What is endpoint detection and response (EDR)?
Endpoint detection and response (EDR) is a system that gathers and analyzes security threat-related information from computer workstations and other endpoints. The goal of these systems is to find security breaches as they happen and facilitate a quick response to discovered or potential threats.
The term endpoint detection and response only describes the overall capabilities of a tool set. Therefore, the details and capabilities of an EDR system vary greatly depending on the implementation.
An EDR implementation can be one of the following:
- A specific purpose-built tool.
- A small portion of a larger security monitoring tool.
- A loose collection of tools used together to accomplish the task.
As attackers continuously update their methods and capabilities, traditional protection systems can fall short. EDR combines data and behavioral analysis, which makes them effective against emerging threats and active attacks, such as novel malware, emerging exploit chains, ransomware and advanced persistent threats.
The historical data that endpoint detection and response tools collect can provide peace of mind and remediation for actively exploited zero-day attacks, even when a mitigation isn't available. The IT security industry considers EDR a form of advanced threat protection.
This article is part of
What is threat detection and response (TDR)? Complete guide
Why is EDR important?
EDR works by detecting and responding to known and unknown cyberattacks. As cyberthreats become increasingly sophisticated, traditional defenses like antivirus software are no longer sufficient to protect organizations.
The array of attack surfaces in modern enterprises has increased with the use of internet of things devices and intricate network connections. EDR helps security teams identify threats across all endpoints, such as laptops, desktops and mobile devices, systems. Organizations monitor endpoint activity in real time, letting security analysts identify cyberthreats quickly. EDR often collects and analyzes telemetry, network connection and endpoint activity log data.
When EDR detects a threat, it initiates automated or manual responses, such as isolating affected endpoints or alerting security teams to take immediate action, depending on how the EDR service is set up. EDR often integrates various threat intelligence feeds to help with threat hunting, identifying suspicious activity and indicators of compromise. It protects against known and emerging cyberthreats by combining endpoint data with threat intelligence.
Key steps to deploy EDR
There are several steps to successfully deploying EDR. The most important include the following:
- Assess organizational needs. Organizations should start by understanding their cybersecurity needs, including the types of endpoints they need to protect their current security infrastructure and potential vulnerabilities.
- Choose the right EDR solution. Once needs are determined, they should select EDR software that aligns with the organization's specific requirements and current infrastructure. This means ensuring that an EDR security service can integrate with the existing security systems, including firewalls and security information and event management (SIEM) tools.
- Install EDR on all endpoints. EDR software should then be deployed on all endpoints vulnerable to attack, such as laptops, desktops and mobile devices.
- Customize response plans. The EDR software must be configured to trigger responses in case of cyberattacks. This can include isolating affected endpoints, sending alerts and engaging incident response plans.
- Monitor and update regularly. Organizations should continuously monitor their endpoint activity and ensure their EDR software is updated with the latest threat intelligence and patches.
Endpoint detection and response use and capabilities
EDR is primarily concerned with endpoints, which can be any computer system in a network, such as end-user workstations and servers. The systems protect most operating systems, including Windows, macOS, Linux and Berkeley Software Distribution, but they don't include network monitoring.
An EDR system gathers information from many sources, including endpoints, firewalls, network scans and internet logs. Security vendors also offer EDR as part of a SIEM package, enabling a security operations center to investigate and respond to threats.
EDR is an integral part of a complete information security posture. It isn't antivirus software, but it may have antivirus capabilities or use data from another antivirus product. Antivirus software is primarily responsible for protecting against known malicious software. A well-executed EDR program, on the other hand, finds new exploits as they are running and detects malicious activity during an active incident. EDR is able to detect fileless malware attacks and attackers using stolen credentials, which traditional antivirus software can't stop.
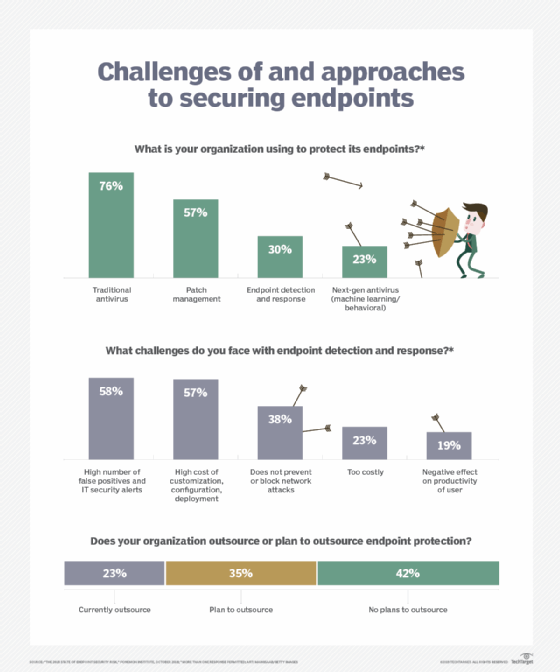
The role of an EDR system falls broadly into two categories:
- Information collection and analysis.
- Threat response.
Because EDR capabilities vary from vendor to vendor, an organization researching EDR systems should carefully investigate the capabilities of any proposed system. They should also consider how well it can integrate with their current endpoint security solution and other security capabilities.
EDR systems gather and organize data from endpoints, and then use that information to identify irregularities or trends. They use many data sources from an endpoint, including logs, performance monitoring information, file details, running processes and configuration data. A dedicated agent installed on the endpoint collects this data, or the system might use built-in operating system capabilities and other helper programs.
EDR systems organize and analyze the collected data. A client device might perform portions of this, but, generally, a central system -- hardware device, a virtual server or a cloud service -- performs these functions.
Simple EDR systems often only collect and display data or aggregate it and show trends. Operators might find following and making decisions based on this type of data difficult.
Advanced EDR systems use machine learning or artificial intelligence to automatically identify and send alerts about new and emerging threats. They might also use aggregate information from the product vendor to better flag endpoint threats. Some systems allow mapping of observed suspicious behavior to the MITRE ATT&CK framework to help detect patterns.
EDR threat response capabilities help the operator take corrective action, diagnose further issues and perform forensic analysis. This can enable issue tracking and help identify malicious activity or otherwise aid an investigation. Forensic capabilities help establish timelines, identify affected systems post breach and gather artifacts or investigate live system memory in suspect endpoints. Combining historical and current situational data helps to provide a fuller picture during an incident.
Some endpoint detection and response systems perform automated remediation activities, such as disconnecting or stopping compromised processes or alerting the user or information security group. They also can actively isolate or disable suspect endpoints or accounts. A good incident response system will also help coordinate teams during an active incident, helping to reduce its impact.
Key EDR features
EDR software has several key features. The most important include the following:
- Continuous real-time monitoring of endpoints and automated threat detection.
- Preconfigured incident response plans such as isolating endpoints or alerting security teams.
- Integration of real-time data and threat intelligence to identify known and emerging threats.
- Automated processes for detecting, analyzing and responding to potential attacks, reducing the workload on security teams.
- Comprehensive data collection across all endpoints to monitor activity and identify anomalies.
- Extended detection and response (XDR).
- Vulnerability identification and management.
- Attack surface reduction tools that minimize exposure of endpoints to potential cyberattacks.
- Suspicious activity alerts.
Endpoint detection and response tools
Vendors offer EDR capabilities either as standalone products or as part of an endpoint protection platform or a service package. According to Gartner, the highly rated XDR services include the following five:
- SentinelOne Singularity Platform.
- CrowdStrike Falcon.
- Harmony Endpoint
- Trend Micro XDR
- Microsoft Defender for Endpoint.
Several open source tools are available, but they might require extensive configuration or extra management systems to be fully featured. These tools include OSSEC, Wazuh, TheHive Cortex and Open EDR.
What to look for in EDR software
There are several important elements of EDR software that organizations should consider when selecting an EDR tool. The most important elements include the following:
- Real-time threat detection.
- Threat intelligence integration.
- Automated responses to security incidents.
- User-friendly interface for security analysts.
- Compatibility with existing security tools.
- Strong data collection and telemetry capabilities.
- Flexible deployment options on-premises or cloud-based.
- Scalability to accommodate organizational growth.
- High-quality customer support and managed services.
Protecting your endpoints is critical for maintaining security. Learn why EDR technologies are essential for endpoint protection.






