What is a denial-of-service attack?
A denial-of-service (DoS) attack is a security threat that occurs when an attacker makes it impossible for legitimate users to access computer systems, networks, services or other IT resources. Attackers typically flood web servers, systems or networks with traffic that overwhelms the victim's resources, making it difficult or impossible for anyone else to access them.
Restarting a system usually fixes an attack that crashes a server, but recovering from flooding attacks is more difficult. Recovering from a distributed DoS (DDoS) attack in which attack traffic comes from many sources is even more difficult.
DoS and DDoS attacks often take advantage of vulnerabilities in networking protocols and how they handle network traffic. For example, an attacker might overwhelm the service by transmitting many packets to a vulnerable network service from different Internet Protocol (IP) addresses.
How does a DoS attack work?
DoS and DDoS attacks target one or more of the seven layers of the Open Systems Interconnection (OSI) model. The most common OSI targets include Layer 3 (network), Layer 4 (transport), Layer 6 (presentation) and Layer 7 (application).
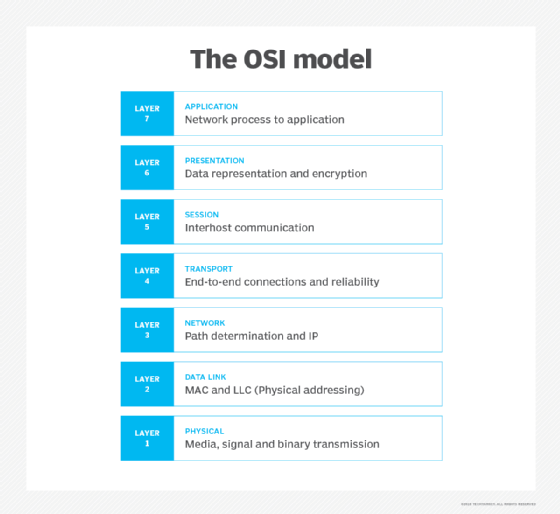
Malicious actors have different ways of attacking the OSI layers. One common way is using User Datagram Protocol (UDP) packets. UDP speeds transmission transferring data before the receiving party sends its agreement. Another common attack method is SYN, or synchronization, packet attacks. In these attacks, packets are sent to all open ports on a server, using spoofed, or fake, IP addresses. UDP and SYN attacks typically target OSI Layers 3 and 4.
Protocol handshakes launched from internet of things (IoT) devices are commonly used to launch attacks on Layers 6 and 7. These attacks can be difficult to identify and preempt because IoT devices are everywhere and each is a discrete intelligent client.
Signs of a DoS attack
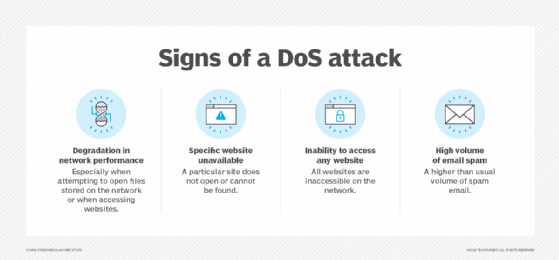
The U.S. Computer Emergency Readiness Team, also known as US-CERT, provides the following guidelines for detecting a possible DoS attack in progress:
- Slower or otherwise degraded network performance that's particularly noticeable when trying to access a website or open files on the network.
- Slow website loading times.
- Inability to access a website.
- Unexplained amounts of traffic
- Out-of-nowhere spikes in network traffic.
- Increased CPU usage.
- More spam email than usual.
Preventing a DoS attack
Experts recommend several strategies to defend against DoS and DDoS attacks, starting with preparing an incident response plan well in advance.
An enterprise that suspects a DoS attack is underway should contact its internet service provider (ISP) to determine whether slow performance or other indications are from an attack or some other factor. The ISP can reroute the malicious traffic to counter the attack and use load balancers to mitigate the severity of the attack.
ISPs also have products that detect DoS attacks, as do some intrusion detection systems, intrusion prevention systems and firewalls. Other strategies include contracting with a backup ISP and using cloud-based anti-DoS measures.
There have been instances where attackers have demanded payment from victims to end DoS or DDoS attacks, but financial profit isn't usually the motive behind these attacks. In many cases, the attackers want to harm the business or reputation of the organization or individual targeted in the attack.
Mitigating a DoS attack
Mitigating a DoS attack requires differentiating between normal network traffic and traffic from an attack. This can be challenging, depending on the nature and complexity of the attack. There are several methods for making the distinction, including the following:
- Rate limiting. This reduces or limits the number of requests a server accepts in a given amount of time. This method can help slow down hackers by making their job more difficult.
- Web application firewall. A WAF protects a specific server and allows users to create customized rules that are particularly effective against Layer 7 attacks.
- Network diffusion. Where the architecture allows, effective mitigations include diffusion, which spreads requests throughout a network, making them less likely to pile up on top of a targeted server.
- Blackhole routing. This method redirects potentially malicious traffic into a null route, effectively shutting down the network. Although this should be used as a last resort, it does keep cybercriminals out.
Types of DoS attacks
DoS and DDoS attacks can be carried out in various ways. Common types of denial-of-service attacks include the following:
- Application layer. These attacks generate fake traffic to internet application servers, especially domain name system (DNS) servers or Hypertext Transfer Protocol (HTTP) servers. Some application layer DoS attacks flood the target servers with network data; others target the victim's application server or protocol, looking for vulnerabilities.
- Buffer overflow. This type of attack sends more traffic to a network resource than it was designed to handle.
- DNS amplification. In a DNS DoS attack, the attacker generates DNS requests that appear to have originated from an IP address in the targeted network and sends them to misconfigured DNS servers managed by third parties. The amplification occurs as the intermediate DNS servers respond to the fake DNS requests. The responses from intermediate DNS servers to the requests might contain more data than ordinary DNS responses, which require more resources to process. This can result in legitimate users being denied access to the service.
- Protocol attacks. Protocol attacks seek to render a target inaccessible. They achieve this by consuming excessive server resources in firewalls and load balancers, creating service disruptions through what is known as state exhaustion.
- Cloud-based attacks. In this class of cyberattacks, the cybercriminal's goal is to exploit cloud-centric system vulnerabilities and cloud resources. The attack can focus on the hypervisor layer -- which manages virtual machine resources -- and install false components. Variations of this approach include hypervisor attacks, hypercall attacks, hyperjacking and cryptojacking.
- Ping of death. These attacks abuse the ping protocol by sending request messages with oversized payloads, causing the target systems to become overwhelmed, stop responding to legitimate requests for service and possibly crash the victim's systems.
- State exhaustion. These attacks -- also known as Transmission Control Protocol (TCP) attacks -- occur when an attacker targets the state tables held in firewalls, routers and other network devices and fills them with attack data. When these devices incorporate stateful inspection of network circuits, attackers might be able to fill the state tables by opening more TCP circuits than the victim's system can handle at once, preventing legitimate users from accessing the network resource.
- SYN flood. This attack abuses the TCP handshake protocol the client uses to establish a TCP connection with a server. In a SYN flood attack, the attacker directs a high-volume stream of requests to open TCP connections with the victim server with no intention of completing the circuits. A successful attack can deny legitimate users access to the targeted server.
- Teardrop. These attacks exploit flaws similar to how older operating systems (OSes) handled fragmented IP packets. The IP specification enables packet fragmentation when the packets are too large to be handled by intermediary routers, and it requires packet fragments to specify fragment offsets. In teardrop attacks, the fragment offsets are set to overlap each other. Hosts running affected OSes are then unable to reassemble the fragments, and the attack can crash the system.
- Volumetric. These DoS attacks use all the bandwidth available to reach network resources. To do this, attackers must direct a high volume of network traffic to the victim's systems. Volumetric DoS attacks flood a victim's devices with network packets using UDP or Internet Control Message Protocol. These protocols require little overhead to generate large volumes of traffic, while at the same time, the victim's network devices are overwhelmed with network packets trying to process the incoming malicious datagrams.
What is DDoS and how does it compare to DoS?
Many high-profile DoS attacks are actually distributed attacks, meaning the attack traffic comes from multiple attack systems. DoS attacks originating from one source or IP address can be easier to counter because defenders can block network traffic from the offending source. Attacks from multiple attacking systems are far more difficult to detect and defend against. It can be difficult to differentiate legitimate traffic from malicious traffic and filter out malicious packets when they're being sent from IP addresses seemingly located all over the internet.
In a DDoS attack, the attacker might use computers or other network-connected devices that have been infected by malware and made part of a botnet. DDoS attacks use command-and-control servers (C&C servers) to control the botnets that are part of the attack. The C&C servers dictate what kind of attack to launch, what types of data to transmit, and what systems or network connectivity resources to target with the attack.
History of denial-of-service attacks
DoS attacks on internet-connected systems have a long history that arguably started with the Robert Morris worm attack in 1988. In that attack, Morris, a graduate student at the Massachusetts Institute of Technology, released a self-reproducing piece of malware -- a worm -- that quickly spread through the internet and triggered buffer overflows and DoS attacks on the affected systems.
Those connected to the internet at the time were mostly research and academic institutions, but it was estimated that as many as 10% of the 60,000 systems in the U.S. were affected. Damage was estimated to be as high as $10 million, according to the U.S. General Accounting Office, now known as the Government Accountability Office. Prosecuted under the 1986 Computer Fraud and Abuse Act, Morris was sentenced to 400 community service hours and three years' probation. He was also fined $10,000.
DoS and DDoS attacks have become common since then. Some recent attacks include the following:
- Multiple-target Rapid Reset attack. In 2023, Amazon Web Services (AWS), Cloudflare and Google all experienced record-breaking DDoS attacks from an army of small botnets using new attack methods. They exploited an HTTP/2 feature for request cancellation, overwhelming servers with a flush of opening and closing streams.
- Google. In October 2020, Google experienced a UDP amplification attack sourced from several Chinese ISPs -- the largest bandwidth cyberattack it had ever experienced. The attack included a multinetwork spoof of 180,000 Simple Mail Transfer Protocol, DNS and Connectionless Lightweight Directory Access Protocol (CLDAP) servers, triggering an overwhelming deluge of responses.
- AWS. In the AWS Shield Threat Landscape Report Q1 2020, the cloud service provider said it mitigated one of the largest DDoS attacks it had ever seen in February 2020. It was 44% larger than anything AWS had ever encountered. The volume of the attack was 2.3 terabytes per second, and it used a type of UDP vector known as a CLDAP reflection. Amazon said it used its AWS Shield to counter the attack.
An email security gateway can help organizations protect against cyberattacks. Learn what features to look for, what the leading providers offer, and tips for avoiding email security threats.






