content filtering
What is content filtering?
Content filtering is a process involving the use of software or hardware to screen and/or restrict access to objectionable email, webpages, executables and other suspicious items. Companies often use content-based filtering, also known as information filtering, as part of their internet firewalls. A common security measure, content filtering helps companies execute corporate policies on the use of information systems -- for example, the filtering and blocking of employee access to social media platforms.
Additionally, parents often use web filtering to screen and/or exclude content their children have access to from a home computer. Filtering software can screen content for anything that is objectionable or criminal, including online porn, hate sites, illegal content and social media. However, one drawback of content filtering programs is that it is easy to unintentionally block access to content that should not be blocked.
How does content filtering work?
Content filtering works by identifying content patterns like objects within images or text strings that indicate undesirable content that must be restricted or screened out. Enterprise networks incorporate content filters in various ways. Network administrators can configure firewalls, mail servers, routers and domain name system (DNS) servers to filter unwanted or malicious content.
Network administrators can install filtering software on dedicated servers or incorporate hardware appliances on the network. Cloud-based content filtering is also growing in importance as is mobile content filtering. Information filtering should be a factor for mobile and other devices, whether they are corporation- or employee-owned as well as for devices used at home, particularly by children.
Content filters usually specify character strings that, if matched, indicate undesirable content that should be screened out.
The following are types of content filtering products:
- Web filtering is the screening of websites or webpages.
- Email filtering is the screening of email for spam and other objectionable content.
- Executable filtering is the screening out of executable files that threat actors use to install unwanted or malicious software.
- DNS filtering is the blocking of content or network access from potentially harmful sources using a special kind of DNS resolver or recursive DNS server. The resolver has a blocklist or an allowlist to filter unwanted or harmful content.
These filters can be configured to exclude undesirable types of content or content that violates companies' acceptable use policies.
Content-based filtering products often include software programs or hardware devices that filter content. Subscription services also provide updated blocklists of potentially malicious IP addresses and domains.
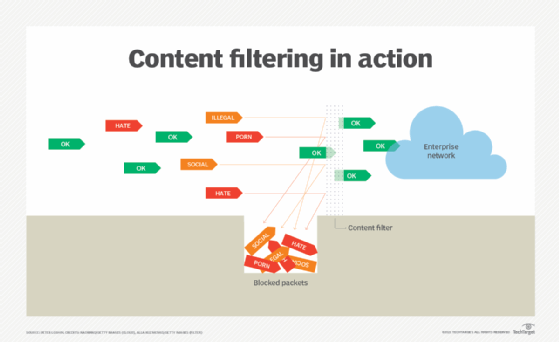
Benefits of content filtering
Content filtering is important because it protects individuals and organizations against potentially harmful content. Additionally, content filtering does the following:
- boosts network bandwidth;
- minimizes the risk of malware attacks;
- improves employee productivity;
- protects individuals, whether children or employees, from accessing content that is inappropriate for their age or function;
- reduces potential malware exposure by restricting access to malicious websites and email messages with malicious content;
- cuts down on potential legal liabilities as it prevents the spread of malicious content;
- improves network bandwidth use by restricting users from accessing unauthorized social media and streaming services, as well as limits attacks that can consume bandwidth; and
- protects organizations against attacks that use exploit kits hidden in other types of content and delivered in email or over the web.
Although content filtering is a key component of enterprise network security, it is not a complete network security strategy. Content filtering works best when combined with other security measures, such as firewalls, multifactor authentication (MFA) and effective authentication mechanisms, like Kerberos. Built into most major operating systems, Kerberos is a protocol for authenticating service requests between trusted hosts across untrusted networks like the internet.
Types of content filtering
Content filters work in tandem with allowlists or blocklists:
- Allowlists block all content except that which is explicitly permitted. This approach enables the strictest level of content filtering.
- Blocklists, or denylists, allow all content, except content that is explicitly forbidden. This approach is more permissive because it blocks only content that is specified.
Content filters use the following mechanisms to restrict inbound content:
- Scanning for restricted phrases or data types. Inbound content can be scanned and rejected for objectionable phrases or words.
- Excluding executable files. These files may be malware or other potentially unwanted programs. Filters can screen out different types of content, such as images, videos and audio files.
- Screening based on origin. Inbound content filtering products may include options for screening content from specific IP addresses, IP networks or domains known to host malicious, illegal or otherwise objectionable content.
- Filtering email content. This can include the option to reject outgoing messages that are being sent to restricted addresses or domains or messages that contain text flagging their contents as proprietary or confidential.
- Filtering texts. Companies can use mobile device management (MDM) tools to prevent employees from responding to messages from unknown sources or clicking on suspicious links, including those sent via Short Message Service (SMS). Businesses can also push out specific settings to all devices with corporate data and block messages from unknown sources.
Hardware vs. software vs. cloud-based content filtering
Ways to enable content filtering include the following:
- Configure existing systems, like various types of firewalls, email servers, routers and DNS servers, to screen out excluded content.
- Install dedicated content filtering software on existing or dedicated enterprise servers.
- Integrate hardware appliances for content filtering with enterprise network infrastructure.
- Use cloud-based content filtering systems that enable content filtering without requiring new hardware or software.
Content filtering in enterprises may use a single approach or may combine two or more of the mechanisms listed above.
Existing network security systems, such as firewalls, may already be configured to block content. Other software systems can enhance that function, as can dedicated appliances and cloud-based content filtering systems for different departments, locations and business units.
For network security, firewalls are considered a bare minimum to protect enterprises from attacks. Find out how inbound and outbound firewall rules can help keep unwanted content and intruders out of the network.
See also: IT security threat management tools, services to combat new risks, the 3 types of DNS servers and how they work, best practices for a modern threat management strategy, 9 essential elements of network security and stateful vs. stateless firewalls.






