cryptographic nonce
What is a nonce?
A nonce is a random or semi-random number that is generated for a specific use. It is related to cryptographic communication and information technology (IT). The term stands for "number used once" or "number once" and is commonly referred to as a cryptographic nonce.
Typically, a nonce is a value that varies with time to verify that specific values are not reused. A nonce can be a timestamp, a visit counter on a webpage or a special marker intended to limit or prevent the unauthorized replay or reproduction of a file.
What are other meanings of nonce?
In general usage, outside of computer science and IT, nonce has several meanings. They include the following:
- Nonce can mean "for the immediate occasion" or "for now."
- A nonce word is a neologism -- newly coined word or expression -- that is created for a single use, such as inclusion in a work of fiction. Once created, nonce words often make their way into common language. For example, Lewis Carroll coined the word "chortle" for the poem Jabberwocky, and James Joyce created the word "quark" for his novel Finnegans Wake.
- Nonce orders are an architectural term describing one-off custom designs or spinoffs of classical orders or design conventions in architecture.
- A nonce is also British slang for a pedophile.
Types of nonce values
A nonce can be categorized based on how it is generated, either randomly or sequentially. A random nonce is produced by stringing arbitrary numbers together. A sequential nonce is produced incrementally. Using the sequential nonce method guarantees that values are not repeated, cannot be replayed and do not take up unnecessary space.
Using the random nonce method safeguards against attackers that collect several keys within a system. Ideally, a nonce will have both random and sequential parts.
For example, a timestamp of 3:01 p.m. 9/17/2020 would be a sequential nonce, because it is produced incrementally. It is highly unlikely that value had occurred before or would ever occur again. It is somewhat predictable. A hacker could learn the pattern that timestamped keys are generated and guess the value of the next one.
A pseudo-random number generator can produce more unpredictable nonces. However, it would be less likely to be unique because there is a chance that the same random number could be generated more than once.
How to use a nonce
Nonce values can be used for a variety of IT applications, including the following:
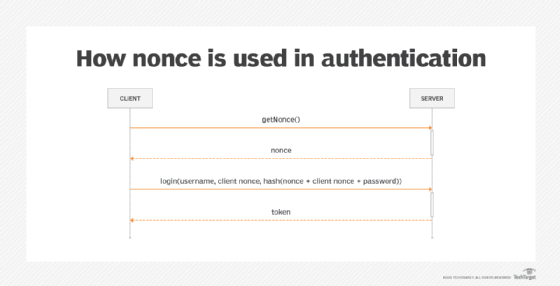
- Authentication. Nonce is used by authentication protocols to ensure that old communications cannot be reprocessed.
- Hashing. Proof of work systems use nonce values to vary input to a cryptographic hash function. This helps fulfill arbitrary conditions and provide a desired difficulty.
- Initialization. An initialization vector is a nonce used for data encryption. It is used only once in any session and prevents a repetition of sequences in encrypted text. Identifying repetitions can help an attacker break a cipher.
- Identity management. Account recovery, two-factor authentication or single sign-on are identity management features that can use nonce values.
- Electronic signatures. Secret nonce values are sometimes used by e-signature tools to create, compare and verify signatures.
- Cryptocurrency. In certain cryptocurrencies, a nonce is used to create a cryptographic hash that connects to a blockchain. In Bitcoin mining, a golden nonce refers to a hash value that is lower than the target difficulty.
- Asymmetric cryptography. In specific instances of public key cryptography, such as in the Secure Socket Layer/Transport Layer Security handshake, two unique nonce values are exchanged. One value is provided by the client while the other is provided by the server. This is called asymmetric cryptography, and it protects each connection from attacks or interventions.
Cryptographic nonce example
Cryptographic nonce is used in authentication protocols to defend against replay attacks. Replay attacks are when an attacker intercepts authentication data in transit and uses it later to gain access to the protected network.
E-commerce sites typically use a nonce to assign originality to each purchase. Without this, an attacker could potentially replay the encrypted information as many times as desired and place additional orders using the same account name and purchase information.
E-commerce provider PayPal uses nonces in its encryption scheme to send sensitive payment information. This helps the company comply with the Payment Card Industry Data Security Standard.
Nonce use in cryptocurrency
Cryptocurrencies use blockchain mining, a peer-to-peer process to maintain the security and authenticity of the blockchain ledger. As part of the process, blockchain miners record digital currency transactions and create new Bitcoins or other cryptocurrencies. Miners validate the trustworthiness of transactions and add new transaction data to the global public ledger of past transactions, creating the blockchain.
Miners use sophisticated software and algorithms to solve complex problems. The first miner to solve a problem receives a new block of the cryptocurrency they are working with. Nonce is the arbitrary number that miners must come up with -- essentially guess -- to produce a number less than or equal to the target hash.
Solving for the nonce requires trial and error because it is a random string. Miners will guess the nonce, add it to the to the hash of the current block header, rehash the value and see if it is less than or equal the value of the target hash.
Learn about four different blockchain network types and their uses in the enterprise.







