out-of-band authentication
What is out-of-band authentication?
Out-of-band authentication is a type of two-factor authentication (2FA) that requires a secondary verification method through a separate communication channel along with the typical ID and password. Out-of-band authentication is often used in financial institutions and other organizations with high security requirements.
The fundamental principle behind out-of-band authentication is to introduce an additional layer of security using multiple, unrelated channels. These secondary channels can be a Short Message Service (SMS) text message, a push notification on a mobile device, a voice call or any other means of communication independent of the initial access point. The practice makes hacking an account more difficult because two separate and unconnected authentication channels would need to be compromised for an attacker to gain access.
How does out-of-band authentication work?
The process typically involves the following steps:
- Initial login. A user attempts to access a system or application, or tries to perform a sensitive transaction through the primary communication channel, such as a website or mobile app.
- Secondary verification request. After the initial login or transaction initiation, the system triggers a request for additional verification through a separate communication channel.
- Out-of-band delivery. The system sends a one-time code, also known as a one-time password (OTP), in the form of a push notification or other form of authentication prompt to the user's registered mobile device or different communication channel.
- User verification. The user receives the authentication prompt and provides the required information, such as entering the OTP or approving the push notification, through the separate channel.
- Access granted. Upon successful verification through both the primary and out-of-band channels, the system grants the user access or completes the requested transaction.
This multichannel approach provides identity and access management functionality that increases the difficulty for attackers to gain unauthorized access. They would need to compromise both the primary and secondary communication channels simultaneously, which is highly improbable.
Examples of out-of-band authentication
Out-of-band authentication can take various forms and apply to different use cases, depending on the specific implementation and the communication channels used. Methods of doing this type of authentication are cheaper to deploy than security key fobs or more complex biometric methods. Some of the most common examples include the following:
- SMS one-time passwords. Users receive a unique, time-sensitive code via SMS on their registered mobile phone, which they must enter to complete the authentication process.
- Mobile app push notifications. A dedicated mobile application sends a push notification to the user's device prompting them to approve or deny the login attempt or transaction.
- Voice calls. Users must make a phone call from a registered number or respond to an automatically generated phone call from the institution. The system initiates an automated voice call to the user's registered phone number, requiring them to press a specific key or provide a verbal response to confirm their identity. Voice recognition technology can be used to provide biometric verification.
- Hardware tokens. Physical devices, such as USB keys and smart cards, generate one-time codes or cryptographic challenges. They serve as an out-of-band authentication factor when used in conjunction with the primary login credentials.
- Software tokens. A software token, also known as a soft token, is generated by authenticator apps that provide single-use personal identification numbers (PINs) for authentication. They're made available via applications on computers and mobile devices.
- Biometric authentication. Using biometric factors such as voice, fingerprint or facial recognition on a separate device, such as a smartphone, dedicated hardware or security token, can serve as an out-of-band authentication method.
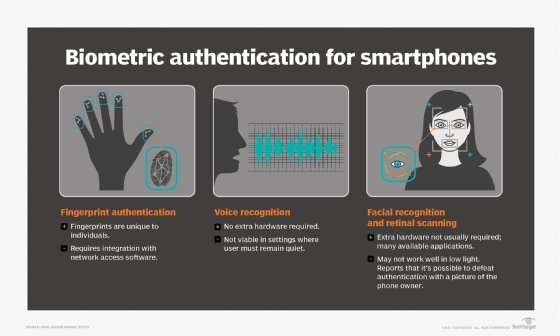
Who uses out-of-band authentication?
Out-of-band authentication has gained widespread adoption across various industries and sectors because of the strong security capabilities it provides. Industries where it's more likely to be used include the following:
- Financial services. Banks, credit card companies and other financial institutions use the technology to secure online transactions, wire transfers and high-value financial operations. It helps prevent fraud and unauthorized access to customer accounts in banking transactions and other financial application.
- E-commerce and online retailers. To safeguard sensitive customer information and prevent online banking fraud, e-commerce platforms often incorporate out-of-band authentication during checkout and account management processes.
- Healthcare. Medical and other healthcare-related organizations use out-band-authentication to ensure the privacy and security of patient data. It's used to protect electronic health records and sensitive medical information from unauthorized access.
- Enterprise organizations. Large companies often implement the technology to secure remote access to corporate networks and proprietary data, as well as to prevent unauthorized access to sensitive systems and applications.
- Government agencies. Federal and other government entities handling confidential data such as tax records and classified information rely on out-of-band authentication to enhance data security and protect against cyberattacks and data breaches. Data breaches cost on average $4.45 million U.S., according to IBM's "Cost of a data breach report 2023" conducted by Ponemon Institute.

Benefits and drawbacks of out-of-band authentication
The technology comes with its own set of advantages and potential drawbacks.
Benefits
- Enhanced security. By introducing an additional layer of verification through a separate communication channel, out-of-band authentication reduces the risk of successful cyberattacks, such as phishing and man-in-the-middle attacks.
- Versatility. The technology can be implemented using various communication channels such as SMS, mobile apps, voice calls and hardware tokens. This lets organizations choose the most suitable method for their users and security requirements.
- Compliance. Many regulatory bodies and industry standards mandate the use of multifactor authentication, such as out-of-band authentication.
- Ease of use. By using familiar communication channels like mobile devices, this type of authentication technology provides a relatively seamless user experience, eliminating the need to remember complex passwords or carry dedicated hardware tokens.
Drawbacks
- Threat actors. Criminals can circumvent out-of-band authentication. For example, a hacker might attempt to substitute their phone number for a customer's on a bank account. In this case, the technology's effectiveness depends on the bank adhering strictly to policies against making changes to an account without phone confirmation or transferring money without that extra authorization.
- Mobile devices. Smartphones in particular can be a weak spot in out-of-band-authentication. If people use the same phone for web banking that they use for SMS authentication, they're nullifying the effectiveness of the secondary measure. In either case, the effectiveness of the authentication technology relies upon adherence to the proper procedures.
- Dependence on communication channels. The technology relies heavily on the availability and reliability of the communication channels used. Disruptions or delays in these channels can impact the authentication process and user experience.
- Potential channel vulnerabilities. Introducing an additional communication channel enhances security but also introduces a new attack surface. Attackers can compromise the out-of-band channel itself by intercepting SMS messages or exploiting vulnerabilities in mobile applications.
- User adoption challenges. Users might resist adopting this type of authentication technology because of the perception that it's inconvenient or they aren't familiar with the separate communication channel being used. Proper user education and training are essential for successful implementation.
- Cost and implementation complexity. Deploying this sort of authentication technology across an organization can be costly and complex, especially for large-scale implementations. It might require additional infrastructure, integration with existing systems and ongoing maintenance and support.
Other authentication methods
While out-of-band authentication offers strong security, it isn't the only authentication method available. Other types of authentication methods include the following:
- Single-factor authentication. SFA is a traditional method that relies solely on a single factor, such as a password or PIN. Out-of-band authentication provides an extra layer of cybersecurity by introducing a separate communication channel, making the system or application more resilient against attacks.
- Two-factor authentication. 2FA combines two different authentication factors such as a password and a one-time code sent via SMS or generated by a dedicated app. While 2FA enhances security compared to single-factor authentication, out-of-band authentication goes further, using separate communication channels, reducing the risk of both factors being compromised simultaneously.
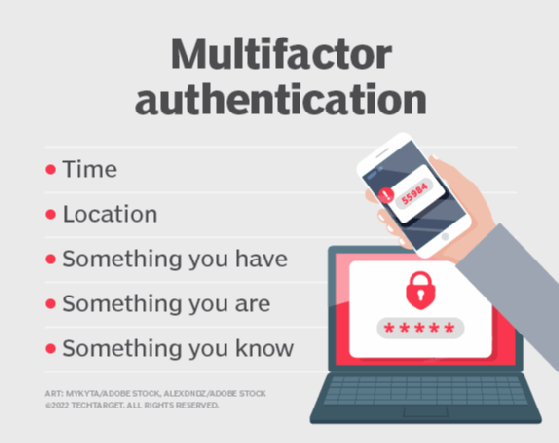
- Multifactor authentication. MFA involves combining two or more independent authentication factors such as a password, hardware token and a biometric factor. Out-of-band authentication can be considered a form of MFA when implemented using multiple communication channels, providing an additional layer of security beyond traditional MFA implementations.
- Risk-based authentication. RBA dynamically adjusts the authentication requirements based on the assessed risk level of a particular login attempt or transaction. Out-of-band authentication can be integrated into a risk-based authentication framework, serving as an additional verification step for high-risk scenarios or transactions deemed potentially fraudulent.
Out-of-band authentication is a popular security and risk management method. Learn the core steps in enterprise risk management.








