
What is double extortion ransomware? How to defend your organization
Double extortion ransomware is a type of cyberattack that encrypts a victim's data, like in a traditional ransomware attack, while also adding a second attack vector of stealing that data. This type of attack combines ransomware with elements of extortionware to maximize the attacker's chance of collecting a ransom payment.
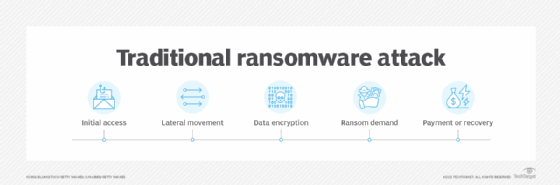
In a traditional ransomware attack, system data is locked and encrypted until the victim agrees to pay the attacker to get their data back. This has proven unsuccessful for many attackers, however, because victims can often restore their data and systems from backups.
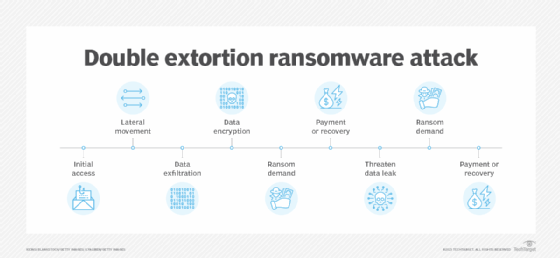
Double extortion ransomware has evolved to take traditional ransomware a step further. Ransomware operators not only encrypt data and hold it for ransom, but they also steal the victim's data and move it to a separate location.
Victims now face the added threat of having their private and sensitive data publicly leaked or sold on the dark web. This tactic gives attackers another way to extort victims into paying a ransom. Victims might be able to restore encrypted files through backups after a double extortion ransomware attack, but they still face the possibility that confidential information could be disclosed. Attackers could also use this opportunity to extort a second ransom, even if the victim pays the first request.
The first public reports of double extortion ransomware surfaced in 2019. It originated from a diverse set of criminal organizations, including the REvil ransomware gang and the Maze ransomware group TA2102. Since then, ransomware incidents have been on the rise.
How a double extortion ransomware attack works
Double extortion ransomware starts like a traditional ransomware attack, but includes the following additional steps:
- Initial access. An attacker or threat adversary group gains access to a victim's system. Common approaches include a phishing attack, where an email is crafted in a way to trick the user into clicking on an embedded link or downloading a malicious file; malware that is delivered using email, a malicious website or a watering hole attack; malware designed to exploit known vulnerabilities that the individual or organization has not patched; or a zero-day vulnerability. Lost or stolen credentials -- sometimes gathered from an existing data breach or using brute-force attacks -- could also be used to access victim systems.
- Lateral movement across a network. Once an attacker gains entry, the next step is to see what else can be accessed. The attacker moves laterally across a network to access as many high-value assets as possible. This step might also include privilege escalation.
- Data exfiltration. This step is added for double extortion attacks. After high-value assets have been identified, the attacker steals and moves or exfiltrates them to a remote site.
- Data encryption. Data is encrypted and locked; the victim can no longer access their files or information.
- Ransom demand. Once the data is encrypted, the attacker makes a ransom demand.
- Payment or recovery. The victim makes the ransom payment to unlock or recover their files and systems from backups or other methods.
- Double extortion ransom demand. If the victim can back up their systems and refuses to pay the ransom, the attacker threatens to publicly post their data or sell it on the dark web, thus demanding another ransom payment. Even if the victim pays the original ransom, the attacker could strike again for a bigger payout.
Examples of double extortion ransomware
Publicly reported incidents of double extortion ransomware include the following:
- Maze ransomware. The Maze ransomware attacks, attributed to a group referred to as TA2102, targeted a variety of organizations, among them IT services giant Cognizant in 2020.
- REvil. REvil ransomware was implicated in the successful attack against IT management vendor Kaseya in 2021.
- DarkSide. DarkSide ransomware was a primary element in the 2021 supply chain attack against Colonial Pipeline, which disrupted fuel supplies in the southeastern U.S.
- BlackMatter. The BlackMatter ransomware group, reportedly a successor to either DarkSide or REvil, successfully attacked agriculture technology firm New Cooperative in 2021.
- LockBit. LockBit, active since 2019, has increasingly added double extortion ransomware capabilities that some researchers suspect were taken from BlackMatter. According to a Cybersecurity and Infrastructure Security Agency advisory, LockBit ransomware as a service has been responsible for 1,700 ransomware attacks in the U.S since 2020.
Cybersecurity tools to defend against ransomware
Defending against traditional and double ransomware attacks requires a multilayered cybersecurity strategy. There are several cybersecurity tools an organization can use to help prevent these attacks. The following is a sampling of these security tools:
- Bitdefender.
- Broadcom Symantec Enterprise Cloud.
- Cisco Secure Endpoint.
- Dell Data Protection Suite.
- ESET Protect.
- F-Secure Total.
- Kaspersky Premium.
- Malwarebytes ThreatDown.
- Sophos Endpoint.
- Trend Micro Cloud One.
- Veeam Data Platform.
- Webroot OpenText Managed Detection and Response.
How to prevent double extortion ransomware
Double extortion ransomware can wreak havoc on a business, denying access to critical data and exposing sensitive information in a public forum. Individuals and organizations should take proactive steps to better prepare, defend against and recover from a double extortion ransomware attack. Ransomware prevention best practices include the following:
- Implement strong authentication and access policies. A successful double extortion ransomware attack depends on the attacker gaining system access. By locking down systems and user authentication using strong protocols and multifactor authentication, organizations can make it significantly more difficult for ransomware threat actors to access a system.
- Develop a network defense-in-depth strategy. A comprehensive defense-in-depth strategy flags intrusions before they become dangerous. Use a combination of firewalls, network traffic analysis tools, intrusion prevention and detection systems, web filtering and endpoint scanning.
- Tailor threat-hunting techniques. Threat-hunting tools actively look for potential threats that might have bypassed network fortifications.
- Conduct regular cybersecurity awareness training. Social engineering and phishing attacks are popular ways to launch double extortion ransomware attacks. Limit risk by training all employees and contractors who have access to the network.
- Use data loss protection tools. DLP technologies are specifically tailored to help organizations ensure sensitive and private information does not leave the network.
- Implement continuous backups. Ransomware is all about denying access to data. Maintain a properly configured continuous backup at a secure and remote location to improve the ability to recover quickly from a ransomware incident.
- Facilitate tabletop exercise planning. Schedule ransomware tabletop exercises to ensure the IT operations staff is ready to respond to an incident with recovery plans when and if a ransomware attack occurs.
- Keep software up to date. Ensure all operating systems, software and firmware are patched and current.
- Adopt a zero-trust policy. A zero-trust security model is a cybersecurity approach that denies access to an organization's resources by default and grants authenticated users and devices access to only the applications, data, services or systems they need.
Although cyber insurance cannot prevent double extortion ransomware, it might cover losses an organization incurs from a ransomware attack. The specific coverage of the cyber insurance depends on the policy.
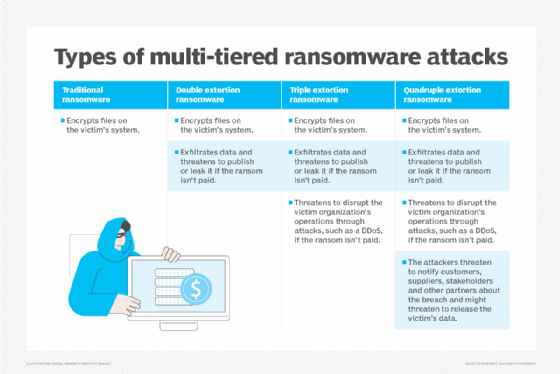
Multi-extortion cyberattack methods
Double extortion ransomware is only one type of multi-extortion attack method. Cybercriminals might also resort to triple or quadruple extortion ransomware attacks, where each type of ransomware adds an additional attack vector for malicious actors to exploit.
Ransomware is becoming a more common attack method for malicious actors. Learn about trends and statistics concerning ransomware.






