What is domain generation algorithm (DGA)?
A domain generation algorithm (DGA) is a program that generates a large list of domain names. DGAs provide malware with new domains to evade security countermeasures.
Cybercriminals and botnet operators use domain generation algorithms to deliver malware that can generate hundreds of new, random domains they can switch between during attacks. This approach makes it harder for the targeted victim to block and remove these domains.
Changing domain names helps hackers by preventing their servers from being blocklisted or taken down by their targeted victims. Security software typically blocks and takes down the malicious domains that malware uses, so switching domains quickly enables cybercriminals to continue pursuing the attack.
DGAs are one of the most known methods that make it harder for malware victims to protect against attacks. They have been used for over 10 years, and some malicious programs still pose a challenge for some to counter.
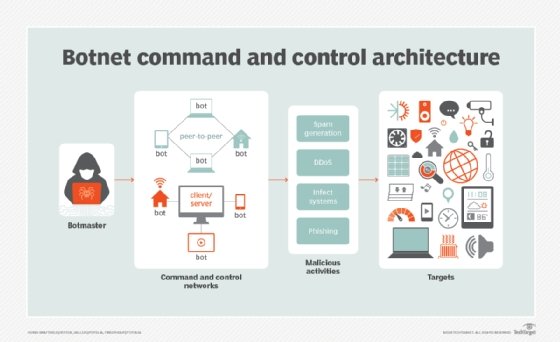
Some of the most familiar examples of malware attacks that used DGA to create control servers (C&C servers) include Conficker, Zeus and Dyre.
How does a domain generation algorithm work?
DGAs periodically generate numerous domain names. These domains act as a rendezvous point for malware commands and C&C servers.
DGAs are pseudo-random generators that construct a random sequence of characters used to form domain names. DGAs can also use words from a dictionary to construct domains. Dictionaries are either hardcoded in malware or taken from an accessible source. DGA generators are normally seed-based and can generate thousands of domain names.
The seed is known to both sides, so the same sequences are generated on both the client and source sides without needing to communicate. This enables the attacker to know beforehand which domain name the malware will use. The attacker then registers that one domain from the sequence to form a communication channel -- or rendezvous point -- for the malware.
If a domain is identified as malicious and is taken down, then the domain and C&;C server are quickly switched.
For example, if a website owner wants to use the domain name mysite.com and a search on a domain name registrar's site reveals that the desired domain name is not available, a DGA running in the site's background might return suggestions for 50 similar available site names.
How does malware use a domain generation algorithm?
Security software can quickly block malware that depends on a fixed domain or Internet Protocol (IP) address. So, in response, attackers use DGAs to switch the malware to a new domain at a regular time interval. This is opposed to using a new malware version or setting up a new server every time the domain is blocked.
The large number of potential rendezvous points makes it difficult for law enforcement to shut down the malware effectively. The additional use of public key cryptography in the malware's code makes it more challenging to mimic commands from malware controllers.
Botnets are a collection of internet-connected devices that malware infects and controls. Botnet operators have discovered they can use DGAs to hide the operator's C&C server and evade detection by blocklists, signature filters, reputation systems, intrusion prevention systems, security gateways and other security methods. The scheme, which is called domain fluxing, is similar to hiding a needle (the C&C server) in a haystack (a long list of IP addresses).
Best practices for detecting and protecting against DGA-fueled malware
A DGA does not harm the victim directly; rather, it enables a malware attack. The methods an organization can use to prevent normal malware attacks also work to prevent attacks that use DGAs. These best practices include using security software that prevents malware attacks, keeping software updated and not opening attachments from unknown sources.
Other methods that can directly counterattack DGAs include:
- Anti-DGA technologies. These use machine learning and big data to target irregular activity. The anti-DGA technologies use an automated prediction method that can anticipate, block and assist with taking down malicious sites.
- Deep learning techniques. Deep learning techniques can detect DGA domain names by using long short-term memory and convolutional neural network
- Multiple pop-up prevention strategies. The constant switching of domains -- domain fluxing -- can evade detection by ad blockers' blocklists, signature filters, reputation systems and other security controls. So in addition to configuring browsers to block pop-up ads, run antimalware regularly to remove existing malware and use permitter gateways to block outgoing calls by DGAs.
Types of domain generation algorithms
The most common types of DGAs include:
- Time-based DGAs use timestamps and dates as seeds to generate domain names. Time-based domains change periodically, making it difficult for cybersecurity tools to stay on top of them and preemptively block them.
- Character-based DGAs generate domains using specific character sets and patterns that create strings resembling randomly generated names.
- Wordlist-based DGAs use preset lists of words or phrases to create generated domains, making the domains appear legitimate.
- Seed-based DGAs use seed values to generate predictable and legitimate-sounding domain names.
- Hybrid DGAs combine multiple DGA types to increase unpredictability and make detection harder.
- Geolocation-based DGAs tailor domain names to specific regions using location data or regional top-level domains.
Examples of domain generation algorithms
Some of the most high-profile examples of DGAs or malware using DGAs currently used in cyberattacks include:
- Conficker DGA uses a time-based DGA to generate thousands of domains daily.
- Necurs botnet is known for using social media platforms for large-scale spam and phishing campaigns.
- Locky ransomware uses a character-based DGA to create domains associated with infected machines, hiding its command-and-control server locations.
- Dridex is known primarily for its financial malware attacks using a hybrid-based DGA.
- Emotet has infected Windows systems globally by using DGA-based malware.
Why do cybercriminals use domain generation algorithms?
DGAs avoid common detection means and control infected systems without relying on static domains that security services can easily block. DGAs generate thousands of domains in real time, making attempts to block them impractical.
Cybercriminals can therefore use DGAs to outpace domain name system (DNS) queries and firewall rules, allowing malware families to persist across network security infrastructures undetected. Also, domains that DGAs generate often use legitimate-appearing domains, which can further hide the malware's intentions from threat intelligence systems.
Learn how companies can arm themselves against six of the most common and damaging cyber attacks.







