What is post-quantum cryptography? Comprehensive guide
Post-quantum cryptography, also known as quantum encryption or PQC, is the development of cryptographic systems for classical computers that can prevent attacks launched by quantum computers.
In the 1980s, scientists speculated that if computers could take advantage of the unique properties of quantum mechanics, they could perform complicated computations faster than classical, binary computers. It quickly became clear that a quantum computer, taking advantage of quantum properties such as superposition and entanglement, could complete certain types of complex calculations in a matter of hours -- something that would take a classical computer several years to complete.
In the 1990s, after mathematician Peter Shor successfully demonstrated that a theoretical quantum computer could easily break the algorithm used for public key encryption, cryptographers around the world began to explore what a post-quantum cryptography system would look like. As of this writing, standards for post-quantum encryption are still emerging.
Pre-quantum vs. quantum vs. post-quantum cryptography
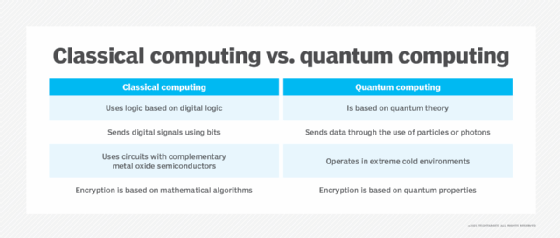
Quantum computers use the laws of quantum mechanics to process information in quantum bits, or qubits. Because each qubit can be a combination of 0s and 1s, a quantum computer can process variables exponentially faster than a classical computer.
Pre-quantum cryptography uses a specific type of cipher called an algorithm to transform human-readable data into secret code. The challenge of pre-quantum cryptography is to make encryption ciphers easy to understand but difficult to reverse-engineer.
Quantum cryptography relies on the physical properties of atoms and uses geometric ciphers to transform human-readable data into unbreakable secret code. A major challenge of post-quantum cryptography is that quantum physics is an emerging scientific field of study, and prototypes for quantum computers are expensive to build and operate.
The quest for quantum-resistant algorithms
In 2016, researchers from MIT and the University of Innsbruck built a small quantum computer that successfully implemented Shor's algorithm and found the factors for the number 15. Once researchers demonstrated that Shor's quantum algorithm could return the correct factors with a confidence level that exceeded 99%, it became clear that a quantum computer could break the world's most widely used cryptographic methods.
That same year, the National Institute of Standards and Technology (NIST) began seeking out submissions for algorithms that could potentially replace public key encryption, key encapsulation mechanisms and digital signatures. Mathematicians and programmers began experimenting with a variety of strategies to replace integer factorization and the discrete logarithmic problems used in the Rivest-Shamir-Adleman (RSA) algorithm, Elliptic Curve Digital Signature Algorithm, Elliptic-curve Diffie-Hellman Key Exchange and Digital Signature Algorithm cryptosystems.
Google's experiments in post-quantum cryptography, for example, involve coupling a classical elliptic curve algorithm with a post-quantum algorithm. The idea is that even if quantum cryptography turns out to be breakable, the addition of an elliptic curve algorithm will still provide a measure of security.
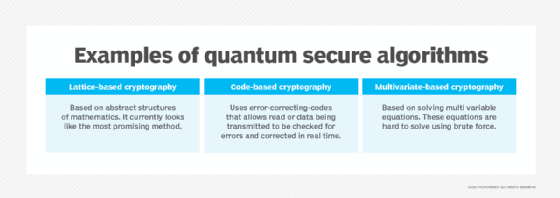
Other popular strategies for quantum-resistant algorithms include the use of lattice, code-based and multivariate schemes. As of this writing, lattice schemes seem to be the most promising because it's extremely difficult to calculate the shortest vector of a large lattice when the shortest vector is quantum and can exist in more than one dimension.
The algorithms that support encryption today, including public key cryptography, are considered safe for e-commerce. While quantum computing is real, the technology is expensive, and use cases have their roots in scientific and government research. The race is on, however, between researchers trying to find a post-quantum encryption that works and researchers trying to break RSA and similar cryptosystems with quantum algorithms.
Many experts believe that quantum supremacy will be reached within nine or 10 years, at which time RSA and similar asymmetrical algorithms will no longer be able to protect sensitive data. NIST is therefore aggressively looking to create a standard for post-quantum encryption.
Experts recommend that while NIST is busy evaluating the effectiveness of proposed standards for post-quantum cryptography, organizations use the next couple of years to create a reference index for applications that use encryption, as well as keep track of public and third-party encryption libraries. Once the strategies for PQC implementation have matured and a standard has been approved, organizations can use the index to develop a plan for how to replace or upgrade applications that require cryptography.
Post-quantum cryptography vs. quantum key distribution
Post-quantum cryptography should not be confused with quantum key distribution. QKD enables a secret cryptographic key to be shared between two remote parties in a way that makes key interception easily detected.
The future of post-quantum cryptography
The future of post-quantum cryptography will be defined by the need to replace traditional cryptographic algorithms with quantum-resistant alternatives capable of withstanding quantum threats. As quantum algorithms advance, widely used protocols like Transport Layer Security and RSA will become vulnerable to exploitation, requiring a transition to PQC algorithms that can secure data both in transit and at rest. Key research areas include the development of new signature schemes, key cryptography methods and based cryptography that rely on mathematical problems currently believed to be resistant to quantum attacks.
Standards groups such as NIST and the International Organization for Standardization are evaluating proposed cryptosystems to ensure effective implementation and global adoption. This field also anticipates increased investment in quantum cryptography, even though its practical deployment remains limited.
In the coming years, governments and technology vendors are expected to introduce certified post-quantum cryptography applications and update widely used security protocols to reflect the shift. As quantum computing moves closer to practical reality, securing data against future decryption efforts will be critical for long-term trust and resilience.
How organizations can prepare for post-quantum cryptography
Organizations should begin preparing for post-quantum cryptography now by assessing where public key cryptography is used within their systems and identifying dependencies that will require transition. A comprehensive migration plan must include an inventory of cryptographic assets and a roadmap for replacing at-risk certificates, signature methods and encryption algorithms.
To reduce risk, enterprises should allocate resources to researching emerging post-quantum cryptography standards and integrating quantum-safe design principles into their IT projects. Establishing internal guidelines for future implementation will help teams be prepared when post-quantum transition requirements become urgent.
It is also important to engage with vendors and partners to evaluate services that align with evolving post-quantum cryptography recommendations. Because today's encrypted data could be harvested and decrypted later, organizations must act before quantum attacks materialize to ensure that their infrastructure is future-proof and capable of maintaining secure communications in the quantum era.
Post-quantum cryptography is the future of quantum computing cybersecurity. Learn why quantum-resistant algorithms matter.







