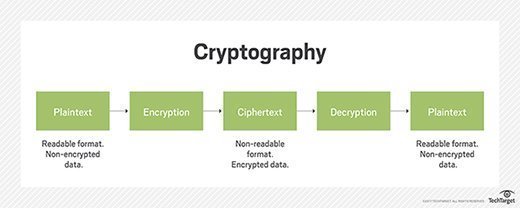
What is a stream cipher?
A stream cipher is an encryption method in which data is encrypted one byte at a time. In this method, a cryptographic key and algorithm are applied to each binary digit in a plaintext data stream to produce ciphertext. This makes stream ciphers different from block ciphers, in which a key and algorithm are applied to blocks of data rather than to individual bits.
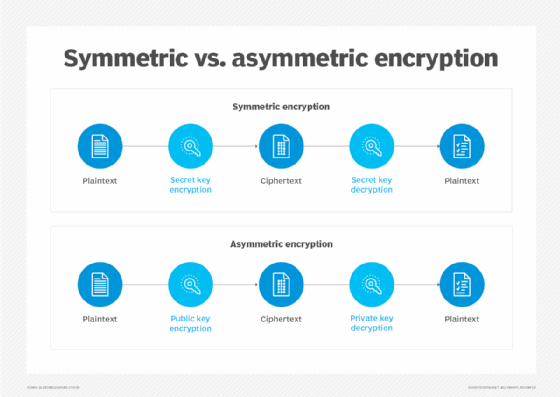
Stream ciphers are symmetric and linear, meaning the same key is used to both encrypt and decrypt data. Due to this characteristic, they offer limited security, making them unsuitable for modern applications where security is paramount. That said, they are still used for many internet and telecommunications applications due to their speed and simplicity. Popular stream cipher algorithms include Rivest Cipher 4, Salsa20, ChaCha20, Trivium, Grain, CryptMT and Fibonnaci Shrinking.
What are the main characteristics of stream ciphers?
A stream cipher is an encryption algorithm that uses a symmetric key to encrypt and decrypt a given amount of data. This key -- also known as a keystream since it is a set of random characters that replaces the characters in the plaintext -- is shared by the participants in a transaction for encryption and decryption. In contrast, asymmetric encryption algorithms use two different keys: a public key to encrypt a message and another private key to decrypt the respective ciphertext. The private key is known only to the message recipient.
Like all encryption methods, stream ciphers modify or scramble plaintext data to generate ciphertext that is unreadable to unauthorized or malicious users. However, what makes them unique is that they encrypt data one bit, or byte, at a time. This makes for a fast and relatively simple encryption process.
Encryption using stream ciphers requires three main components:
- Message, document or piece of data.
- Key.
- Encryption algorithm.
The key typically used with a stream cipher is known as a one-time pad. Mathematically, a one-time pad is unbreakable because it demonstrates the cryptographic principle of perfect secrecy, which means it's always at least the exact same size as the message it is encrypting. Additionally, the ciphertext looks completely random, preventing outsiders from deriving the entire message simply by looking at the ciphertext.
Stream ciphers can be either synchronous or self-synchronizing. In a synchronous stream cipher, the keystream is generated independently of the plaintext and ciphertext, while self-synchronizing stream ciphers use both a secret key and some randomization technique to increase security and prevent hacking.
How does a stream cipher work?
The following example illustrates the one-time pad process of stream ciphering.
Person A (sender) attempts to encrypt a 10-bit message using a stream cipher. The one-time pad is also at least 10 bits long -- although this can become cumbersome depending on the size of the message or document they are attempting to encrypt. The sender could create a pseudorandom cipher digit stream, or keystream, using a key that is smaller than the size of the plaintext file. Furthermore, to avoid having to create a larger keystream, they can use a cryptographic number generator to create a larger keystream from a smaller, pseudorandom key.
They decide to use a 4-bit key to encrypt their message. First, they use an initialization vector (IV) to generate a random seed value. To maximize the security of the encryption process, the IV should be random and unpredictable. Also, the same IV should not be used more than once. Placing this seed value into a cryptographic number generator creates a pseudorandom keystream that matches the size of the desired plaintext file. The quality of the number generator contributes to the randomness and security of the ciphertext. Lower-end cryptographic number generators can sometimes have patterns that malicious users or hackers can identify and use to decrypt the ciphertext.
After the keystream is created, the stream cipher combines the keystream with the corresponding digits of the plaintext using the XOR (exclusive-OR) operator. The XOR operator creates new binary values by comparing bits in the plaintext and the keystream that share the same position. These values make up the ciphertext. Thus, the first bit in the message is XORed with the first bit of the keystream. If the two digits are the same, the XOR operator produces a zero. If they are different, the XOR operator produces a 1. This is part of what makes stream cipher encryption so fast. Once each bit of data has been XORed by the stream cipher, it produces an unreadable ciphertext message.
Ciphertext decryption happens in a similar manner to plaintext encryption. This time, instead of the data and keystream being XORed, the ciphertext and the keystream are XORed. As long as the recipient has the key, they can transform the scrambled ciphertext data back into plaintext.
Advantages of stream ciphers
Encryption speed is the biggest advantage of stream ciphers. Once a stream cipher makes a key, the encryption and decryption process is almost instantaneous. This is largely due to the simplicity of operation due to the use of a basic XOR function using two distinct data bits and the same key for encryption and decryption. For this same reason, the technological complexity of a stream cipher is quite low. Simply put, complex or expensive hardware is not required to use stream ciphers for encryption.
Another advantage of stream ciphers is the ability to decrypt selected sections of ciphertext. Since each bit of data in the ciphertext corresponds with plaintext data in the same position, users can decrypt ciphertext for part of a document rather than the entire file. Also, there's no need to wait to start the encryption process. The ability of stream ciphers to encrypt data bit by bit means that information can be encrypted and sent as soon as it's available.
Given these advantages, stream ciphers are still used by many web browsers and websites with Secure Sockets Layer. Many applications that involve real-time communication, like voice calls, video streaming and online gaming, as well as digital rights management applications, also use stream ciphers.
Drawbacks of stream ciphers
Stream ciphers are not especially secure due to the positional alignment among the plaintext, keystream and ciphertext. During the encryption process, a hacker who obtains a segment of plaintext and its respective ciphertext may be able to deduce the keystream used by the process. This is why cryptographers refer to stream ciphers as having low diffusion, meaning the plaintext and ciphertext are not vastly different from each other.
Error propagation is another problem of stream ciphers. If a particular bit is received in error or if an error occurs during transmission, the subsequent bits can also be affected. Since the cipher relies on previously stored bits for decryption, errors that occurred earlier can result in erroneous output after decryption.
It's important to ensure that the keystream is properly designed with the correct number of bits. Mistakes increase the risk of cryptanalysis, compromising the security and integrity of the encrypted data. Also, the keys should be used only once to maintain security and prevent system compromise -- especially in situations where hackers manage to steal a previously used key.
Confusion vs. diffusion
Evaluate encryption methods using two main criteria:
- Confusion contributes to the ambiguity of the ciphertext -- i.e., the methods used to complicate the relationship between the plaintext and the ciphertext.
- Diffusion, on the other hand, refers to how well the encryption hides these complex, or simple, relationships. For example, a standard for diffusion is that at least 50% of the ciphertext should change when a cipher alters a single bit of plaintext. Encryption operations with low diffusion are less secure than those with high diffusion.
Stream cipher vs. block cipher
Block ciphers and stream ciphers are two distinct forms of symmetric key encryption. The main difference between these modes of operations is the amount of data they encrypt at one time. While stream ciphers perform data encryption one bit at a time, block ciphers encrypt fixed blocks of information all at once. These predetermined data blocks are typically either 64 or 128 bits long. If the data is not long enough -- i.e., it is smaller than the block size -- pads are added.
The difference in mode of operation is what makes stream ciphers more suitable for encrypting data in transit and block ciphers more suitable for data at rest. It also means that stream ciphers require less processing power and are faster compared to block ciphers.
That said, the distinction between stream ciphers and block ciphers can become confusing because a block cipher primitive can sometimes be used in such a way that it is effectively a stream cipher on a larger scale. Simply put, block ciphers can operate as stream ciphers in some situations. The reverse is not true.
Other than the difference in block size, the encryption and decryption methods employed are nearly identical.
See best practices for wireless network security, tips for managing guest wireless network access and how the Wi-Fi Protected Access 3 security protocol simplifies logins and secures the internet of things. Learn why experts warn cryptography techniques must keep pace with threats and about the importance of security and data encryption in the cloud. Also, explore what quantum computers mean for cryptography.





