What is pharming?
Pharming is a scamming practice in which malicious code is installed on a PC or server, misdirecting users to fraudulent websites without their knowledge or consent. The aim is for users to input their personal information into the fake website's login, registration or other page.
Once information, such as a credit card number, bank account number or password, has been entered at a fraudulent website, criminals have it to use for identity theft or other nefarious purposes. A majority of social engineering attacks that result in credential theft originate with compromised business emails.
How does pharming work?
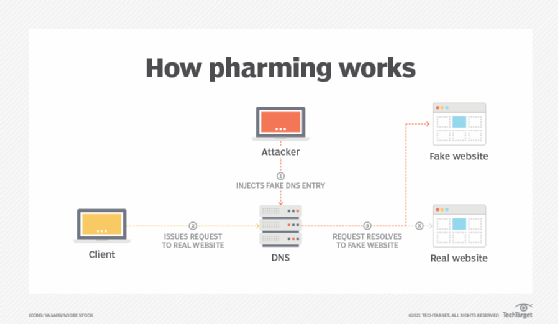
Pharming uses the Domain Name System (DNS) to redirect users from the intended domain to another website. Attackers exploit vulnerabilities in the DNS protocol or compromise insecure DNS servers, adding entries that redirect traffic.
The DNS server translates domain names, such as google.com, to Internet Protocol (IP) addresses, such as 187.128.30.49. If a pharmer -- a hacker engaged in pharming -- changes a website's IP address in the DNS server, then a user's computer is given the wrong IP address when accessing that website. By causing the DNS server to give the user the corrupted address, the pharmer sends them to a fake site to try to elicit personal or other sensitive information.
Pharming techniques
There are a few different forms of pharming. The most common include the following:
- Malware-based pharming. This is when code sent in an email modifies a PC's local host files. The host files convert URLs into the IP addresses that the computer uses to access websites. A computer with a compromised host file will go to the fake site even if a user types in the correct web address or clicks on a bookmark entry. Some spyware removal programs can correct the corruption, but it frequently recurs unless the user changes browsing habits, such as blocking pop-up ads and cookies. For this reason, it is recommended that users install a reliable cybersecurity software program to both clean the system and protect it.
- DNS cache poisoning. With DNS cache poisoning, the DNS table in a server is modified so that someone who thinks they're accessing a legitimate website is actually directed to a fraudulent one. In this method of pharming, individual PC host files don't need to be corrupted. Instead, the problem occurs in the DNS server, which handles millions of internet users' requests for URLs. Victims then end up at a bogus site without any visible indicator of a discrepancy. Spyware removal programs can't deal with this type of pharming because nothing is technically wrong with the users' computers.
- Social engineering pharming. In this instance, cybercriminals use social engineering techniques to trick users into going to a fraudulent website. The techniques used are similar to phishing in that they often involve impersonating trusted entities through emails, text messages and phone calls with the aim of getting the victim to click on a link that takes them to the fake site.
Examples of pharming attacks
There are several different examples of pharming attacks. The most common examples include:
- Login credential theft. Users are redirected to fake banking websites to steal usernames and passwords.
- Malicious software distribution. Trojans or other malicious software is disguised as legitimate downloads to alter users' DNS settings.
- Compromised social media pages. Users are redirected from authentic-looking profiles to fake websites.
- Internet service provider-based attacks. Attackers target ISPs to redirect multiple users to pharming websites simultaneously.
- Router exploitation. Router configurations are changed to redirect all connected devices to malicious sites.
Signs of pharming
There are several signs that pharming might be taking place, including the following:
- A slightly different site link and appearance. Pharming websites look slightly different from legitimate sites. They might use different colors, logos or graphics in their attempt to trick users into thinking the site is safe to visit. In addition, the website URL might be slightly different. For example, a pharming site might have minor spelling errors.
- Authentication failures. Unsuspecting victims of a pharming attack might have difficulty logging in to familiar accounts and see unexpected redirects on webpages.
- Increased alerts and notifications. An increase in alerts and notifications from a website can be an indication of a pharming attack. These can include antivirus software alerts, such as frequent notifications about DNS or malware issues. Additionally, ISPs might alert users or organizations about potential pharming security breaches.
- An insecure connection. HTTPS is a widely adopted cybersecurity measure that encrypts data transmission between a web browser and a website. However, pharming scams continue to prey on unsuspecting users by luring them to insecure, fake websites. Pharming sites use a variety of tricks to appear legitimate, duplicating well-known logos and URL redirects. However, one commonality among insecure, fake sites is that they use http in their URLs instead of https, which is used in secure websites' URLs.
Protecting against pharming
There are many steps that users can take to prevent pharming and other malicious attacks from occurring, such as the following:
- Keep computers updated. Keeping a computer's operating system and other software updated is important for protecting against pharming. The latest software patches fix the vulnerabilities that hackers use to attack computers.
- Clear the browser cache. While surfing the internet, web browsers store information about the sites visited. If the same computer is used with a different internet connection, it's possible for a cyberattacker to access the computer's information. To avoid this problem, it's a good idea to clear the cache before using a new internet connection.
- Download antivirus and antimalware software. Using an antivirus program is an effective way to protect a computer from online threats and pharming. Attackers often use malware to exploit security vulnerabilities in operating systems and browsers. It often spreads using malicious code or links to malicious websites.
- Use HTTPS. This secure internet communication protocol encrypts data as it moves between web browsers and websites. HTTP, the protocol that HTTPS replaced, is less secure; it was designed before internet security risks increased.
- Use a virtual private network. A VPN hides IP addresses from websites and keeps hackers from stealing personal information. It creates an encrypted connection between a device and an organization's network, so even if the DNS is hijacked, sensitive information stays safe. A VPN service should have reputable DNS servers.
- Use bookmarks. Bookmarking frequently accessed sites and not clicking on links in emails or on social networking sites can reduce the chance of pharming.
Pharming vs. phishing
Pharming has been called "phishing without a lure." However, the two types of attacks are different.
Phishing
In phishing, the perpetrator sends out emails and instant or text messages that appear to come from some of the web's most popular sites. Phishers aim to obtain personal and financial information from individual recipients of those emails and messages.
Phishing is an attempt to extract sensitive information, such as usernames, passwords, social security numbers and credit card details, by masquerading as a trustworthy entity in an electronic communication. A phishing attack often directs users to enter details at a fake website that looks and feels almost identical to the legitimate one.
Phishing is a numbers game: If a hacker sends out 1 million phishing emails, they might get only a handful of responses, but those responses can be valuable. For example, a hacker might not get a large number of bank passwords from a single phishing email attempt, but if they get one response out of 10,000 potential victims, their scam succeeded.
Pharming
Pharming is a form of phishing that uses a DNS system to send a user to a fake website. Instead of sending an email that looks like it's from a user's bank, pharming directs victims to a website that looks like their bank's website.
Pharming can victimize larger numbers of computer users than phishing attacks because individuals aren't targeted one by one. In addition, pharming requires no conscious action on the part of the victim.
Famous pharming attacks
There have been several large-scale pharming attacks since the early 2000s:
- Rock Phish attacks. Active in the early 2000s, the Rock Phish group targeted banks and e-commerce websites. It was able to successfully redirect users to fake websites to collect their credentials.
- DNSChanger malware. This malware altered DNS settings on infected computers, redirecting victims to malicious websites. DNSChanger affected millions of users before being dismantled in 2012.
- Brazilian pharming campaigns. In 2015, several large-scale pharming attacks were carried out in Brazil. These exploited vulnerabilities in routers and DNS configurations to target online banking users and steal their credentials.
Pharming is a common form of cyberattack. Learn the 16 common types of cyberattacks and how to prevent them.








