plaintext
What is plaintext?
In cryptography, plaintext is usually ordinary readable text before it is encrypted into ciphertext, or readable text after it is decrypted.
Data input to or output from encryption algorithms is not always plaintext. For example, when data is superencrypted, or encrypted more than once using different encryption algorithms, only the input to the first encryption method is considered plaintext.
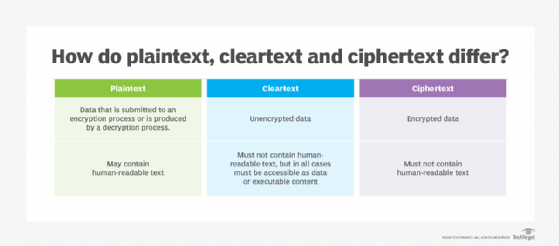
Plaintext vs. cleartext vs. ciphertext: What are the differences?
Plaintext and ciphertext go together like water and ice: One can be converted to the other, and back again, with no change to the inherent composition of the useable form. But there is also cleartext, which is not necessarily the same as plaintext.
Binary files are not usually considered plaintext, because they are not human-readable -- but they are still accessible to end users. Examples of non-plaintext binary files include the following:
- executable program files;
- rich media files, including images, video and audio recordings; and
- data files generated by applications like spreadsheets, databases and word processors, which may be partially or completely stored as binary data.
In Request for Comment (RFC) 4949, "Internet Security Glossary, Version 2," the Internet Engineering Task Force differentiates between plaintext and cleartext, noting that the two terms are not interchangeable. For the purpose of internet security, cleartext data is not encrypted, while plaintext data could be encrypted if it is being superencrypted.
According to the National Institute of Standards and Technology (NIST), plaintext refers to "intelligible data that has meaning and can be understood without the application of decryption," although this is one of several definitions NIST recognizes -- including the IETF definition.
What are examples of plaintext?
For most applications, plaintext is preferred. For example, a browser, word processor or email client should display plaintext. However, network protocols used in the early internet sometimes exchanged user ID and password pairs in plaintext. This is not good security practice because it exposes user credentials for systems accessed remotely over a public network like the internet. The open source Mimikatz cybersecurity tool is designed specifically to sniff open networks for plaintext user credentials, among other functions.
Other examples where using a protocol or application that does not encrypt user ID and password exposes credentials include the following:
- The Password Authentication Protocol described a protocol for a two-way handshake authentication exchange, but it had no provision for encrypting credentials.
- Plaintext passwords written in application configuration files expose those credentials. Less commonly, developers leave plaintext passwords in their source code, which also exposes those credentials.
- Protecting passwords in PowerShell scripts. Developers must take precautions to avoid exposing those passwords in their scripts.
- Sharing secret keys or private keys in email clients presents a common situation when using encryption and decryption. Protocols and applications using shared secrets for authentication should always be designed and configured to encrypt shared keys -- and early internet protocols like were not always designed to do so. For example, the Internet Mail Access Protocol (IMAP) is an email client protocol for retrieving and managing email messages. IMAP originated in the 1980s, and legacy deployments did not always require encryption for credentials.
Cyber attacks commonly target resources stored in plaintext. Many attacks succeed by uncovering plaintext files that contain passwords or other sensitive information in plaintext rather than encrypted.
Often, plaintext is preferred for the content in question. For example, plaintext emails are messages that contain only text. Promotional email campaigns often use plaintext messages to avoid strict spam-filtering systems that tend to block messages that are HyperText Markup Language-encoded or that add other binary components.
There's a little-known middle ground between ciphertext and plaintext that helps retain the ability to process metadata from encrypted data. Find out why, sometimes, format-preserving encryption could be a good fit.





