What is cloud security?
Cloud security, or cloud computing security, is a set of policies, practices and controls deployed to protect cloud-based data, applications and infrastructure from cyberattacks and cyberthreats. It encompasses securing cloud-based resources, including data centers, servers, networks and virtual machines (VMs).
Cloud security addresses unique challenges such as shared responsibility models, multi-tenancy, data privacy and compliance requirements. The primary concern of cloud security is data privacy and protection during data transfer.
Cloud security is a broader discipline than cybersecurity but has the same goals. However, it differs from traditional cybersecurity because it requires administrators to secure assets within a third-party service provider's infrastructure.
Why cloud security is important
Companies outsource IT data, systems and applications to third-party cloud service providers (CSPs). When IT departments enter into contractual agreements with CSPs, it is understood that the CSP will be responsible for securing the underlying cloud infrastructure. Because no organization or CSP can eliminate all security threats and vulnerabilities, business leaders must balance the benefits of outsourcing cloud services against the data security risk their organizations are willing to assume.
Cloud security is vital for the following:
- Business continuity. Implementing effective cloud security mechanisms and policies is critical to preventing breaches and data loss, avoiding noncompliance and fines, and maintaining business continuity (BC).
- Centralized security. A significant benefit of the cloud is that it centralizes applications and data security. Eliminating the need for dedicated hardware reduces organizations' cost and management needs while increasing reliability, scalability and flexibility.
- Disaster recovery. Cloud security systems help prevent potential losses caused by natural disasters by providing data redundancy and backup services. Cloud environments typically include automated backup processes, where data is regularly backed up according to predefined schedules. These backups might consist of everything from individual files to entire server instances or databases, enabling organizations to easily back up and recover vital data if a disaster occurs.
- Resiliency. Many cloud providers have multiple data centers in different geographic locations. This enables more agile failover and promotes BC; if one data center experiences a security breach, applications and data can be failed over to an alternate site.
- Data protection. Businesses store confidential information on the cloud, such as customer financial details, intellectual property and sales records. If this information is leaked, it can cause irreparable damage. Therefore, stringent cloud security measures are essential for protecting sensitive data from unauthorized access and potential leaks. Most cloud security providers invest in advanced technologies, such as AI and security analytics, to automatically scan for suspicious activities.
- Enhanced business outcomes. Cloud security enables better business outcomes by managing and mitigating cloud security risks. Businesses transitioning to the cloud must prioritize cloud security to recover more quickly if anything goes wrong.
- Cost savings. Many businesses outsource cloud security to CSPs to save money on maintaining their security infrastructure.
- Cloud data compliance. Ensuring compliance is a key component of effective cloud data security systems, which entails understanding data storage, access, processing and protection requirements. Many organizations use cloud data loss prevention (DLP) techniques to reduce their chance of breaches and ensure data compliance.
- Data encryption. Most CSPs use advanced encryption techniques to provide comprehensive options for secure data transfer, storage and sharing. They can ensure data protection both during transit and at rest.
How cloud security works
Cloud computing operates in the following three main environments:
- Public cloud services. Third-party CSPs own and host public clouds. These include software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS). Public cloud services, including cloud security services, are available to anyone who wants to use or purchase them. Typically, cloud security in the public cloud focuses on protecting data from distributed denial-of-service attacks (DDoS), malware, hackers and unauthorized access.
- Private clouds. Private clouds are hosted by or for a single organization and are not shared with others. Cloud security in private clouds enables organizations to have more control over their data and resources while taking advantage of the cloud's scalability and other benefits.
- Hybrid clouds. These include a mix of public clouds, private clouds and on-premises data centers. Cloud security in hybrid clouds involves securing data and apps running in the cloud, other cloud environments and on-premises. It also requires uniform security options, policies and practices for protection across various cloud providers.
As a result, cloud security mechanisms take two forms: those supplied by CSPs and those enforced by customers. Security is rarely the complete responsibility of the CSP or the customer. It is usually a joint effort using a shared responsibility model.
Types of cloud security
Cloud security encompasses various measures taken to protect data, infrastructure, applications and the integrity of cloud environments.
Security as a service is a subset of SaaS. The Cloud Security Alliance defines the following security-as-a-service categories:
- Identity access management (IAM).
- DLP.
- Web security.
- Email security.
- Security assessments.
- Intrusion management.
- Security information and event management (SIEM).
- Encryption.
- BC and disaster recovery.
- Network security.
- Continuous monitoring.
- Penetration testing.
- Vulnerability scanning.
These include firewall as a service, cloud-based virtual private networks and key management as a service. Secure access service edge and zero-trust network access are also becoming popular cloud security models.
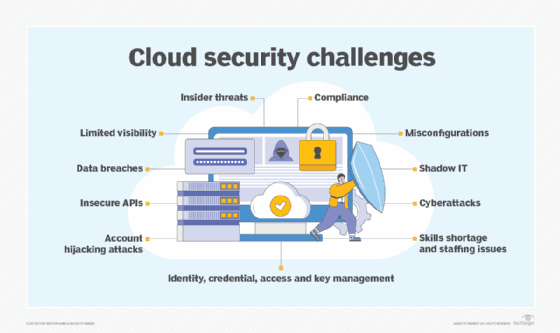
Top cloud security challenges
The following cybersecurity challenges exist in the cloud:
- Insider threats. These risks originate within an organization where authorized users move between on-premises and cloud-based assets and intentionally or unintentionally use this access to harm the company's systems or data.
- Data breaches. Unauthorized users accessing sensitive company data can affect the organization's reputation and financial standing, potentially leading to legal actions.
- Access control. To meet a universal security governance standard, security policies, authentication, authorization and permissions must be consistent across all clouds.
- Shadow IT. Users often subscribe to their own cloud services, creating blind spots for IT administrators and potentially increasing the risk of data breaches.
- Cyberattacks. Cyberattacks such as DDoS attacks use multiple trojan-infected systems to target a particular system and deny service.
- Insecure application programming interfaces. If APIs are misconfigured or user credentials are not properly implemented, API interfaces might not be adequately secured, making them vulnerable to malicious activity.
- Cloud visibility and control. Many IT organizations use IAM technology to ensure security visibility across all IT resources and access to only authorized users.
- Misconfigurations. Cloud security misconfigurations, such as forgetting to replace default administrative passwords or not setting privacy levels, are common, especially when IT must learn a different tool set for every cloud it uses.
- Cloud compliance. Companies using cloud services must comply with industry security and regulatory requirements to protect data and avoid legal ramifications.
Security administrators must implement processes to identify and mitigate emerging cloud security threats. These threats typically revolve around newly discovered exploits found in applications, OSes, VM environments and other network infrastructure components. Organizations must quickly and properly update and patch the software they control to handle these security challenges and eliminate emerging threats.
Establishing communication channels between in-house IT and CSP staff is also essential. In-house staff should subscribe to, monitor and digest the CSP's security bulletin stream. Well-documented communication channels must be established and continuously updated so time isn't wasted when working through a security breach.
Cloud security tools
Many of the same tools used in on-premises environments can be used in the cloud, although cloud-specific versions of them might exist. These tools and mechanisms include encryption, IAM and single sign-on, DLP, intrusion prevention systems and intrusion detection systems, and public key infrastructure.
Some cloud-specific tools include the following:
- Cloud workload protection platforms. This security mechanism is designed to consistently protect workloads, such as VMs, applications or data.
- Cloud access security brokers. A CASB is a tool or service that sits between cloud customers and cloud services to enforce security policies and, as a gatekeeper, adds a layer of security.
- Cloud security posture management. This group of security products and services monitors cloud security and compliance issues and aims to combat cloud misconfigurations.
- Cloud Intelligence and threat hunting. These tools provide threat and anomaly detection in the cloud using analysis of account activity logs and posture findings.
- Serverless security. These tools apply vulnerability assessment and posture management for serverless functions in the cloud.
- Tools to manage identities and access rights. Whereas IAM tools can provide security visibility across all IT resources, a complementary technology, cloud infrastructure entitlement management (CIEM), can help provide granular control across cloud environments.
Cloud security best practices
There are separate security SaaS best practices, PaaS best practices and IaaS best practices. Organizations should also adhere to several general cloud security best practices, including the following:
- Understand the shared responsibility model. Organizations should understand the responsibilities of their CSPs and security teams, focusing on how they connect to the cloud and control data and access.
- Choose CSPs wisely. Businesses should know what security controls the cloud vendors offer and diligently review contracts and service-level agreements.
- Adopt an IAM policy. Organizations should implement a granular IAM policy based on the principle of least privilege and strong passwords.
- Enforce encryption. Data should always be encrypted, whether at rest, in use or in motion.
- Conduct continuous monitoring. Companies should maintain cloud visibility through continuous monitoring. Regular monitoring helps them stay on top of security-related feature updates from cloud providers and establish incident response practices.
- Establish and enforce cloud security policies. A cloud security policy outlines the procedures and controls governing data security, applications and infrastructure in cloud environments. It helps ensure that security measures are consistently applied across the organization's cloud deployments and align with regulatory requirements and industry best practices.
- Provide security training. Companies should conduct security awareness training for employees, third-party partners and anyone accessing organizational cloud resources.
- Perform cloud segmenting. Cloud segmentation involves dividing cloud environments into unique segments or zones based on access requirements, data sensitivity and security controls. Segmenting cloud resources enables organizations to set up granular access controls, ensuring that users and apps only have access to the required resources.
- Consider using CIEM. CIEM software is specifically designed to monitor user activities in the cloud. It can provide granular visibility into cloud-based user activities.
- Implement strong access controls. Multifactor authentication and rigorous password policies should be enforced.
- Ensure safe APIs. All APIs should have strong authentication and encryption and be tested regularly for vulnerabilities.
- Consult the Cybersecurity Security Information Sheets. The Cybersecurity and Infrastructure Security Agency and the National Security Agency have released joint Cybersecurity Information Sheets to provide organizations with recommended best practices and mitigations to improve the security of their cloud environment.
Future of cloud security
Cloud security is rapidly evolving, with several emerging trends and technologies shaping its future. According to IBM's "Cost of Data Breach Report 2024," the highest average cost per incident of breached data stored in cloud-based systems reached $5.17 million in 2024. Given the notable surge in cloud-based attacks, it is imperative for companies embracing cloud technology to prioritize strong security measures.
The following are some emerging trends shaping the future of cloud security:
- Serverless computing. Serverless computing enables businesses to run applications and services without managing the underlying server infrastructure. It offers numerous benefits for cloud security by reducing the attack surface, including automating security updates and providing isolation and sandboxing. Serverless computing also enables scalable security controls, offering built-in security features and promoting security as code practices. As organizations increasingly adopt serverless architectures, they are likely to rely on these capabilities to enhance the security posture of their cloud-based applications and services.
- Integration of large language models. Cloud services are increasingly integrating large language models (LLMs). By automating threat detection and response through machine learning (ML) and natural language understanding, LLMs transform cloud security. Their ongoing adaptation to changing threats offers real-time information for prompt incident handling. LLMs also serve as proactive sentinels against social engineering threats, simplify compliance management by understanding regulatory texts and assist with incident response communication to lessen the damage security breaches do to a company's reputation.
- Adoption of zero trust. Zero trust concepts are expected to shape cloud environments significantly. With zero trust, access to resources, data and permissions are not automatically granted based on user identity or network location. Instead, every access request is rigorously authenticated, authorized and continuously monitored, regardless of whether it originates inside or outside the network perimeter. By adopting zero-trust policies, organizations can minimize the risk of lateral movement attacks and reduce the effects of potential breaches. In cloud network security, zero-trust models are expected to become increasingly prevalent as organizations adopt cloud-based architectures and distributed workforces.
- AI-based threat detection. Conventional security measures might not be adequate as cyber threats change over time. By examining large data sets to find anomalies and possible breaches, threat detection driven by AI is becoming the new norm. It is a notable development in cloud security due to its proactive protection against new threats, which enables enterprises to recognize and eliminate threats before they can negatively affect the cloud infrastructure.
- CIEM. This emerging security technology has great potential because it can give IT granular visibility of user activities in the cloud.
Many organizations lack the in-house cloud security expertise and resources to adequately protect cloud assets during their transition to hybrid and multi-cloud infrastructures. Learn the benefits of outsourcing cloud security and explore the pros and cons of managed cloud security services.







