information assurance (IA)
What is information assurance (IA)?
Information assurance (IA) is the practice of protecting physical and digital information and the systems that support the information. An IA strategy employs a variety of security measures to ensure the availability, integrity, authentication, confidentiality and nonrepudiation of an organization's information assets.
Information assurance seeks to reduce the risks to information and systems by taking the steps necessary to ensure their reliability and ongoing protection. Such safeguards have become especially important in today's digital landscape, where data now drives most of our daily business operations. The proper data protection procedures and use of this data can play a critical role in an organization's reputation and bottom line.
Organizations that prioritize IA stand a much better chance of ensuring the accuracy of their data and protecting the personal information entrusted to them. They can also better comply with applicable regulations and reduce the financial risks that come with compromised data. A single data breach can cost an organization millions of dollars in lawsuits, fines, tarnished reputations and diminished revenues.
According to the National Institute of Standards and Technology (NIST), information assurance is defined as the "measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality and nonrepudiation."
NIST also stated that IA can be described as the "degree of confidence one has that security measures protect and defend information and systems." To this end, the steps that an organization takes to implement IA should provide for the "restoration of systems by incorporating protection, detection and reaction capabilities."
5 principles of information assurance
Security teams that implement Information assurance programs typically adhere to -- or attempt to adhere to -- the following five principles to ensure the protection and reliability of their sensitive information and systems:
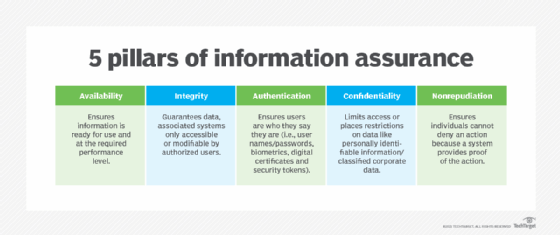
- Availability. Authorized users who need access to protected information should be granted that access without impeding their productivity. That said, they should be granted access only at the level required, applying the principle of least privilege to all information and systems. For example, one group of users might be allowed to read certain information but not be able to modify it, while other users are permitted to both read and update the information. At the same time, users with no authorization should be prevented from accessing any forms of that information.
- Integrity. Sensitive information is protected from unsanctioned modifications or deletions. Only users who have been authorized to make changes should be able to carry them out. If data is considered immutable -- that is, it should never be deleted or changed -- all modifications should be prevented. The goal is to ensure that the data remains reliable, accurate and trustworthy throughout its life span.
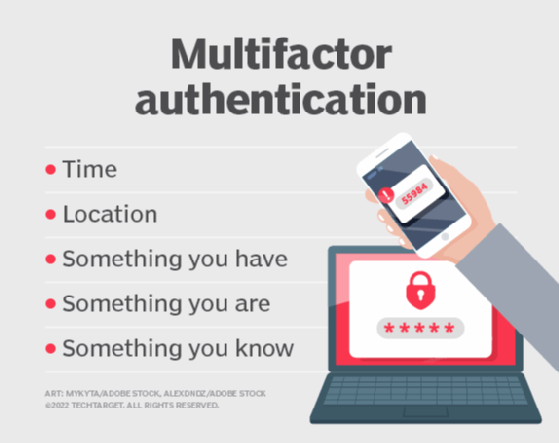
- Authentication. The identities of all users, devices and applications that attempt to access protected information should be validated to ensure that they are who or what they appear to be. Authentication often involves the use of protection strategies, such as strong passwords, multifactor authentication, biometrics, digital certificates or security tokens.
![what is multifactor authentication]()
The five factors used to authenticate a user requesting access to a system. - Confidentiality. All personally identifiable information and other sensitive information are protected at all times from unauthorized access. This type of confidential data should never be disclosed without proper approval -- unless required by law. Personal data is often protected by regulations such as the General Data Protection Regulation or California Consumer Privacy Act.
- Nonrepudiation. Those who have access to protected information or have handled it in any way should not be able to deny any of their actions, as they relate to that information. For example, they should not be able to refute that they transferred, modified or deleted data if they performed any of those actions. The systems used to manage, store and transfer information should have mechanisms in place that can prove what actions have occurred and who took those actions. In this way, the information's source and authenticity cannot be disputed.
The pillars are interrelated with one another and often reinforce each other. For example, authentication and confidentiality go hand in hand in ensuring the protection of private data. By adhering to these five principles, information security teams can better guarantee that their data is accurate, trustworthy and protected.
Organizations take different approaches in applying these five principles to their information and systems. Often, they carry out steps such as identifying and classifying their information assets or performing risks assessments that identify potential vulnerabilities to those assets. They might also attempt to identify gaps in their existing security structures. In addition, they likely develop policies and procedures as part of a larger risk management plan, as well as define strategies for implementing, monitoring and enforcing their IA initiatives.
Explore electronic signature best practices to build in to your workflow and how to use data classification to protect data and backup compliance. Discover how to execute cybersecurity best practices by reading this guide. Also, learn the essentials of data security and the practice of preserving the confidentiality, integrity and availability of organizational data.