encryption key
What is an encryption key?
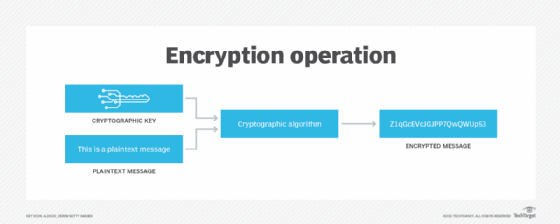
In cryptography, an encryption key is a variable value that is applied using an algorithm to a string or block of unencrypted text to produce encrypted text or to decrypt encrypted text. The length of the key is a factor in considering how difficult it will be to decrypt the text in a given message.
A strong encryption key is typically a randomly generated sequence of bits that is not easily guessed. The length of the encryption key determines how susceptible it is to a brute-force attack, where an attacker tries out different keys until the right one is found.
How does an encryption key work?
Encryption algorithms are implemented in software. They encrypt data by applying a key to unencrypted data. Ciphertext results from that process. It is protected from unauthorized access and is accessible only to users or software that have the proper decryption key.
Encrypted data is decrypted when the encryption algorithm applies the correct key to the ciphertext.
Asymmetric encryption vs. symmetric encryption
There are two main types of encryption: symmetric and asymmetric. They are distinguished by the number of keys they use.
Symmetric encryption
Secret key encryption, also known as symmetric encryption, uses a single key to encrypt and decrypt data. This type of encryption is symmetric because the same key is used to encrypt plaintext into ciphertext and decrypt that ciphertext back into plaintext.
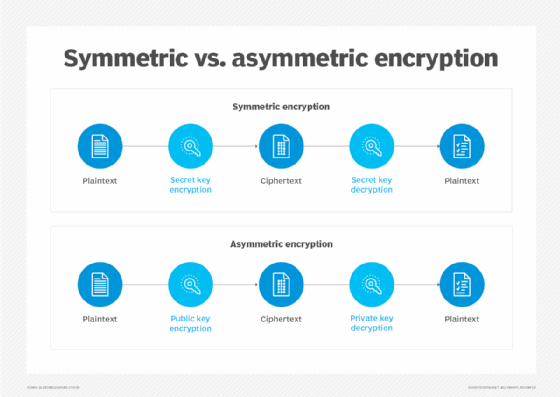
Asymmetric encryption
Public key cryptography, also referred to as asymmetric cryptography, uses public key pairs. One of the paired keys is public, and the other is private. Each of these keys can transform plaintext into encrypted ciphertext -- but ciphertext encrypted with one of the keys can only be decrypted with the other key.
When the public key is used to encrypt ciphertext, that text can only be decrypted using the private key. This enables anyone with access to the public key to encrypt a plaintext message, which only the private key holder will be able to decrypt. This is how private messages can be sent without exchanging a shared secret key.
Text encrypted with the private key can only be decrypted using the public key. This is how a digital signature is created. A ciphertext encrypted with a private key is decrypted using the public key to authenticate the signature.
Public keys are published in publicly accessible repositories, where anyone who needs to communicate with public key pair holders can access them. The key pair owner is the only one who can hold the private key. It must remain secret, or else the key pair can't be trusted to authenticate the owner.
What does an encryption key do?
Encryption keys represent a data variable used to control how an algorithm processes plaintext into ciphertext and back.
For symmetric ciphers, the encryption key should be accessible only to users who are authorized to access the encrypted data. For asymmetric encryption algorithms, which use pairs of encryption keys, the public key is intended to be shared and need not be kept secret. However, the key pair owner should never share the private key.
How are encryption keys created?
Passwords have their limitations. They are usually limited to characters accessible from a computer keyboard. On the other hand, cryptographic keys can consist of any string of bits. Such strings may be rendered in human-accessible character sets, if necessary.
Factors that affect the strength of a key include the following:
- key length;
- entropy or randomness; and
- strength of key management -- storage, creation and exchange.
Acceptable key length varies depending on the encryption algorithm in use. Truly random keys are more resistant to attacks. However, in all cases, strong encryption key management strategies are essential for creating and using keys securely.
Length
For the same encryption algorithm, a longer key is better than a shorter one to secure encrypted material against brute-force attacks. As attackers use more powerful computers, the required key lengths grow longer.
Over the years, acceptable key length matches have grown in tandem with computer power. For example, in the early 1990s, the first secure web servers used 40-bit keys to encrypt data; by 2015, the National Institute of Standards and Technology (NIST) recommended a minimum key length of 2,048 bits for use with the RSA, or Rivest-Shamir-Adleman, encryption algorithm.
Randomness
Randomness is just as important as length to the strength of a private key. NIST has put out entropy source recommendations.
Commercial software often relies on a pseudo-random number generator (PRNG) to generate private keys. However, PRNG output is not truly random, and a determined attacker can defeat it with sufficient resources.
A source of physical entropy, such as a physical dice roll or coin toss, is required to generate truly random numbers. For example, when users generate a public key pair using the Pretty Good Privacy (PGP) public key encryption program, they are prompted to generate entropy by randomly moving their mouse.
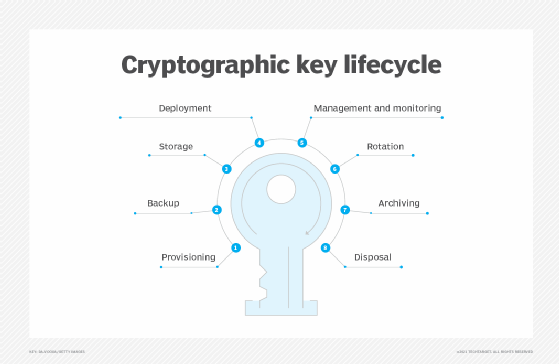
Encryption key management
Like any perishable commodity used in organizations, encryption keys require management. They must be created, administered and deleted when needed. Key management tasks include the following:
- provisioning or creating strong encryption keys for organizational needs;
- backing up keys that must be recoverable after system failures;
- storing keys securely;
- deploying keys to systems that need them;
- managing and monitoring use of deployed keys;
- rotating keys to prevent overexposing them to sensitive material;
- archiving keys that are no longer being actively used for data recovery; and
- disposing keys that are no longer required to prevent unauthorized use.
NIST recommendations for key management are a good place to start when implementing encryption key management platforms.
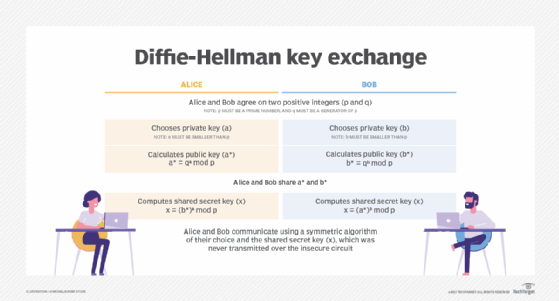
What algorithms are used for encryption key exchange?
Before the widespread deployment of computers connected over an open network -- the internet -- key exchange was a difficult part of encryption. Secure key exchange depended on a physical exchange of keys or keying materials.
As computers have become widely used for encryption, key exchange continues to be a challenging part of securing data exchanges over the internet. Data traversing the internet is exposed to a variety of intermediary systems, so it became necessary to implement encryption protocols for the secure exchange of private keys.
The Diffie-Hellman key exchange protocol was first published in 1976. It is a standard for generating a session key that encrypts communications sessions between computers on an open network. Network applications that use session keys for encrypted exchanges include the following:
- Hypertext Transfer Protocol over Secure Sockets Layer sessions. HTTPS sessions between web browsers and web servers are encrypted with session keys.
- Telnet remote login sessions. Telnet sessions connect to a remote server and are often encrypted with session keys.
- Secure Shell sessions. SSH sessions connect to a remote server and are always encrypted with session keys.
Diffie-Hellman is not the only secure key exchange protocol. Others include the following:
- Internet Key Exchange. The IKE protocol is part of the IP Security protocol for negotiating key exchange and authentication as part of an IPsec connection.
- RSA. This key exchange protocol is part of the RSA public key encryption cryptosystem. It enables the exchange of private keys for digital signatures and symmetric encryption keys for session encryption.
A trusted key exchange protocol is a prerequisite for using symmetric encryption algorithms, such as Advanced Encryption Standard. It is also necessary for asymmetric encryption algorithms, like RSA.
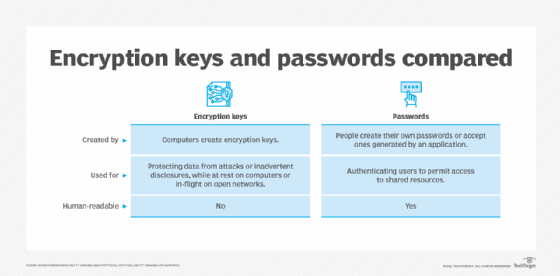
Encryption key vs. password
Passwords and secret or private encryption keys are similar in two important ways:
- Secrecy. Passwords and encryption keys should always be kept secret to prevent unauthorized use or access to protected data (keys) or systems (passwords).
- Entropy. The more random a password or a key is, the more likely that either will be able to resist hacking attacks.
Both passwords and keys restrict access to data (keys) or resources (passwords). Despite sharing these characteristics, encryption keys differ from passwords in the following ways:
- Computer systems use encryption keys to encrypt potentially sensitive data; passwords are used to authenticate system users and grant access to resources on a computer system.
- Encryption keys usually do not need to be human-readable; passwords usually do need to be human-readable.
What are some examples of encryption keys?
People routinely use encryption when they check their email or browse the web. However, most will never see the encryption keys that protect their communications.
One exception is those who use PGP to encrypt or digitally sign messages. Request for Comments 4880 is the specification that defines the OpenPGP implementation of PGP. According to that spec, PGP keys can be encoded as printable American Standard Code for Information Interchange characters using the Radix-64 encoding, which is also called ASCII armor.
An example of an ASCII armor-formatted PGP public key looks like this:
-----BEGIN PGP PUBLIC KEY BLOCK-----
A5O9u10AAP9XBeW6lzGOLx7zHH9AsUDUTb2OggYGMzd0P3ulJ2AfvQ4RtCZBbGlj
pFgEXEcE6RYJKwYBBAHaRw8BAQdArjWw23AqyiFbFBKT4TzXcVBqPTB3gUmzlC/U
sAcCBhUKCQgLAgQWAgMBAh4BAheAFiEW64W7X6M6deFelE5j8jFVDE9H444FAl2l
4SBMb3ZlbGFjZSA8YWxpY2VAb3BlbnBncC5leGFtcGxlPoiQBBMWCAA4AhsDBQsJ
LzoACgkQ8jFVDE9H447pKwD6A5xwUqIDprBzrHfahrImaYEZzncqb25vkLV2arYf
dEGXVQEFAQEHQEL/BiGtq0k84Km1wqQw2DIikVYrQrMttN8d7BPfnr4iAwEIBwAA
78aA/R3AwtLQvjxwLDuzk4dUtUwvUYibL2sAHwj2kGaHnfICnF0EXEcE6RIKKwYB
b7O1u10AAP9XBeW6lzGOLx7zHH9ACBBYCAwECHgECF4AWIQTrhbtfozp1MBAh4ah
eAFiEE64W7X4/xFPG6U17rhTuq+07gmEvaFYKfxRB6sgAYiW6TMTpQEK6IeAQYFg
AIBYhBOuF hcGs1O0RkWNQWbUzQ8nUOeD9wNbjE3zR+Mu88DsEw22jKl52lkqMcx
hcGs1O0RkWNQWbUzQ8nUOeD9wNbjE3zR+yfRAQDbYqvtWQKN4AQLTxVJN5X5AWyb
up+jOnXhXpROY/IxVQxPR+OOBQJcRwTpAhsMAAoJEPIxVQxPR+OOWdABAMUdSzpM
Pjn+We1aTBhaGa86AQ==
=t8OM
-----END PGP PUBLIC KEY BLOCK-----
While PGP keys can be displayed as readable text, most encryption keys are random sequences of the number of bits in the preferred key length. When it is necessary to display a key, the bit values are usually translated into some character set or numerical format.
For example, a 16-byte key (128 bits) could be displayed as binary digits, like this:
10111100 00101101 10100011 00010100 10001001 01101111 01001110 10101001
01101111 10111101 00000011 01110001 11100100 11110001 10111101 00001001
The same key could be displayed in hexadecimal format, like this:
BC 2D A3 14 89 6F 4E A9
6F BD 03 71 E4 F1 BD 09
The bits composing the key can be converted to any character set, though, in all cases, the character set must be specified for the key transcription to be useful.
Encryption keys are just one component of cryptographic platforms. Learn how encryption is implemented in hardware through the use of hardware security modules.






