What is a pass-the-hash attack?
A pass-the-hash attack is an exploit in which an attacker steals a hashed user credential and -- without cracking it -- reuses it to trick an authentication system into creating a new authenticated session on the same network.
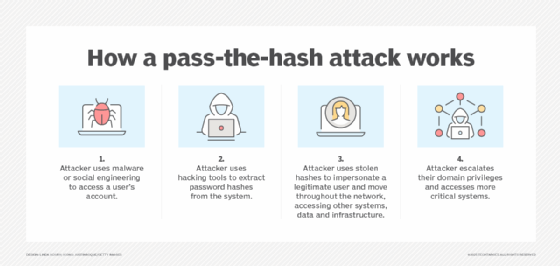
Pass the hash is primarily a lateral movement attack technique. This means that hackers compromise a user account or device to obtain a hash, which lets them extract additional information and credentials. By laterally moving between devices and accounts, attackers use pass the hash to gain the right credentials to eventually escalate their domain privileges and access more influential systems, such as an administrator account on the domain controller. Most of the movement executed during a pass-the-hash attack uses a remote software program, such as malware.
Typically, pass-the-hash attacks are directed at Microsoft Windows systems, but they can also work against other operating systems (OSes) in some instances and any authentication protocol, such as Kerberos. Windows is especially vulnerable to these attacks because of its single sign-on (SSO) function that lets users enter their password once to access all resources. SSO requires users' credentials to be cached within the system, making it easier for attackers to access.
How does a pass-the-hash attack work?
To execute a pass-the-hash attack, the attacker first obtains access to a user's account using malware or social engineering techniques, such as phishing. Then, the attacker accesses the hashes from the targeted system using any number of hash-dumping tools, such as fgdump and PWDump7. The attacker then uses these tools to place the obtained hashes on a Local Security Authority Subsystem Service (LSASS).
Pass-the-hash attacks are often directed at Windows machines due to the security vulnerability of the New Technology Local Area Network Manager (NTLM) hashes once admin privileges have been obtained. These attacks often trick a Windows-based authentication system into believing that the attacker's endpoint is that of the legitimate user and automatically provides the required credentials when the attacker tries to access the targeted system. This can all be accomplished without any need for the original password.
The NTLM hashes -- fixed-length mathematical codes derived from the passwords -- are the key to pass-the-hash attacks. They enable the attacker to use compromised domain accounts without extracting the plaintext password. This is because computer OSes, such as Windows, never send or save user passwords over their network. Instead, these systems store passwords as encrypted NTLM hashes, which represent the password but can't be reverse-engineered.
NTLM can still be used in place of the password to access various accounts and resources on the network. For an attacker to be able to access LSASS, they need to successfully compromise a computer to the point where the malware can run with local admin rights. This is one of the greatest obstacles for pass-the-hash attacks.
Once a Windows-based machine is compromised and the deployed malware is granted access to the local usernames and NTLM hashes, the attacker can choose whether to hunt for more credentials or attempt to access network resources using the credentials of elevated users.
For example, by gathering more user credentials, an attacker can retrieve the credentials of users who either have separate accounts on the Windows machine, such as a service account, or have remote access to the computer as a login administrator. Remote IT admins who log in to the compromised Windows machine expose their username and NTLM hash to the now-integrated malware. An attacker who has an IT administrator's credentials can move laterally through networked devices.
Lateral movement is an effective way to search for users with elevated privileges, such as administrative rights to protected resources. Privilege escalation can be obtained by finding the credentials of an administrator with greater administrative access. For example, a pass-the-hash attacker could locate the login credentials of the domain administrator through lateral movement. Recognizing their elevated privileges, hackers start running processes as a domain administrator on the domain controller. These elevated resources could also include customer databases, source code depositories and email servers.
Prior to Windows 10, there were few obstacles in the way of a hacker obtaining NTLM hashes from a compromised Windows machine. Windows 10 addressed these weaknesses by adding a security feature known as Microsoft Windows Defender Credential Guard. Using virtualization-based security technology, WDCG can isolate LSASS, allowing only trusted, privileged applications to access and interact with data. Virtualizing LSASS means that malicious applications can no longer access the NTLM hashes, even while they're running with full admin rights. And, while efforts have been made to safeguard NTLM hashes and LSASS in later versions, pass the hash is still a viable method of data breach that companies should be aware of.
In 2024, Microsoft deprecated the NTLM authentication protocol and advised developers to transition to more secure alternatives, such as Kerberos authentication. All versions of NTLM are no longer under active development, though NTLM is still functional in recent Windows versions.
What is a password hash?
A password hash is an encrypted form of a password. A password is made into a password hash by applying an algorithm that converts it into a string of fixed-length characters, making it difficult to render into plaintext form. While this is a common method used in password management and security, it has weaknesses that make it a prime target for cyberattacks.
In pass-the-hash attacks, cybercriminals exploit stolen password hashes instead of plaintext passwords. Once obtained, these hashes enable attackers to bypass the normal authentication process and access resources as if they were legitimate users. This makes hash-based authentication a critical vector for cyberthreats and credential theft in modern systems.
How to mitigate a pass-the-hash attack
There are several ways organizations can prevent and mitigate pass-the-hash attacks, such as the following:
- Implement multifactor authentication (MFA) that requires additional verification steps beyond passwords to ensure credentials alone can't grant access.
- Upgrade to secure protocols that include replacing NTLM with stronger options, such as the Kerberos authentication mechanism.
- Restrict privileged account access through privileged access management (PAM) and the principle of least privilege to control and monitor sensitive accounts.
- Secure Active Directory (AD) and Windows Server, and regularly monitor both systems.
- Enforce strong password management policies by using complex passwords and requiring regular password updates.
- Adopt a zero-trust model that assumes all users and devices could be compromised by credential theft, requiring verification at every step.
- Deploy advanced security solutions, such as firewalls, endpoint detection tools and network monitoring, to identify and block cyberthreats before they escalate.
Because pass the hash exploits the features and capabilities of the NTLM protocol, the threat of pass-the-hash attacks can't be eliminated completely. Once an attacker compromises a computer, pass the hash becomes one of many malicious activities that can be executed.
Unfortunately, there are many ways for hackers to remotely compromise a computer, and their attack methods are constantly evolving. For that reason, cybersecurity measures aren't 100% effective, and multiple mitigation techniques must be used simultaneously.
Recognizing that not all pass-the-hash attacks can be prevented, companies can try to improve their detection strategies, as well as their preventative measures. Workstation logs are one of the most common ways to reliably monitor administrative activity. These logs can track privilege assignments, as well as successful login attempts. Target server logs and domain controller logs are useful for the same reasons.
Who is vulnerable to a pass-the-hash attack?
Organizations using legacy protocols, like NTLM, or weak permissions structures are vulnerable to pass-the-hash attacks. Systems like AD, which store authentication data, are often targeted because of their centralized nature and the potential for lateral movement within a network. For example, a compromised domain admin account could grant an attacker unrestricted access to the organization's network.
High-value targets, such as privileged accounts and those with access to sensitive data, are especially at risk. Threat actors often use tools such as Mimikatz to extract password hashes from memory and execute a pass-the-hash attack. Organizations without strong defenses, like MFA or PAM, remain vulnerable to pass-the-hash attacks.
Pass-the-hash attacks are one of several cybersecurity threats. Get up to speed on cybersecurity planning for businesses.






