What is defense in depth?
Defense in depth is a cybersecurity strategy that uses multiple security measures to protect an organization's networks, systems and data. The idea is that no single security product or process can fully protect a network, and that multiple layers of products and processes can provide redundancy if one layer should fail.
The phrases defense in depth and layered security are sometimes incorrectly used interchangeably. Layered security focuses on using multiple security measures to protect a single aspect of security, such as network security or endpoint security. It is a component of defense in depth.
An example of a defense-in-depth strategy is an organization using a firewall to inspect and filter traffic, intrusion detection and prevention systems (IDS/IPS) to monitor for and detect attacks, endpoint protection tools to secure devices, segmentation to limit lateral movement attacks, multifactor authentication (MFA) and single sign-on (SSO) for account access and data encryption to keep data secure even if it is exfiltrated, while also using a zero-trust model for continuous authorization and authentication.
Traditional perimeter security strategies are ineffective in today's enterprise networks mainly because of the prevalence of cloud use and remote employees. Employees and approved third parties need to access applications and data wherever they are in the world and on multiple different types of devices, which results in an expanded attack surface that traditional perimeter security tools cannot properly protect.
Defense in depth benefits
Defense in depth offers organizations numerous security benefits, including the following:
- No single point of failure. With multiple layers of protection, attackers can't gain full access to a network or IT system after bypassing a single layer of security.
- Cyber resilience. Defense in depth improves cyber resilience -- the ability of an organization to prevent, respond to and recover from cybersecurity incidents.
- Faster and improved threat detection. Additional security controls enable a higher probability of detecting and mitigating threats, including sophisticated attacks.
- Compliance and regulations. Adopting a defense-in-depth strategy helps organizations meet the requirements of many industry regulations, such as the Health Insurance Portability and Accountability Act, Payment Card Industry Data Security Standard and General Data Protection Regulation, which mandate certain security controls used for defense in depth.
- Makes attacks more expensive. Strategically placing multiple defensive controls and tools increases the effort and cost required for malicious hackers to conduct attacks. This could frustrate threat actors and lead them to abandon attacks.
Defense in depth challenges
Implementing a defense-in-depth strategy is not without complications. Consider the following challenges:
- Increased management complexity. Adopting multiple tools and security controls increases complexity and the chances an aspect of the attack surface could get overlooked. Adopting multiple tools can also result in tool sprawl, overlapping tools, wasted budget and extra work for the security teams managing them.
- Doesn't mitigate all attack types. While defense in depth helps prevent and mitigate many attacks, it isn't a silver bullet. Organizations remain susceptible to social engineering, supply chain attacks, zero-days and more.
- High costs and staffing requirements. A defense-in-depth security strategy requires multiple controls, which can increase costs, skills required and staffing needs. Without proper budgeting and resources, organizations risk having an incomplete defense-in-depth strategy that is vulnerable to exploits and attacks.
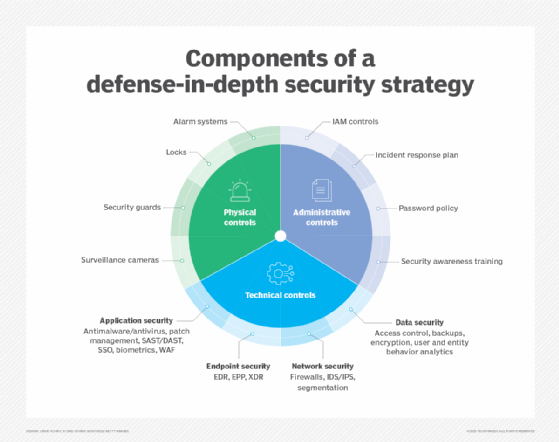
Elements of a defense-in-depth strategy
When designing a defense-in-depth strategy, organizations should cover the following three areas:
- Physical controls. Protect against threats, such as theft and tampering, to data centers, office buildings and other physical assets. Controls include alarm systems, door locks, security guards and surveillance cameras.
- Technical controls. Implement security tools and controls to protect data and systems from malicious actors. Consider using firewalls, threat detection and response, encryption and network segmentation.
- Administrative controls. Create and deploy security policies and procedures companywide. These include privileged access management (PAM), incident response plans, password policies and security awareness trainings.
Defense-in-depth layers and tools
While every organization will have its own strategy based on business needs, a successful defense-in-depth strategy generally includes the following layers and tools:
- Identity and access management. Implement a strong IAM program, including MFA, PAM, least privilege access, role-based access control, visibility and monitoring capabilities, and user and entity behavior analytics.
- Network security. Create a strong perimeter defense to keep data secure. Tools and technologies include firewalls, IDS/IPS and network segmentation.
- Application security. Secure in-house and third-party applications and application programming interfaces (APIs) using web application firewalls, static and dynamic application security testing tools, API security posture tools and patch management best practices. Follow authentication and authorization best practices, including using biometrics, SSO and more.
- Endpoint security. Protect all endpoints, including PCs, mobile devices and servers, with endpoint security technologies, such as endpoint detection and response, extended detection and response and endpoint protection platforms.
- Data security. Protect sensitive data with file integrity monitoring software to alert security teams if files, registry settings or folders are altered; secure data backups to improve recovery time after a data breach; and encryption to limit threat actors' ability to use exfiltrated data.
- Threat intelligence feeds. Follow threat intelligence feeds to stay up to date with emerging attack types.
- Monitoring and prevention. Add automation to continuously search for, detect and mitigate attacks. Consider using log monitoring software, SIEM systems, vulnerability management and incident response plans.
- Physical security. Use security guards, key card access and CCTV cameras to limit unauthorized access to offices, data centers and other physical locations.
How to implement defense in depth
Adopting a defense-in-depth strategy involves the following steps:
- Risk assessments and attack surface mapping. Conduct a risk assessment to prioritize which parts of the business require the most protection. Map out the organization's entire attack surface to understand its various attack vectors and which tools provide the necessary protections. Create a budget for defense in depth.
- Develop a strategy and deploy tools and controls. Evaluate, adopt and deploy security tools and controls. Test to ensure they work as expected to properly secure the attack surface.
- Conduct offensive tests. Use penetration testing and other red team exercises to confirm the current defense-in-depth strategy works and to understand where weaknesses or vulnerabilities exist. Address any issues.
- Monitor, review and update. Keep stakeholders informed of the strategy's progress and success at preventing or mitigating attacks, while continuously assessing it for improvement.








