shadow password file
What is a shadow password file?
A shadow password file, also known as /etc/shadow, is a system file in Linux that stores encrypted user passwords and is accessible only to the root user, preventing unauthorized users or malicious actors from breaking into the system.
The common practice of storing passwords in the /etc/passwd file leaves the Linux system vulnerable to break-in attempts. To eliminate this vulnerability, newer Linux systems use the /etc/shadow file to store user passwords instead.
Traditional password files are maintained in /etc/passwd, but the actual hashed passwords are stored in /etc/shadow.
Authentication with /etc/passwd and /etc/shadow
In older Linux systems, user information, including passwords and usernames, are kept in a system file called /etc/passwd. This plaintext database is used to keep track of every user on the Linux system. The file is owned by the root and can only be modified by root or users with sudo privileges, although it is readable by all system users.
Each user's password is stored in an encrypted form within the /etc/passwd file. These credentials are hashed using a one-way hash function so they cannot be decrypted. So, user authentication takes place by comparing the contents of the /etc/passwd file to the user's encrypted password upon logging in -- after the password is rehashed with the key or salt.
If there is a mismatch, the user cannot access the system. However, the reuse of passwords -- a common problem among users -- and the increasing use of rainbow tables by threat actors to crack password hashes and gain entry into Linux systems have made this old system insecure.
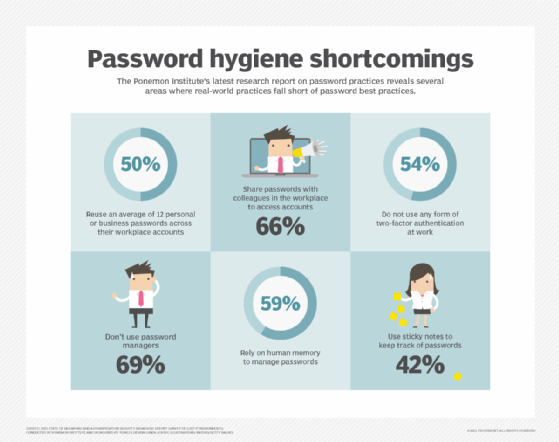
The /etc/shadow file provides an enhanced authentication mechanism for Linux systems by tightening access at the account level. This text file stores actual passwords in hashed format, along with additional information related to these passwords.
The one-way hash function converts the plaintext into a hash. Each password is stored as a long character string that's a combination of the hashing algorithm, the hashed password and an optional salt to add greater randomness to the mix.
The file is owned and can only be accessed by the root user -- the Linux administrator account, also known as a superuser account -- and the shadow group. By comparison, etc/passwd is considered a world-readable file, as many tools read it to verify ownership and authentication.
To decrypt the password in /etc/shadow, a malicious user would need to know the hash string and the hashing algorithm used. They would then have to brute-force each password by trying every combination, hashing it and confirming if it matches the hash stored in the database. This is a long, convoluted and undesirable process that's made possible by the shadow file, which is how it keeps bad actors out of the system -- something that the older /etc/passwd file cannot always manage.
The need for a shadow password file
Passwords within the /etc/passwd file are encrypted using a randomly generated value or encryption key between 1 and 4,096 and a one-way hashing function. The key or salt is also stored with the encoded password.
Still, the /etc/passwd file is vulnerable to unauthorized access. Despite every password being hashed, the hacker could still view them in the /etc/passwd file, since the file itself is world-readable. Moreover, for encryption, the file only supports the basic and outdated Data Encryption Standard (DES) algorithm.
Hackers armed with a password cracking tool can crack passwords encrypted with DES, especially if users have weak or common passwords. They may launch a dictionary attack to methodically test each encoded password in the /etc/passwd file against their dictionary of commonly used passwords, each encoded 4,096 different ways to cover all hash possibilities.
If passwords are weak, such as "1234567" or "password", cybercriminals may be able to break into the system within just a few hours.
Admins can address this risk by moving the passwords in the /etc/passwd file to the /etc/shadow file, which, by definition, is readable only by those who have access to the system root directory. The traditional /etc/passwd file is still maintained, as it contains more than just password information, including the username, user identifier, user's group identifier and absolute path to the user's home directory.
The encrypted passwords, along with other information -- such as password expiration date, the minimum number of days required between password changes and the maximum number of days the password is valid -- are kept in the shadow password file.
Any process that requires access to the shadow password file must be either owned by the root or it must be granted root-level permissions prior to access. This provides stronger security against password snooping and attacks that target the /etc/passwd file's vulnerabilities.
Format of a shadow password file
The shadow password file contains one entry per line, with each line representing one user account listed in the /etc/passwd file. The first line usually describes the root user, followed by the system and normal user accounts.
Each line of the file contains nine fields that are separated by colons:
- Username. User account and login name that exist in the system.
- Encrypted password. Password using the format $type$salt$hashed and eight to 12 characters long.
- Last password change. Date since Jan. 1, 1970, when the password was last changed.
- Minimum password age. The minimum number of days that must elapse before the password can be changed by the user.
- Maximum password age. The number of days after which the password must be changed.
- Warning period. The number of days before the password expires, during which time the user gets a warning to change the password.
- Inactivity period. The number of days post-expiration -- since Jan. 1, 1970 -- before the user's account is disabled.
- Expiration date. The date on which the account was disabled.
- Unused. This field is left empty and reserved for future use.
No one should edit the shadow password file manually.
Common commands used in shadow password files
To change a user's password, the passwd command must be used.
To set up password aging, the chage command must be used by the root user.
To verify the integrity of password files, the pwck command can be used. This command does the following:
- verifies the integrity of users and authentication information;
- checks that all entries in /etc/passwd and /etc/shadow are in the proper format and contain valid data; and
- prompts users to delete entries that are improperly formatted or entries that contain other uncorrectable errors.







