one-time pad
What is a one-time pad?
In cryptography, a one-time pad is a system in which a randomly generated private key is used only once to encrypt a message that is then decrypted by the receiver using a matching one-time pad and key.
Messages encrypted with keys based on randomness have the advantage that there is theoretically no way to break the code by analyzing a succession of messages. Each encryption is unique and bears no relation to the next encryption, making it impossible to detect a pattern. But with a one-time pad, the decrypting party must have access to the same key used to encrypt the message; this raises the issue of how to get the key to the decrypting party safely, or how to keep both keys secure.
One-time pads have been used when both parties started out at the same physical location and then separated, each with knowledge of the keys in the one-time pad. The key used in a one-time pad is called a secret key because if it is revealed, the messages encrypted with it can be deciphered easily. One-time pads figured prominently in secret message transmission and espionage before and during World War II and in the Cold War era. On the internet, the difficulty of securely controlling secret keys led to the invention of public key cryptography.
How does a one-time pad work?
Typically, a one-time pad is created by generating a string of characters or numbers that will be at least as long as the longest message that will be sent. This string of values is generated in some random fashion, such as by using a computer program with a random number generator. The values are written down on a pad or on any device that someone can read. The pads are given to anyone who is likely to send or receive a sensitive message. Typically, a pad may be issued as a collection of keys -- one for each day in a month, for example, with one key expiring at the end of each day or after it has been used once.
When a message is to be sent, the sender uses the secret key to encrypt each character one at a time. If a computer is used, each bit in the character -- which is usually eight bits in length -- is exclusively OR'ed with the corresponding bit in the secret key. With a one-time pad, the encryption algorithm is simply the XOR operation. When there is some concern about how truly random the key is, it is sometimes combined with another algorithm, such as MD5. This kind of encryption can be considered 100% noise source used to mask the message, and only the sender and receiver have the means to remove the noise. Once the one-time pad is used, it cannot be reused. If it is reused, someone who intercepts multiple messages can begin to compare them for similar coding for words that may occur in several messages.
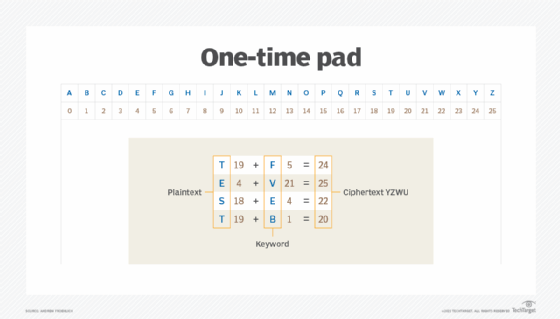
A simple example of how a one-time pad works is shown in the example below. Here, we have a plaintext message of TEST. We also have a random secret key of FVEB, which is the same length as the message sent. Using the simple process of assigning a letter to a number, the plaintext message can be translated to 19, 4, 18 and 19. Using this same conversion method for the secret key, we get 5, 21, 4 and 1. Adding the two together, we get 24, 25, 22 and 20; when converted back to alphabetic letters, this gives us an encrypted message of YZWU. This message can then be decrypted by reversing the steps.
How is one-time pad used?
Although a one-time pad is truly the only unbreakable encryption method, its use is impractical for many modern applications because the system must meet the following conditions:
- The key must be the same size as the message being sent.
- The key must be truly random.
- Keys must never be reused.
- Keys must be securely shared between the sending and receiving parties.
Because of these strict conditions, the use of one-time pad over digital media is impracticable. The most challenging conditions reside in generating truly random keys, the inability to reuse a key and sharing those keys with the receiving party. Because of the distributed nature of computer networks and how data is shared on the global internet, other encryption mechanisms are better suited, although less secure in practice. The one-time pad has been relegated to being an interesting encryption method that was successfully used in a pre-technology era.
What is the difference between a one-time pad and a stream cipher?
In many regards, a one-time pad is a stream cipher if certain conditions are met. However, not all stream ciphers can be one-time pads. The reason for this is simple; a one-time pad requires that the key length be at least as long or longer than the message being sent. The definition of a stream cipher, however, does not have this length condition. This means that a stream cipher could be encrypted with a key shorter than the length of the message, which is inherently less secure.
Learn how organizations must adopt stronger and more secure authentication methods if they want to take advantage of IoT.






