honeynet
What is a honeynet?
A honeynet is a network set up with intentional vulnerabilities hosted on a decoy server to attract hackers. The primary purpose is to test network security by inviting attacks. This approach helps security experts study an actual attacker's activities and methods to improve network security.
What is the difference between a honeypot and honeynet?
A honeynet contains one or more honeypots, which are computer systems on the internet. They are expressly set up to attract and trap interlopers who attempt to penetrate other people's computer systems. Although the primary purpose of a honeynet is to gather information about attackers' methods and motives, the decoy network can benefit its operator in other ways, such as diverting attackers from the real network and its resources.
In addition to the honeypots, a honeynet usually hosts real applications and services to make it look like an actual production network and a worthwhile target. However, because the honeynet does not actually serve any authorized users, any attempt to contact the network is considered an illicit attempt to breach its security. As such, any outbound activity is likely evidence that a system has been compromised.
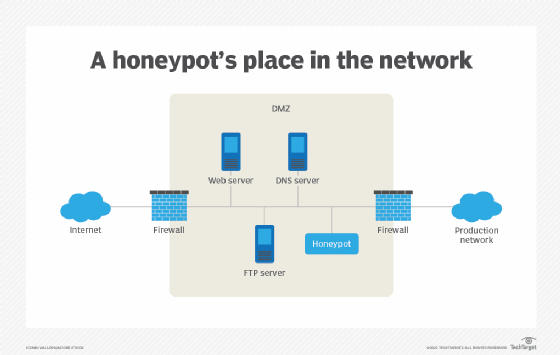
For this reason, the suspect information is much more apparent than it would be in an actual network, where it would have to be tracked down amid all the legitimate network traffic and data. Applications within a honeynet typically have familiar names like finance or human resources to make them appealing to an attacker.
A virtual honeynet is one that, while appearing to be a physical network, is a virtual image of a network that resides on a single server. As it is not a network system, computer security analysts do not have to waste their time examining legitimate users found in real-world networks.
As a honeynet cannot detect attacks on legitimate systems, there is always the risk of an attacker moving laterally from the honeynet to a production network segment to penetrate the real network. To mitigate risk, it is best to isolate the honeynet network and monitor it proactively.
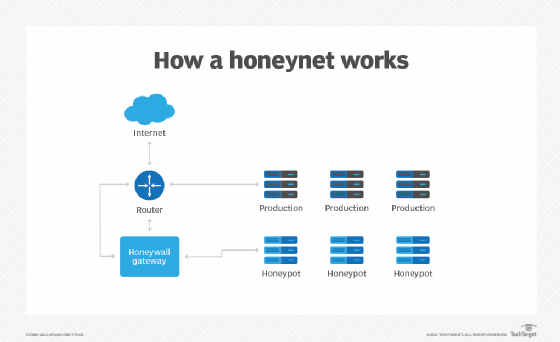
What is a honeywall?
A honeywall is used to monitor network traffic and divert malicious actors to honeypot instances. In a honeywall scenario, security experts often inject more vulnerabilities into a honeynet to make it easier for attackers to access the trap.
As any point in the network can be a point of entry, monitoring traffic in real time and diverting attackers away from the actual network are important.
What is The Honeynet Project?
The Honeynet Project is a nonprofit international research organization dedicated to computer security and information sharing. As such, The Honeynet Project actively promotes the Deployment of honeynets.
The organization is also committed to developing Open Source security tools, studying the latest hacking methods and investigating the latest cyber attacks.
What are honeypots and honeynets in Windows networks?
There are one or more honeypots in a honeynet. These honeypots can appear like a real network with multiple systems hosted on one or more servers. Each server represents a different environment.
As such, a honeynet can have a Microsoft Windows Server or honeypot machine to represent a Windows environment, a Linux honeypot machine for a Linux-based environment and so on.
Check out the ultimate guide to cybersecurity planning for businesses. Also, explore the top cybersecurity best practices to protect your business and the different types of cybersecurity controls and how to place them.








