What is email spoofing?
Email spoofing is a form of cyber attack in which a hacker sends an email that has been manipulated to seem as if it originated from a trusted source. Email spoofing is a popular tactic used in phishing and spam campaigns because people are likelier to open an email when they think a known sender has sent it. Email spoofing aims to trick recipients into opening or responding to the message.
Why email spoofing is a serious problem
Although most spoofed emails can be easily detected and remedied by simply deleting the message, some varieties can cause serious problems and pose security risks. For example, a spoofed email could pretend to be from a well-known shopping website, asking the recipient to provide sensitive data, such as a password or credit card number.
Alternatively, a spoofed email could include a link that installs malware on the user's device if clicked. A common example of business email compromise involves spoofing emails from a company's chief executive officer or chief financial officer requesting a wire transfer or internal system access credentials.
According to a report from the Anti-Phishing Working Group titled "Phishing Activity Trends Report: 4th Quarter, 2022," the top industries targeted by spoofing emails include finance, software as a service, social media providers, logistics and shipping, and payment services.
In addition to phishing, attackers use spoofed email to do the following:
- Hide the fake sender's real identity.
- Bypass spam filters and blocklists -- users can minimize this threat by blocklisting internet service providers and Internet Protocol (IP) addresses.
- Pretend to be a trusted individual -- a colleague or a friend -- to elicit confidential information.
- Pretend to be a reliable organization -- for example, posing as a financial firm to get access to credit card data.
- Commit identity theft by impersonating a targeted victim and requesting personally identifiable information.
- Damage the sender's reputation.
- Launch and spread malware hidden in attachments.
- Using a man-in-the-middle attack to seize sensitive data from individuals and organizations.
- Obtain access to sensitive data collected by third-party vendors.
How can email spoofing be dangerous?
The potential harm of email spoofing covers a considerable range, making it a form of social engineering attack worth defending against. The following are some of the areas where that harm can occur:
- Scams from false trust. Spoofing enables a hacker to pose as an executive, vendor or other trusted contact. This false trust can lead to fraudulent payments, wire transfers and other losses.
- Data breaches. Spoofing can expose sensitive information if employees are misled into revealing credentials and other information providing system access. Once inside a network, hackers can potentially gather confidential information for various purposes.
- Reputational damage. A company or organization that suffers successful spoofing attacks that result in significant losses or data breaches can lose consumer or client trust, diminishing its reputation. Moreover, a hacker can potentially surface personal information in a target computer, enabling them to tarnish a specific victim's reputation.
- Blocklist avoidance. A spoofed email address can be crafted to avoid the settings of spam filters, keeping the address off blocklists. This capacity to remain undetected is one of the more insidious features of the spoofing technique.
What's the difference between email spoofing and phishing?
Cybercriminals often use spoofing as part of a phishing attack. Phishing obtains sensitive data by faking an email address and sending an email that looks like it's coming from a trusted source that could reasonably ask for such information. The goal is to make victims click on a malicious link or download an attachment that installs malware on their system.
Spoofing alters the email header so the email appears to be from a trusted source. This is also related to domain impersonation, in which an email address similar to another is used. In domain impersonation, an email might come from an address, such as "[email protected]," while, in a spoofing attack, the fake sender's address looks genuine, such as "[email protected]."
How email spoofing works
Email spoofing can be easily achieved with a working Simple Mail Transfer Protocol (SMTP) server and common email platform, such as Outlook or Gmail. Once an email message is composed, the scammer can forge fields found within the message header, such as the FROM, REPLY-TO and RETURN-PATH addresses. When the recipient gets the email, it appears to come from the forged address.
This is possible to execute because SMTP doesn't provide a way to authenticate addresses. Although protocols and methods have been developed to combat email spoofing, adoption of those methods has been slow.
An email spoofing attack can take many forms. One typical example is an email that appears to be from a peer-to-peer (P2P) payment platform, such as Venmo, Zelle or PayPal, informing the recipient that their account will be suspended if they don't click on a link and provide their credentials. The idea, of course, is to steal the credentials. The hacker can then log in to the payment platform as the spoofed recipient and take their money.
A hacker can easily make a spoofing email look legitimate by copying graphics or other familiar elements from the P2P platform's website, reducing the likelihood that the recipient will question it.
How to tell if an email has been spoofed
If a spoofed email doesn't appear suspicious to users, it will likely go undetected. However, if users sense something is wrong, they can open and inspect the email source code. Here, the recipients can find the originating IP address of the email and trace it back to the sender.
The following are some indicators that an email has been spoofed:
- Sender Policy Framework check. SPF is an authentication protocol in many email platforms and security products. Depending on users' email setup, messages classified as soft fail might still arrive in their inbox, often indicating an illegitimate sender.
- Email header. The various elements of the email header might be inconsistent, suggesting that the sender isn't who they say they are. Comparing the suspect email header to a previous legitimate email from the authentic sender might confirm the spoof.
- Request for personal disclosure. If an email urges the recipient to disclose personal sensitive information, such as private demographic data or personal account information, it's suspect.
- Recycled content. A hacker deploying an email spoof often recycles content from a previous spoof. Copying and googling the email text to see if it matches any previous phishing emails online can help identify a spoofed email.
9 best practices for stopping email spoofing
Users and businesses can use the following techniques to prevent email spoofers from accessing their systems.
1. Deploy an email security gateway
Email security gateways protect businesses by blocking inbound and outbound emails with suspicious elements or emails that don't meet the security policies a business implements. Some gateways offer additional functions, but all can detect most malware, spam and phishing attacks.
2. Use antimalware software
Antimalware software programs can identify and block suspicious websites, detect spoofing attacks and stop fraudulent emails before they reach user inboxes.
3. Use encryption to protect emails
An email signing certificate encrypts emails, allowing only the intended recipient to access the content. In asymmetric encryption, a public key encrypts the email, and a private key owned by the recipient then decrypts the message. An additional digital signature can ensure the receiver that the sender is a valid source. In environments without broad encryption, users can learn to encrypt email attachments.
4. Use email security protocols
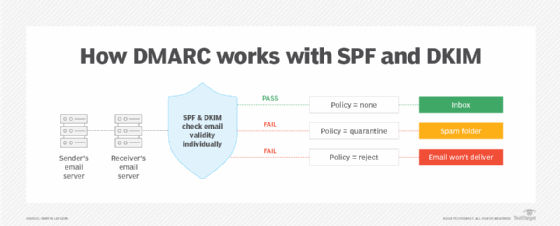
Infrastructure-based email security protocols can reduce threats and spam by using domain authentication. In addition to SMTP and SPF, businesses can use DomainKeys Identified Mail (DKIM) to provide another layer of security with a digital signature. Domain-based Message Authentication, Reporting and Conformance (DMARC) can also be implemented to define actions to take when messages fail under SPF and DKIM.
5. Use reverse IP lookups to authenticate senders
A reverse IP lookup confirms that the apparent sender is real and verifies the email's source by identifying the domain name associated with the IP address.
Website owners can also consider publishing a domain name system record stating who can send emails on their domain's behalf. Messages are inspected before the email body is downloaded and can be rejected before causing harm.
6. Train employees in cyber awareness
In addition to software-based antispoofing measures, businesses must encourage user caution, teaching employees about cybersecurity and how to recognize suspicious elements and protect themselves. Simple educational programs can equip users with email spoofing examples and enable them to spot and handle spoofing tactics and procedures to follow when a spoofing attempt is discovered. Training should be ongoing to update the materials and methods as new threats emerge.
7. Watch out for possible spoofed email addresses
The email addresses users communicate with are often predictable and familiar. Individuals can learn to watch out for unknown or odd email addresses and to verify an email's origin before interacting with it. Attackers often use the same tactics multiple times, so users must remain vigilant.
8. Never give out personal information
In many situations, even if spoofed emails get into an inbox, they only cause real damage when a user responds with personal information. By making it a common practice never to divulge personal information in emails, users can significantly limit the effects email spoofing could have.
9. Avoid strange attachments or unfamiliar links
Users should also steer clear of suspicious attachments and links. As a best practice, they can examine every element of an email, looking out for telltale signs, like misspellings and unfamiliar file extensions, before going ahead and opening a link or attachment.
As the use of artificial intelligence increases, AI-powered phishing attacks are becoming more dangerous. Learn what best practices cybersecurity practitioners can follow to detect and prevent AI phishing attacks.






