footprinting
What is footprinting and how does it work?
Footprinting is an ethical hacking technique used to gather as much data as possible about a specific targeted computer system, an infrastructure and networks to identify opportunities to penetrate them. It is one of the best methods of finding vulnerabilities.
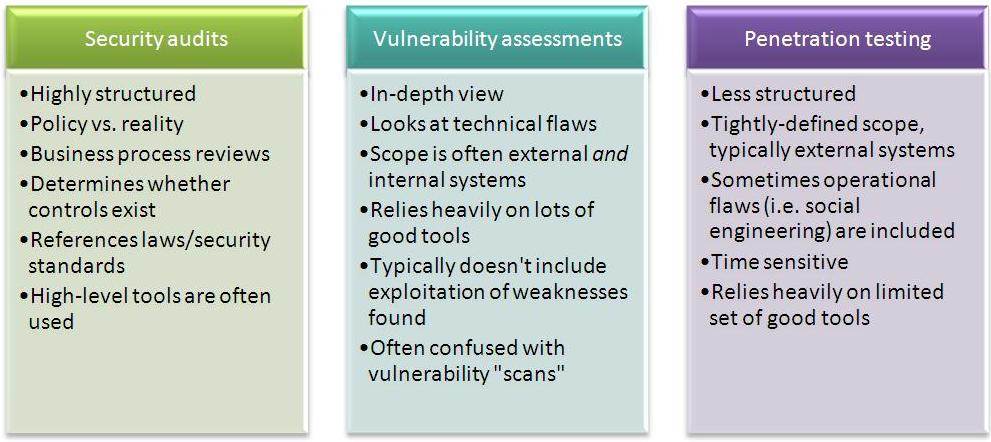
The process of cybersecurity footprinting involves profiling organizations and collecting data about the network, host, employees and third-party partners. This information includes the OS used by the organization, firewalls, network maps, IP addresses, domain name system information, security configurations of the target machine, URLs, virtual private networks, staff IDs, email addresses and phone numbers.
There are two types of footprinting in ethical hacking:
- active footprinting
- passive footprinting
What is active footprinting?
Active footprinting describes the process of using tools and techniques, like using the traceroute commands or a ping sweep -- Internet Control Message Protocol sweep -- to collect data about a specific target. This often triggers the target's intrusion detection system (IDS). It takes a certain level of stealth and creativity to evade detection successfully.
What is passive footprinting?
As the name implies, passive footprinting involves collecting data about a specific target using innocuous methods, like performing a Google search, looking through Archive.org, using NeoTrace, browsing through employees' social media profiles, looking at job sites and using Whois, a website that provides the domain names and associated networks fora specific organization. It is a stealthier approach to footprinting because it does not trigger the target's IDS.
How do you start footprinting?
Reconnaissance is similar to footprinting and is a crucial part of the initial hacking exercise. It is a passive footprinting exercise where one collects data about the target's potential vulnerabilities and flaws to exploit while penetration testing.
 Footprinting can help ethical hackers find potential vulnerabilities to assess and test.
Footprinting can help ethical hackers find potential vulnerabilities to assess and test.
Footprinting processes start with determining the location and objective of an intrusion. Once ethical hackers identify a specific target, they gather information about the organization using nonintrusive methods, such as accessing the organization's own webpage, personnel directory or employee bios.
Ethical hackers collect this information and initiate social engineering campaigns to identify security vulnerabilities and achieve ethical hacking goals.
Advantages of footprinting
Footprinting techniques in ethical hacking help businesses identify and secure IT infrastructure before a threat actor exploits a vulnerability. Users can also build a database of known vulnerabilities and loopholes.
Footprinting also helps companies better understand their current security posture through analysis of data gathered about the firewall, security configuration and more. Users can update this list periodically and use it as a reference point during security audits.
Drawing a network map helps cover all trusted routers, servers and other network topologies. Users can pursue a reduced attack surface by narrowing it down to a specific range of systems.
Other types of footprinting
DNA footprinting is the method used to identify the nucleic acid sequence that binds with proteins.
An ecological footprint is an approach to measuring human demand for natural capital or resources. It calculates the amount of natural resources required to support people or an economy. Ecological footprinting uses an ecological accounting system to keep track of this demand.
A digital footprint describes one's unique, traceable digital activities. These include actions, communications and contributions expressed on the internet or digital services. Digital footprints can be either active or passive.
Explore the future of cybersecurity, and check out an ultimate guide to cybersecurity planning for businesses.








