What is a session key?
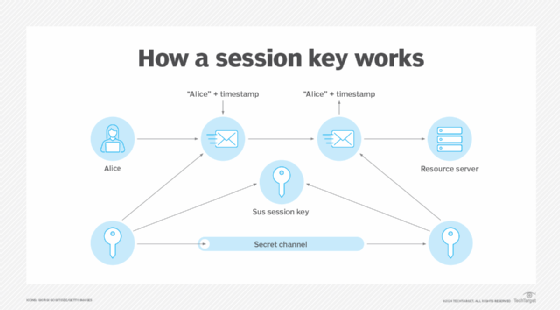
A session key is an encryption and decryption key that is randomly generated to ensure the security of a communications session between a user and another computer or between two computers. Session keys are sometimes called symmetric keys because the same key is used for both encryption and decryption.
The session key is used for only one session. It is then discarded, and a new key is randomly generated for the next session. In contrast, public keys, or asymmetric encryption, use two keys -- a public key and a private key -- instead of a single key to secure data communication between two parties over an open network.
Session keys and symmetric encryption
All cryptographic encryption methods involve the use of keys for encryption and decryption.
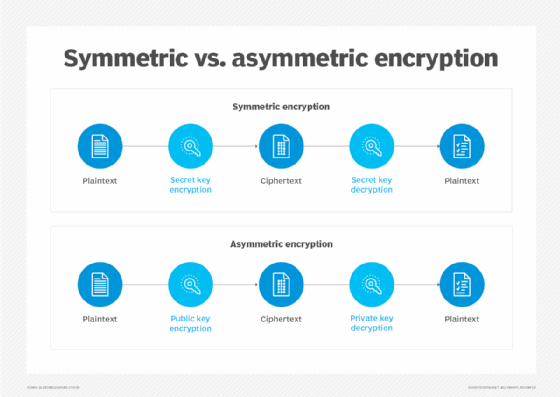
In asymmetric cryptography -- also known as public key infrastructure (PKI) -- two different keys are used: a public key that is used by a data sender to encrypt the data and a private key used by the data recipient to decrypt and read the data. The public key is available for anyone to use, while the private key remains private and is known only to the message recipient.
In symmetric encryption algorithms, the same key is used as both the public and private key -- hence the term symmetric. As a result, anyone holding the key can both encrypt and decrypt the data being sent. This key is known as a session key since it is temporary, meaning it can only be used for a single communication session between a sender and a recipient. When a new session begins between the two parties, a new session key needs to be generated to encrypt and decrypt data.
What is a session?
A session is typically an interaction or conversation between a user and a web server and is characterized by an exchange of information. This exchange may be in the form of a request-response between a browser and the web server. It begins when a user's device requests a page from the web server and is completed when that browser has sent over all the packets of information the server requested, such as when a user logs in to a website. This series of interactions between the user and the website requires a data connection and is, therefore, considered a session.
That said, a session may not involve a request or response between the two parties. For instance, when a user signs in to a web service, the session is simply an exchange of information that results in the user signing in to the service and the server storing this information for later use.
Other kinds of sessions include the following:
- Hypertext Transfer Protocol session. An HTTP session is a series of interactions between a user's browser and a web server that persists beyond a single page view and enables the server to track a user's activity
- Transmission Control Protocol session. A TCP session is a logical connection between two network hosts established by the exchange of transport layer segments.
- Telnet remote login session. A Telnet session is a method used to connect to and interact with a remote server.
In general, a session persists for the period in which the two parties continue to communicate. It can also persist for a certain fixed period, after which it expires. To reopen the connection and reestablish communication, the parties have to generate new session keys.
Benefits of cryptographic session keys
Cryptography is an essential tool in the fight against identity theft that is used to protect information in a wide range of applications, such as electronic commerce, information security and data storage. Cryptography uses keys to encrypt and decrypt data. Session keys, which are generated using a symmetric algorithm, provide the following benefits:
- Convenient to use. Session keys can be a single fixed key, or they can be generated dynamically from a set of existing keys.
- Added protection. A session key is discarded after it is used to establish a secure communication channel, such as during a Transport Layer Security (TLS) connection. Using different session keys for subsequent sessions makes data less vulnerable to cryptanalysis -- the process of decrypting encrypted text without using the real key -- by unauthorized or malicious parties.
- Faster to use. Since session keys are single-use symmetric keys, they are much faster to use than asymmetric keys for certain applications, such as for storing caches of temporary data. Session keys also offer better performance than asymmetric PKI encryption for real-time applications, like secure messaging.
Disadvantages of session keys
Session keys do have some disadvantages, including the following:
- Not as secure as asymmetric (public) keys. Due to their simplicity, session keys are less secure than asymmetric public/private keys. This can be problematic for applications where data integrity is critical.
- Vulnerable to compromise. Using a session key for more than one session may result in the session's compromise and adversely impact the integrity and security of the data being exchanged.
- Risk of eavesdropping. Since a single key is used to both encrypt and decrypt data, it puts information security at risk should bad actors intercept the key in transit over the network or steal it when it's stored in the memory of a server.
- Risk of cryptanalysis. The more data that's encrypted and decrypted using a single session key, the higher the risk of cryptanalysis and thus transaction compromise.
HTTPS encryption and session keys
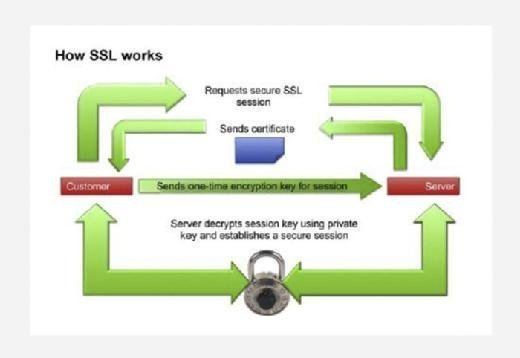
HTTPS is a web protocol that encrypts data sent between a browser and website. The encryption ensures a connection is private and gets the data to its destination securely so it can't be intercepted and read in transit by an unauthorized party. When a user's browser sends a request to access a website via HTTPS, it generates a session key. This key encrypts the sent data and also decrypts it when it is received.
For instance, if a user enters their checking account information to buy items online, their browser encrypts that information using a session key. The website's server then decrypts it using the session key it received from the browser.
How does a TLS handshake work?
To create a secure HTTPS connection between two computers -- for example, a client device and a web server -- a TLS handshake must occur. A TLS handshake refers to a series of steps that occurs when connecting to a website with HTTPS:
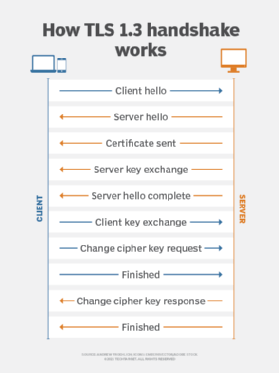
- The server sends its Secure Sockets Layer certificate to the client.
- The client checks the certificate.
- The client encrypts a random number with a public key.
During the TLS handshake, the communicating devices establishes the session key. The session key encrypts the bulk of the data transmitted in the handshake and is generated and negotiated independently of the protocol version and cipher suite selected by the clients and servers. As a result, the session key is the same for all connections established between two peers that support the same protocol version.
If the TLS handshake fails -- usually due to misinformation passed back and forth between two communicating computers -- then the connection is not secure, so the risk of someone eavesdropping on the connection and/or stealing sensitive data is high.
Concepts related to session keys
There are several encryption technologies that are related to session keys, including the following:
- Master encryption key. An MEK is an encryption key that protects the integrity of the other encryption keys. This cryptographic key is not usually used for encryption or decryption. Rather, it is used to generate a large number of other session keys that are then used for communications. Since session keys are only needed for a short period of time, a master key is more practical than a per-use key.
- Key encryption key. A KEK is used to encrypt other keys, such as the data encryption key or the traffic encryption key, that are used to encrypt sensitive data.
- Content encryption key. A CEK is a key that may be further encrypted using a KEK. The CEK is used to encrypt content for storage or transmission, including content in the form of messages, images, audio and so forth.
See best practices for wireless network security, tips for managing guest wireless network access and how the Wi-Fi Protected Access 3 security protocol simplifies logins and secures the internet of things. Learn why experts warn cryptography techniques must keep pace with threats and about the importance of security and data encryption in the cloud. Also, explore what quantum computers mean for cryptography.








