parameter tampering
What is parameter tampering?
Parameter tampering is a type of web-based cyber attack in which certain parameters in a URL are changed without a user's authorization. In some cases, the data entered by a user into a form field of a webpage may also be modified -- again, without the user's authorization. The attack may point the browser to a link, page or site that the user did not intend to access.
Parameter tampering explained
A parameter tampering attack targets a web application's business logic. It is employed by malicious users looking to exploit the application for their own benefit. Some attackers also use parameter tampering to launch a man-in-the-middle (MitM) attack.
Since the attack is based on manipulating the parameters exchanged between a client and server, it enables bad actors to modify application data, including user credentials, user permissions and even the number, quantity or price of products listed on a website.
This data, stored in URL query strings, hidden form fields, Hypertext Transfer Protocol (HTTP) headers or cookies, is required to expand a web application's control and functionality. However, through parameter tampering, a bad actor such as an identity thief can manipulate this data to surreptitiously obtain personal or business information about the user.
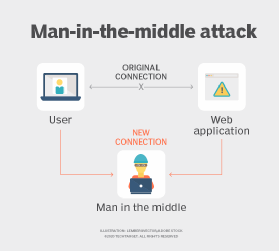
The impact of parameter tampering
The impact of parameter tampering depends on the type of parameter being manipulated. Four such parameters and their impact are explained below.
1. Impact of manipulating URL query strings
Query strings are typically used in web applications to pass data from the client to the server through parameters, add data calls to a hyperlink and display that information on the linked page.
Attackers may tamper with the URL query string to perform malicious actions, such as stealing data. By manipulating query strings, they can access information from a database, understand the architecture of a web application or even execute commands on the web server.
2. Impact of manipulating HTTP POST data
Since query strings are fairly simple, many web applications use the POST method to pass data between pages. POST data is not displayed by browsers, so it is considered a safe way to retrieve information. However, attackers can still modify the data to gain access to sensitive information.
3. Impact of manipulating HTTP headers
Headers are commonly used by HTTP requests and responses to deliver information about the HTTP message. A referer header is included in the HTTP request header. It contains the URL of the webpage from which the request originated and enables websites to identify the location of visitors. This data can be used to optimize caching and for analytics and logging.
Attackers can modify the referer header to make it look like it came from the original site. By submitting a malicious string, they can construct arbitrary HTTP responses and launch many kinds of attacks, including cross-user defacement or web and browser cache poisoning. They may also hijack pages or initiate cross-site scripting attacks.
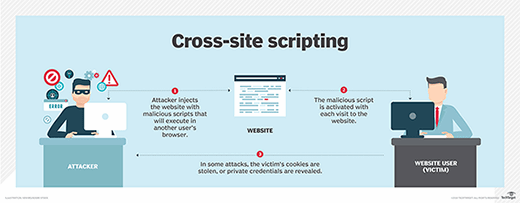
4. Impact of manipulating website cookies
A website cookie is a small piece of information stored in the web browser. The web server creates cookies to store user preferences and other data, such as timestamps and session tokens.
An attacker can modify or poison a cookie to bypass authentication in order to access a user's account and view, manipulate or exfiltrate sensitive data.
Preventing parameter tampering
Parameter tampering is especially common when applications are developed without properly validating the characters that will be accepted by the web application. Fortunately, it is possible to prevent such attacks by adopting secure programming techniques so that only expected data is accepted by the web application. If the application can't accept manipulated parameters, malicious actors won't be able to extract information from a database or execute arbitrary commands at the operating system level.
The application logic should be able to handle a situation when a parameter is either not passed or passed incorrectly. Further, when developing secure and stable code, developers should treat cookies the same as parameters.
Other ways to prevent parameter tampering include these practices:
- Clearly define the data type. Developers must define the specific data types, like string or alphanumeric characters, that the web application accepts. For instance, if a field is set to accept numbers, it should only be allowed to accept numbers and no other data type.
It's also important to define the maximum and minimum allowable data lengths for the application to ensure that bad actors can't manipulate data lengths to tamper with parameters. - Control parameter passing. Some applications need parameters to be passed to a dynamic webpage. But, if a particular parameter is omitted, the application should display an error message to the user. Also, developers should not automatically assume that a parameter is being passed before it is used in the application.
- Control parameters with incorrect format. Assuming that a parameter is in a valid format without verifying can create serious security gaps, especially if the parameter is passed to a Structured Query Language Also, the parameter's format may be incorrect even if the parameter is normally provided by a hidden field or combo box, enabling a hacker to alter the parameter and hack into the site. For these reasons, developers should always control parameters with incorrect formats.
- Never store critical data in hidden parameters. Critical data, such as product prices, order numbers, etc., should never be stored in hidden parameters or cookies since doing this can pose a major security risk and increase the possibility of a parameter tampering attack.
- Rigorous application testing. In addition to the above best practices, application testing is a crucial defense against parameter tampering. Developers and quality assurance testers must test the application, both from a user's and an attacker's perspective, to determine if there are weaknesses that must be addressed.
Manual testing by changing parameter values, modifying cookie values and using different data types in specific fields to see how the application performs can help identify parameters that are susceptible to manipulation and thus mitigate the risks of parameter tampering attacks.
In general, allowlisting, or accepting only allowable input, is a more effective way to prevent parameter tampering than blocklisting, or refusing to accept forbidden input. A web application firewall can also provide some protection against parameter tampering, provided that it is configured properly for the site in use.
Overall, the vulnerability of a computer or network to parameter tampering can be minimized by implementing a strict application security routine and making sure that it is kept up to date.
See also: session hijacking, proxy hacking, cache poisoning, IP spoofing, site scraper, content spoofing, ingress filtering, cyber hijacking and browser hijacking.








