What is exposure management?
Exposure management is a cybersecurity approach to protecting exploitable IT assets. It involves identifying, monitoring, preventing and remediating risks and vulnerabilities on exposed assets, such as endpoints, servers, applications and cloud-based resources.
The goal of exposure management -- sometimes referred to as cyberthreat exposure management, threat exposure management or continuous threat exposure management -- is to examine the attack surface of an organization to detect and address vulnerabilities and security blind spots before malicious actors find them. This helps organizations protect their attack surface; keep IT assets secure; and prevent cyberthreats, such as data breaches. It is also a key component of the risk assessment process, helping organizations assess levels of risk and their potential impacts on the business.
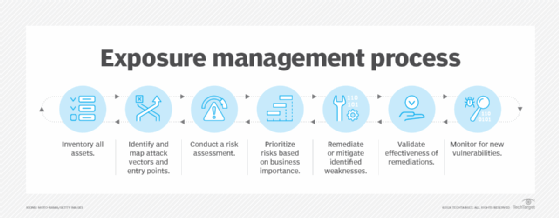
How organizations conduct exposure management is unique to their business model and stakeholders. The process generally includes the following steps:
- Inventory all assets.
- Identify and map attack vectors, attack paths and potential entry points.
- Conduct a risk assessment.
- Prioritize risks based on business importance.
- Remediate or mitigate identified weaknesses.
- Validate effectiveness of remediations.
- Monitor for new vulnerabilities.
Exposure management isn't a one-and-done task. It is an ongoing, continuous process to keep IT assets protected.
Gartner outlined five steps for its continuous threat exposure management process: scoping, discovery, prioritization, validation and mobilization.
Exposure management vs. vulnerability management
While vulnerability management and exposure management sound similar and have the same end goal of protecting assets, they are not synonymous. Vulnerability management is a process used for exposure management.
Exposure management focuses on discovering, monitoring and mitigating attack surface risks to determine a risk posture based on exploitable digital assets. It is a holistic approach to protecting an organization's assets from vulnerabilities and weaknesses created through exposed access points.
Vulnerability management focuses on finding, remediating and mitigating security vulnerabilities by inventorying systems and applications, scanning networks and prioritizing weaknesses. It is often based on the Common Vulnerability Scoring System.
Exposure management benefits
Exposure management helps organizations understand their risk posture and address cyberthreats. It provides visibility into an organization's assets and attack surfaces and helps the organization reduce risk and prevent costly cyberattacks and loss of sensitive data.
Exposure management also provides the following benefits:
- Better security posture. Organizations can proactively prepare for and respond to common and newly discovered risks and vulnerabilities rather than reactively responding post-breach or post-attack.
- Understanding of the scope of risk and security. Exposure management helps security teams focus on and monitor specific threats and attack surfaces.
- Proper budget allocation. Security teams can address limited budgets while keeping high-risk assets protected by using exposure management to understand where to best apply investments.
- Ensure regulatory compliance. Knowing where IT assets live and what their security measures are helps organizations keep accurate reporting and meet regulatory requirements.
- Improved communication between decision-makers and security teams. Exposure management ensured security teams and C-suite executives are on the same page concerning asset risk prioritization and protection.
Exposure management challenges
Organizations might contend with the following difficulties when implementing an exposure management program:
- Lack of staff and skills. Effective exposure management requires skilled employees. Inadequate staffing and skills could lead to coverage gaps and missed vulnerabilities.
- Budget limitations. Companies might not have the budget to thoroughly assess and mitigate identified risks, perform continuous monitoring or pay skilled security professionals.
- Third-party risks. Organizations face risks introduced by third parties, such as with the SolarWinds attacks. If an organization's third-party vendors, contractors or partners have security vulnerabilities, it might be exposed to the same security risks via supply chain attacks.
Exposure management technologies and tools
Exposure management consists of several technologies and tools to effectively discover exposed assets and assess risks and attack surfaces.
Exposure management technologies
Organizations need several technologies to achieve a complete view of their security risk profile. These technologies help organizations understand their risks; determine levels of risk; and continually monitor for threats, vulnerabilities and attacks:
- Risk assessment. Risk assessments determine whether current security processes and infrastructure adequately protect IT assets by identifying weaknesses, asset exposure and levels of risk.
- Vulnerability management. The vulnerability management process helps organizations identify vulnerabilities and weaknesses in infrastructure, endpoints, networks, applications, servers and cloud services, then remediate those issues. This is best done continuously and by automation.
- IT asset management. ITAM enables tracking assets across their entire lifecycle, documenting where IT assets live and managing licensing information.
- Attack surface management. ASM provides understanding of external and internal vulnerabilities and attack vectors. It identifies where attackers could bypass defenses and where to monitor assets in the future.
- Threat detection and response. TDR identifies, monitors, and remediates or prevents threats before they become security incidents.
Types of exposure management tools
No single exposure management tool exists, although some vendors bundle suites of products to create an exposure management portfolio. Organizations can also use tools they have already deployed. These can include the following:
- Vulnerability scanners. Use vulnerability scanners that examine applications, cloud assets, networks, hosts and databases to identify vulnerabilities and weaknesses within IT environments.
- Asset discovery. Determining the attack surface starts with documenting all IT assets. IT asset discovery tools do the following:
- Scan systems and identify all endpoints and applications connected to the network.
- Monitor for asset weaknesses and vulnerabilities.
- Create a complete and up-to-date asset inventory.
- Detect shadow IT.
- Generate compliance reporting.
- External attack surface management. EASM tools identify and remediate security gaps based on external-facing asset prioritization. Some tools offer automated discovery of potentially exposed assets and conduct asset inventories.
- Cyber asset attack surface management. CAASM tools provide comprehensive asset inventory and management, map external and internal attack surfaces, and help identify and assess asset security measures.
- Patch management. Patch management tools identify, monitor and automate patching to keep applications and services up to date.
They also help security teams update local and remote desktops, servers, and other systems and devices. - Security monitoring. Exposure management requires continuous monitoring. Security monitoring tools collect data, including network traffic user activity data, used by security teams to detect suspicious and malicious behavior.
- Penetration testing and breach and attack simulation. Pen testing tools and BAS tools test and validate security infrastructure, including networks and applications.
How to build an exposure management program
With the technologies and tools in place, organizations should create a cyber-risk management program that includes exposure management.
To start, inventory all IT assets for potential exposure and identify vulnerabilities and weaknesses within the current cybersecurity infrastructure. Next, perform a complete attack surface mapping. Document potential exposures and how attackers could gain access to or exfiltrate assets. Consult threat intelligence feeds to stay up to date on attackers and their tactics as well as which attack vectors malicious actors target.
Next, perform a risk assessment to determine risk levels for all assets. Involve CISOs to accurately decide which assets are the most critical to protect and monitor. Create a prioritization list of which exposures and vulnerabilities to remediate and in what order. The goal isn't to remediate all weaknesses within an organization, just those deemed high priority. Monitor and remediate other exposures and vulnerabilities as time or budget permits.
Finally, validate the effectiveness of remediations and monitor for new threats and vulnerabilities.
Exposure management isn't complete after mapping, testing and remediating all assets and attack surfaces per the prioritization list. It is a constant and ongoing process that organizations should conduct on a continuous basis. Stay apprised of new assets and adjust or update risk prioritizations when new vulnerabilities are discovered or business needs change.
Exposure management best practices
A well-defined exposure management process is key to achieving defense-in-depth security. While it takes a lot of time and planning initially, the process is critical to minimizing asset exposure and preventing data loss and breaches.
Consider the following exposure management best practices:
- Prioritize assets deemed critical during the risk assessment as the exposure management program matures.
- Use automation where possible, especially in organizations that lack the staff or budget to perform routine exposure management tasks.
- Develop vulnerability response plans to ensure quick action for any weakness or exploit discovered during monitoring.
- Conduct regular pen tests or BAS exercises to determine if current processes work as intended or need to be updated or adjusted.








