screened subnet
What is a screened subnet?
A screened subnet, or triple-homed firewall, refers to a network architecture where a single firewall is used with three network interfaces. It provides additional protection from outside cyber attacks by adding a perimeter network to isolate or separate the internal network from the public-facing internet.
Screened subnet explained
Used in networks that have both public and private areas, a screened subnet lets users access the internet without exposing the local area network to internet-based cyber attacks or data breaches. It does this by establishing a network between an internal network and an external/presumed hostile network, such as the internet. This ensures that there is no single vulnerable point that could potentially compromise the entire enterprise network.
It uses three network interfaces:
- Interface 1 is the public interface connected to the internet.
- Interface 2 connects to the demilitarized zone (DMZ) to which hosted public services are attached.
- Interface 3 connects to the intranet to provide access to and from internal networks.
The subnet's main purpose is to isolate the DMZ and its publicly accessible resources from the intranet, thereby minimizing external attention and possible attacks on that subnet. The architecture makes it more difficult to attack the intranet, especially when a properly configured firewall is combined with the use of private IP addresses on one or both of these subnets. Even if the firewall itself is compromised, an attacker won't be able to access the intranet.
This design of a screened subnet firewall is based on other system security models, like dual-homed gateways and screened host firewalls. Since it adds an additional layer of security to the network, a screened subnet is suitable for many high-traffic sites.
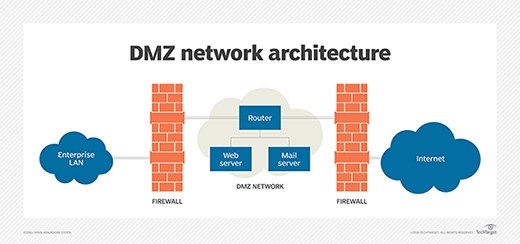
Screened subnet architecture
A screened subnet uses logical screening routers as a firewall to define three separate subnets. One is the external router that, as the name suggests, separates the external network from a perimeter network. Next, the internal router isolates the perimeter network from the internal network, or intranet.
The perimeter network hosts the servers, or bastion hosts, which can be accessed and have access to both internal and external networks. This network is also known as the DMZ or border network.
The simplest type of screened subnet architecture consists of two routers: one between the perimeter net and internal network and the other between the perimeter net and the external network. The external network is usually the internet.
The components that make up the architecture are the following:
- perimeter network
- bastion host
- interior router
- exterior router
Perimeter network
This network sits between the external network and protected internal network. It shields systems from attackers by adding an additional layer of security between the two networks. So, if attackers break into the bastion host on the perimeter network, they can only snoop on traffic on that net.
No internal traffic, which may be sensitive, proprietary or business-critical, passes over the perimeter net, thus shielding this traffic from attackers even if the bastion host is compromised.
Bastion host
Bastion hosts act as proxy servers for numerous services by running specialized proxy server software or standard servers for self-proxying protocols, like Simple Mail Transfer Protocol.
In the screened subnet architecture, bastion hosts are attached to the perimeter net. A host acts as a point of contact for incoming connections from the outside world, such as the internet. It handles outbound services -- from internal networks to internet servers -- in two ways:
- Packet filtering on exterior and interior routers allows external servers to directly access internal clients.
- Proxy servers can be set up to run on the bastion host. This allows internal clients to indirectly access external servers.
In both cases, the site's security policy determines which internet host the bastion host connects to and which services it accesses.
Interior router
Also known as a choke router, this router is responsible for protecting the internal network from the perimeter net and the internet. It performs most of the packet filtering for the firewall and some services from the internal net to access the internet.
The interior router also allows services between the bastion host and internal net. However, these may not be the same services that the interior router allows between the internet and the internal network.
Usually, it's best to limit the allowable services between the bastion host and internal network to an as-needed basis to reduce the number of machines and services a threat actor can attack.

Exterior router
Also known as an access router, the exterior router is responsible for protecting the internal net and perimeter net from the external internet. These routers do little packet filtering and allow almost everything outbound from the perimeter net. Also, the packet filtering rules to protect internal machines are usually the same on both internal and exterior routers.
One important task of an exterior router is to shield any incoming packets from the internet that contain forged source addresses. In addition, it can prevent IP packets with inappropriate source addresses from leaving the network. This can reveal configuration problems, source address forging and other serious network issues.
Screened subnet architecture limitations
Despite its security advantages, a screened subnet architecture has some limitations. It's expensive to build and difficult to configure and maintain, for example. It can also be hard to troubleshoot if there are problems, and unresolved problems can open many security holes that lead to cyber attacks.
The firewall can be made to permit some trusted services between the internet and internal systems. This subverts the security policy and may also weaken the firewall's effectiveness. Finally, the architecture relies on packet filtering routers for security, which can be complex to configure and increase the risk of security mistakes.
See also essential elements of network security, top 10 network security best practices to implement today, why both endpoint security and network security matter, the top network security techniques for modern companies and how to plan now for the future of network security.








