencies discourage organizations from paying the ransom, but many organizations still opt to pay. They should consult with ransomware negotiation services to help get a better outcome.
Double extortion ransomware vs. triple extortion ransomware
Double extortion ransomware and triple extortion ransomware are similar in many respects. The main difference between them is that triple extortion adds a third threat vector. The goal of double and triple extortion ransomware is to put additional pressure on victims to pay even more money to prevent further attacks. There are also quadruple extortion attacks. These attacks build on traditional ransomware and add a fourth vector: Attackers threaten to notify the victim's customers and other stakeholders to inform them of the breach and threaten to release the victim's data.
Organizations can buy ransomware and cyber insurance, which can cover losses like business interruptions, incident response, data recovery and reputational harm in the case of a ransomware attack. Cyber insurance can cover double, triple and quadruple extortion ransomware attacks, but specific coverage depends on the policy.
Notable examples of triple extortion ransomware
Since 2020, several ransomware groups have launched triple extortion ransomware attacks. The following are examples of these attacks:
- AvosLocker. A ransomware-as-a-service (RaaS) operation, AvosLocker was active in 2022, leading to a Federal Bureau of Investigations advisory warning about the group.
- BlackCat. Also known as ALPHV, the BlackCat ransomware group became a major threat in 2022 with attacks against fuel and aviation companies, as well as universities. In 2023, the group claimed responsibility for the cyberattack on Barts Health NHS Trust.
- Hive. The Hive ransomware group executed large triple extortion ransomware attacks until late 2022, when U.S. law enforcement disrupted its operations.
- Vice Society. In 2022 and 2023, Vice Society emerged as a triple extortion ransomware threat, targeting public sector and educational organizations. In February 2023, Vice Society claimed it had successfully attacked the San Franscisco Bay Area Rapid Transit system.
- Quantum. The Quantum ransomware gang was active in 2022 and known for selling victim data. Among its many victims was the Glenn County Office of Education in California, which paid a $400,000 ransom.
- RansomHub. First seen in February 2024, RansomHub has claimed more than 600 RaaS attacks globally, causing disruption and financial losses to organizations in healthcare, manufacturing, education, real estate and other industries. Believed to be the successor to ALPHV, its origins appear to be Russian-affiliated countries.
How to prevent triple extortion ransomware
To prevent and limit the risk of triple extortion ransomware attacks, organizations should follow these best practices:
- Strengthen access controls. Use strong passwords and multifactor authentication, limit administrative privileges to servers and disable or restrict access to remote desktop protocol.
- Deploy patches and software updates. Ensure all operating systems, software and firmware are patched and up to date.
- Tighten network security. Secure networks with micro-segmentation and virtual LANs to reduce the risk of attackers moving laterally across them. Make sure firewalls are in place alongside intrusion prevention and detection systems.
- Implement monitoring and logging. Monitor networks for suspicious connections, scan logs for indicators of compromise and watch for signs of credential misuse.
- Conduct cybersecurity awareness training. Teach employees about phishing and social engineering. Raise awareness of suspicious emails, URLs and attachments.
- Create an incident response plan. Develop and test a ransomware incident response plan. Ensure it covers detection, analysis and containment.
- Perform backups and test recovery efforts. Maintain regular offline, encrypted backups and store them in a location separate from the production network. Regularly test restoration capabilities from backups. Consider buying cyber insurance to offset any costs if a ransomware incident does occur.
Tools businesses can use to defend against ransomware
Defending against traditional, double and triple ransomware attacks requires a cybersecurity strategy that is extensive and multi-layered. Key security tools should provide the following:
- Network protection.
- Endpoint protection.
- Cloud security.
- Data protection.
- Monitoring and threat detection.
- Endpoint detection and response.
- Identity and access management.
- Intrusion detection.
- Zero-trust frameworks.
- Data loss prevention.
- Backup and disaster recovery.
- Network segmentation and firewalls.
The following is a sampling of these tools:
- Bitdefender.
- Cisco Secure Endpoint.
- ESET Protect.
- F-Secure Total.
- Kaspersky Premium.
- Malwarebytes ThreatDown Endpoint Protection and Endpoint Detection & Response.
- OpenText MDR (formerly Webroot MDR).
- Sophos Endpoint.
- Symantec Enterprise Cloud.
- Trend Micro’s Trend Cloud One.
There are numerous cybersecurity tools an organization can use to protect against malware and ransomware attacks. Learn more about each of the previously mentioned ransomware protection tools.





