man in the browser (MitB)
What is man in the browser (MitB)?
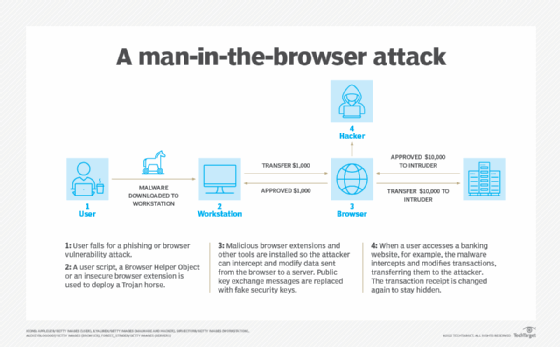
Man in the browser (MitB) is a cybersecurity attack where the perpetrator installs a Trojan horse on the victim's computer that is capable of modifying that user's web transactions. The purpose of a man-in-the-browser attack includes eavesdropping, data theft or session tampering. This attack method may be used in cases of financial fraud, where perpetrators manipulate internet banking services and change transaction verifications to gain monetarily from the victims.
Specifically, a man-in-the-browser attack is a type of man-in-the-middle (MitM) attack. MitM attacks secretly intercept and relay messages between two parties who believe they are communicating directly with each other. MitM attacks are a type of eavesdropping in which the entire conversation is controlled by the attacker.
Because man-in-the-browser attacks require the installation of Trojan malware on the target computer, perpetrators commonly take advantage of security vulnerabilities or phishing tactics to initiate the attack. MitB attacks are deployed via user script, a Browser Helper Object or an insecure browser extension. MitB works by infecting a browser with a Trojan horse, which enables an attacker to intercept and modify data sent from a browser to a server. Messages in a public key exchange are also intercepted and replaced with fake security keys, and malicious browser extensions can be installed.
A man-in-the-browser attack occurs when the victim has entered the URL into the browser independently, without an external prompt. On the surface, transactions are taking place normally with expected prompts and password requirements.
When an MitB attack is successful, the perpetrator can steal a user's data and money. The attack can also change the appearance of a website and change server responses.
Examples of man-in-the-browser attacks
Some past examples of man-in-the-browser cyber attacks include the following:
- Zeus is an MitB attack that steals online banking credentials and conducts unauthorized fund transfers. It has also been used to execute technical support scams. Attacks have been successful on Firefox and Internet Explorer (IE) web browsers and have targeted Amazon, Bank of America, the U. S. Department of Transportation and Cisco accounts. Man-in-the-browser attacks can also occur on mobile devices. Zeus in the mobile is one example.
- OddJob is an MitB attack designed to be used against banking websites. The attack is installed through Firefox or IE and activates when the infected user opens a banking website. The attack targets the user's real-time session ID token in order to make bank account transactions. The attack is hard to detect because it is not stored on the device's disk.
- SpyEye is a Trojan that prompts a user for information such as banking accounts, passwords, usernames or credit card numbers. It affects multiple web browsers, including Google Chrome, Firefox, IE and Opera. The attack can also operate as a keylogger. SpyEye in the mobile is another example of an MitB mobile device attack targeting Android users.
What are some key signs of a man-in-the-browser attack?
Man-in-the-browser attacks are difficult to detect. Even though a webpage is created or changed by the attacker, the webpage's URL may be correct, and the webpage itself may look similar to the intended page.
Some possible signs that may indicate an MitB attack, however, include the following:
- The user's antivirus software detects malware.
- The user is suddenly logged out of an account.
- The user receives login notifications from locations away from their device.
- There are missing or extra elements on a webpage.
How to prevent man-in-the-browser attacks
Although man-in-the-browser attacks are hard to detect, they are still preventable. Ways to prevent these attacks include the following:
- Be wary of phishing emails. Because phishing is a main method involved in initiating an MitB attack, users should know how to protect themselves from potential attempts.
- Use antivirus or security software. Antivirus programs that can detect Trojans and MitM attacks can also detect MitB attacks. Mimecast and Codesealer are two programs that can detect MitB attacks.
- Use out-of-band authentication. Out-of-band authentication is a type of two-factor authentication that requires a secondary verification method through a separate communication channel along with a typical ID and password. Out-of-band authentication makes hacking an account more difficult. However, this method is not 100% reliable because some Trojans can intercept incoming text messages, too.
- Be aware of potentially malicious websites. Users should ensure they are on a webpage with the correct corresponding URL and nothing on the website is out of place or changed.
- Use a virtual private network. A VPN obscures network traffic being transmitted or received and limits the hacker's ability to modify traffic.
Are there other threats similar to man-in-the-browser attacks?
A man-in-the-browser attack is similar to, and is classified as, a MitM tactic in which an attacker intercepts messages in a public key exchange. The attacker then retransmits them, substituting bogus public keys for the requested ones. An MitB attack is more difficult to prevent and disinfect, however, because, instead of occurring in a public exchange, the activity takes place between the user and the browser security mechanisms.
Boy-in-the-browser (BitB) attacks are a variant of MitB attacks where the attacker uses malware to change the user's computer network routing. After routing, the malware removes itself to make the BitB attack harder to detect.
Browser-in-the-browser attacks are another similar attack that attempts to simulate a browser window in a browser to spoof a legitimate domain. The goal of this type of attack is to successfully stage convincing phishing attacks.
Learn more about how to avoid getting hooked by phishing attacks -- the main way attackers bring MitB attacks to victims.








