continuous authentication
What is continuous authentication?
Continuous authentication is a method of verification aimed at providing identity confirmation and cybersecurity protection on an ongoing basis. By constantly measuring the probability that individual users are who they claim to be, continuous authentication validates the user not just once but nonstop throughout an entire session. Focused on furnishing smart, secure identity verification without interrupting the workflow, continuous authentication is implemented using machine learning and a variety of factors, including behavioral patterns and biometrics.
Continuous authentication is gaining attention as companies seek new ways to prevent unauthorized access to critical business data. Traditional forms of verification include single-factor authentication, which provides protection at login; two-factor authentication, which adds a second layer of security at login; and multifactor authentication, which adds further authentication methods. These traditional authentication measures do not offer continuous validation of a user's identification.
The need for new identity and access management strategies such as continuous authentication is growing as a result of the rapid pace of digital advancements and escalating cybercrime.
How does continuous authentication work?
Continuous authentication constantly collects information about a user's actions and patterns of regular behavior and learns to distinguish between normal and abnormal behavior. Based on analysis of user behavior, access to a system can be granted or additional user identity verification can be requested.
Variances and inconsistencies in behavior and user interaction with a system can be measured, or a user's physiological characteristics can be identified continuously during the session. If a user behaves badly or is compromised, access can be revoked, ending the application session immediately. Changes can be detected using keystrokes, video, fingerprints, touch (the amount of finger pressure applied) or facial features, such as eye position, pupil size or how often someone blinks.
An application with continuous authentication functionality can continually compute an authentication score to determine how certain it is that the account owner is the one using the device. Depending on the score, the user might be prompted to input additional information, such as a password, card or fingerprint.
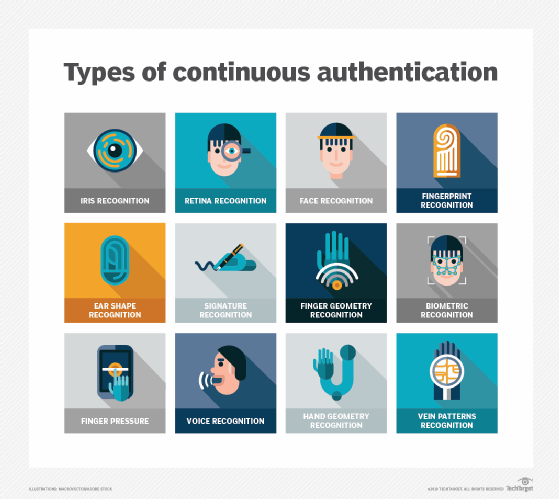
Types of authentication methods
A variety of technologies exist to support continuous authentication:
- Physical movement sensors. These can track a user's unique way of moving -- for example, how a user walks when holding a phone or specific hand positioning and movements when carrying or using a device.
- Facial identification. Facial recognition is often used for authentication purposes, such as accessing a mobile phone, but can also be applied to authenticate users continuously.
- Behavioral and physiological biometrics. User behavior patterns such as interactive gestures, how a user types or taps, finger pressure, how long a user holds a key on a keyboard, or how they swipe or use a mouse can be monitored continuously. Variances from the norm can then be highlighted or flagged.
- Voice authentication. Patterns in voice -- for example, changes in pitch and frequency -- can be tracked for continuous authentication. Out-of-the-ordinary qualities can be observed by constantly monitoring input speech against a control conversation used as a reference.
Benefits and drawbacks of continuous authentication
Using behavioral biometrics or the combination of behavior and physiology unique to each individual helps stop imposters, bots and fraudsters with criminal intent. The objective is to improve security without negatively affecting UX. Without continuous authentication, organizations are more vulnerable to many attack vectors and cybersecurity threats. For example, a system can be taken over when a user stops using it, but the session remains open. Other possible threats include credential stuffing and phishing.
Continuous authentication capabilities can be integrated directly into an application, but standards to accomplish this across multiple apps are not yet available. Although modern technology makes continuous authentication easier than in the past, user acceptance could remain an issue. Continuous authentication might be a step too far for some who see it as invasive and aren't comfortable being passively monitored. Similarly, privacy and compliance problems could arise. Balancing privacy concerns and security benefits is key to the acceptance of continuous authentication.







