logon (or login)
What is a logon (or login)?
In computing, a logon is a procedure that enables an entity to access a secure system such as an operating system, application, service, website or other resource. The entity is typically an end user, although it can also be another system, such as a computer, service or application. For example, a logon process is usually carried out when an application accesses a database. In such cases, the logon operation occurs behind the scenes, without user intervention beyond the initial setup.
The system that users sign in to is often on a local device such as a desktop or smartphone. For example, users commonly log on to their PCs after rebooting them or when opening secure applications that require additional authentication, such as a password management utility. The target system might also be a networked resource, such as a file share on a local area network or a cloud service accessed via the internet. In such scenarios, a user might participate in one or more logon events when establishing a connection, although some of those events will be hidden from the user.
How the logon process works
Traditionally, the logon process requires a user to enter an ID and password into an interface when signing in to a secure system. Each system has its own credential requirements. For example, a system might require that the user ID is in the form of an email address, or that it is made up of only alphanumeric characters and conforms to a minimum and maximum length.
A password might have similar requirements in terms of character type and length, but it also usually comes with other restrictions. For example, the password might need to include at least one uppercase letter, one lowercase letter, one number and one special character, such as *, @, !, & or $. Most systems mask the password as the user types it into the interface to ensure it cannot be read by a nearby individual or device.
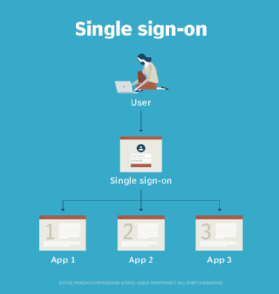
Single sign-on (SSO) is an authentication method that simplifies logging in to multiple systems and applications by enabling users to use the same password for each. Based on federated identity management principles, SSO eases the management of multiple credentials. On the internet, SSO uses the Open Authorization framework to act as an intermediary for end users so that their passwords are not exposed.
Other logon methods
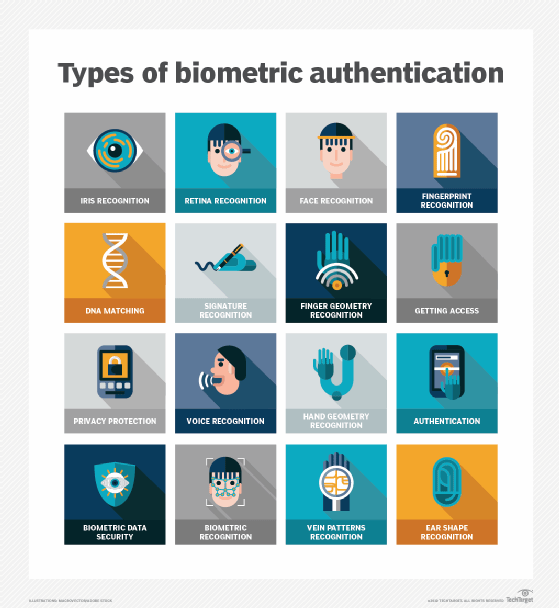
The ID and password method is not the only approach to system logon. Many devices now include biometric features that make it possible to scan a user's physical characteristics -- known as biometric authentication -- as part of the logon process, rather than requiring an ID and password. For example, a laptop or tablet might scan a user's fingerprint or facial features, and then compare those with the digital characteristics on file. If there's a match, the logon process can proceed.
Another alternative is the smart card, which can also initiate a logon without requiring an ID and password. In this case, the user inserts a smart card into a reader connected to the device. The user will then be able to access specific resources on the device, on the network or both, depending on the type of smart card support available to that device and how the service has been configured.
Logon, login, log on, log in
The term logon is often used interchangeably with the term login, even though many sources distinguish between the two -- or at least show preference for one over the other. There is no industry consensus or standard on either term's usage, and much of it comes down to the preference of individual communities, vendors or people. This has resulted in a mishmash of approaches to sign-in terminology, leading to a fair amount of inconsistency and, at times, confusion.
Microsoft and others in the Windows community have tended to favor the term logon, particularly as it applies to the authentication and authorization mechanisms that govern both local and network access. Microsoft has also been steadily moving toward the terms sign in and sign out when referring to session-level access of any kind. However, the term login also pops up in some Microsoft products. For example, SQL Server includes a type of security principal called the login, which has a very specific meaning within the context of that product.
The Unix world, which includes Unix-like operating systems such as Linux, macOS, iOS and Android, has tended to favor the term login, with most of the official documentation sticking along these lines. Outside of these more controlled spheres, however, applications, websites, online services and the population at large tend to use the terms logon and login -- along with such terms as sign-in or sign-on -- without any apparent uniformity or agreement across the technical landscape.
Another source of confusion surrounds the use of logon for different parts of speech. In this area, too, usage is inconsistent. However, the guidelines are fairly straightforward. When used as a noun or adjective, the term should be one word, as in "the user logon" or "the logon procedure." When used as a verb, the term should be two words, as in "you must log on" or "the user is still logged on." The term login follows the same guidelines. It is treated as one word when used as a noun or adjective, and two words when used as a verb.
Learn how to create account lockout policies that detail how many unsuccessful login attempts are allowed before lockout. See how to filter security log events for signs of trouble.








