What is cloud infrastructure entitlement management (CIEM)?
Cloud infrastructure entitlement management (CIEM) is a modern cloud security discipline for managing identities and privileges in cloud environments. As organizations shifted from on-premises computing and storage systems to cloud-based infrastructure accessed via the internet, IT and security teams established a set of practices and processes to determine which users can access cloud infrastructure and for what specific purposes.
At its core, CIEM helps organizations do the following:
- Govern identity access. CIEM lets organizations enable and track which users have permission to access what in the organization's cloud infrastructure, regardless of whether that cloud environment is with a single cloud provider or multi-cloud.
- Enforce least-privileges access. The objective of entitlement management is to understand and catalog the access entitlements that exist within the cloud environment. This lets an organization provide users with seamless and secure access to the cloud infrastructure they require to perform tasks. It simultaneously prevents users from accessing infrastructure that they aren't authorized to use. This is known as the principle of least privilege, or POLP.
- Integrate with other access management tools. CIEM is one component of an organization's identity access management (IAM) program, and it works in conjunction with cloud security posture management (CSPM) tools. CIEM also dovetails with the zero-trust security model, and, as such, fits within the organization's security program.
- Automate access governance. CIEM tools, which are typically delivered in the cloud as software as a service (SaaS), let IT and security teams manage user identities and enforce access entitlements. Multiple vendors sell software to support and automate an organization's entitlement management program.
- Improve visibility into permissions. CIEM software is usually integrated into a cloud-native application protection platform (CNAPP), enabling IT and security teams to have a more holistic view of their security practices.
Why is CIEM important for cloud security?
As enterprise IT infrastructure becomes more complex and more expansive, many organizations use a mix of on-premises and cloud-based computing software and data storage systems. Consider the state of cloud adoption, where 86% of organizations have embraced a multi-cloud strategy, according to the "2025 State of the Cloud Report" from Flexera, which makes IT management software.
Meanwhile, according to the "Cloud Security 2024: Managing Complexity" report from research firm IDC, 56% of organizations reported having a more complex multi-cloud environment than expected.
A typical organization has a growing number of cloud deployments from a lengthening list of cloud providers. Organizations might have workloads running in one or more of the hyperscalers, such as Amazon Web Services (AWS), Google and Microsoft, while likely using multiple SaaS products.
More use of cloud resources comes as the volume and velocity of cybersecurity threats surge. Consequences and costs associated with a data breach, whether because of a successful attack on an organization's systems or as the result of human error, have increased significantly. The global average cost of a data breach in 2024 was $4.9 million, a 10% increase over the previous year, according to the "Cost of a Data Breach Report 2024" from Ponemon Institute and IBM Security.
Each of those factors on its own speaks to the need for an organization to effectively manage users' access to its technology environment. And, when combined, those factors create an imperative for entitlement management to prevent unauthorized users from accessing sensitive data.
Of course, CIEM is only part of a larger security program, complementing the other components.
Challenges of entitlement management
CIEM addresses the entitlement-management challenges that come with dynamic cloud environments involving multiple providers. Common challenges that CIEM helps manage include the following:
- Entitlement complexity at scale. A typical organization has thousands -- sometimes even millions -- of individual permissions granted to users. Users can be people or on-premises and cloud-based systems, all of which are in near-constant flux. Individual roles in the organization change. Systems undergo upgrades, and tasks users must perform to get work done are refined or replaced. CIEM lets IT and security teams oversee entitlements even as elements change, making it a critical piece of an organization's security layer.
- Lack of visibility. Traditional IAM tools often fall short in cloud environments, where entitlements can be inherited, nested or dynamically assigned. CIEM provides granular, real-time visibility into effective permissions across cloud services.
- Excessive permissions. CIEM helps curb excessive permissions and privilege creep. It continuously discovers and maps all identities and their effective access, identifying unused or overlapping permissions and enforcing POLP through automated rightsizing or revocation.
- Complexity of multi-cloud environments. Organizations often use multiple cloud service providers, such as AWS, Google Cloud and Microsoft Azure. Each has its own unique IAM framework, terminology and permission structures. Managing entitlements consistently across these disparate environments manually is a massive and error-prone undertaking. CIEM centralizes entitlement management across diverse cloud platforms, normalizing data and providing a unified dashboard. This simplifies policy enforcement and ensures consistent security policies, reducing configuration inconsistencies and security gaps.
- Risky entitlement combinations. Sometimes, individual permissions might seem harmless, but when combined, they create a dangerous attack path. For example, the ability to read sensitive data and modify logging configurations enables an attacker to exfiltrate data and then cover their tracks. Detecting these complex interdependencies manually is nearly impossible. By using advanced analytics, machine learning (ML) and user and entity behavior analytics (UEBA), CIEM can identify these toxic combinations and alert security teams to potential privilege escalation or lateral movement risks.
- Compliance and audit readiness. Meeting regulatory compliance requirements for access control in the cloud can be complex, often requiring detailed proof of who has access to what. By providing continuous monitoring, automated reporting and historical audit trails of entitlement changes and use, CIEM significantly simplifies the process of demonstrating compliance and preparing for audits.
Components of CIEM
A CIEM tool complements other security software, layering in capabilities that are included or as extensive as required in other tools, such as CSPM, cloud workload protection platforms (CWPPs) and cloud access security brokers.
The components commonly found in CIEM products include the following:
- Discovery. CIEM products have the ability to identify all cloud resources and users -- both humans and machines -- along with their associated permissions and account activities. In other words, a CIEM tool can identify which user has entitlements to which cloud resource.
- Analysis. A CIEM tool should give IT and security teams the ability to analyze entitlements, policies, rules and risks, letting them identify excessive permissions and optimize entitlement policies.
- IAM. CIEM products offer centralized IAM across cloud resources.
- Governance and enforcement. CIEM products also automate policy and rules enforcement, helping organizations follow POLP.
- Anomaly detection. These products include UEBA, as well as other analytics and ML capabilities to detect abnormal behaviors that could indicate unauthorized access attempts.
- Management capabilities. A common feature of a CIEM product is a dashboard that delivers a centralized view into user permissions throughout the organization's cloud environment, as well as data on anomaly detection, governance and compliance.
- Visibility and access control. CIEM systems increase visibility into cloud access entitlements and give IT and security teams more control over users' permissions. This helps organizations strengthen their security posture and reduce risks. It can also help increase agility and speed transformation, as companies have increased confidence that they can manage permissions while they adopt new applications as fast as the business needs them.
- Audit and compliance reporting. CIEM provides detailed logs, dashboards and reports on access activity, entitlement changes and policy enforcement to support regulatory and internal governance needs.
How CIEM is used
CIEM products rely on advanced analytics and ML to identify user entitlements, analyze them against an organization's rules and compliance requirements, and then align them against the organization's own policies. That enables a CIEM product to not only identify entitlements but also assess each user's entitlements to determine whether that user has the appropriate level of access privileges. If they don't, the CIEM tool alerts administrators to users with excess privileges so they can act. If an automated response is enabled, the tool automatically adjusts a user's level of access.
CIEM tools can perform this analysis across multiple cloud platforms and as cloud resources change -- for example, when an organization scales up and down or provisions and deprovisions based on needs. Taken together, CIEM platforms let administrators monitor, manage and adjust permissions, even in large-scale cloud environments.
What are the benefits of CIEM?
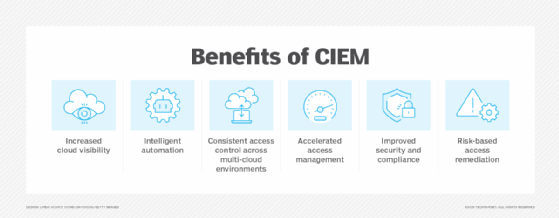
Developing an effective CIEM program and investing in a CIEM product have benefits, such as the following:
- Increased visibility. Better visibility into the organization's cloud entitlements lets IT and security leaders know that they're giving the right level of permissions to users. This means users can accomplish business tasks without receiving excessive permissions that might increase risks and without being denied the access they need, which negatively affects productivity. CIEM tools typically have an audit function, too, which further boosts visibility and accountability.
- More efficiency. With automation, ML and analytics let administrators work at a scale and speed exponentially greater than manual processes.
- Higher levels of consistency. A CIEM tool's automation and intelligence capabilities enable consistent enforcement of access control policies across cloud environments of all sizes. By normalizing permissions across multiple cloud providers, CIEM helps organizations maintain unified security policies in hybrid and multi-cloud environments.
- Greater agility and accelerated access management. CIEM products are designed to deliver their capabilities and benefits in dynamic cloud environments so IT, security and business teams can deploy, provision and deprovision as fast as needed without being slowed by manual access control management processes. Automated IAM and anomaly detection and response further boost agility.
- Improved security posture and privacy requirement compliance. A CIEM program supported by a CIEM tool ensures that entitlements are rightsized, aligned with the organization's rules and policies, and appropriate. This lowers overall risks.
- Risk-based access decisions. Advanced CIEM platforms incorporate analytics and risk scoring to prioritize remediation efforts based on business impact, helping security teams focus on the most critical access risks.
Best practices for implementing CIEM
Effectively implementing CIEM requires a strategic, ongoing approach to managing identities and permissions across complex and dynamic cloud environments. The following best practices can guide organizations looking to implement CIEM successfully:
- Start with a cloud identity inventory. Before deploying a CIEM tool, organizations should perform a thorough audit of all existing cloud identities across multi-cloud environments, their permissions and the resources they access across all their cloud environments. This establishes a baseline and identifies existing over-privileged accounts, dormant identities and toxic permission combinations.
- Define clear roles and responsibilities. Establishing clear, well-defined roles within the organization, mapped to the specific cloud resources and actions required for each job function, forms the foundation for applying POLP. This approach ensures that entitlements are granted based on actual business needs rather than convenience.
- Enforce the POLP as a default. All new accounts, both human and nonhuman, should be provisioned with only the minimum privileges necessary. Elevated access should be granted only when specifically justified. This core tenet of CIEM reduces the attack surface by limiting the actions an attacker could take if an identity were compromised.
- Embrace automation for entitlement management. Organizations should use CIEM's automation capabilities for tasks such as identifying over-privileged accounts, recommending rightsizing actions and automatically revoking unnecessary permissions. In dynamic cloud environments, manual entitlement management is unsustainable. Automation reduces human error, ensures consistency and enables security teams to scale their efforts effectively.
- Implement just-in-time and just-enough access. For tasks that require elevated privileges, organizations should use CIEM to grant temporary, time-bound access, with automatic revocation once the task is completed. This approach significantly reduces the window of opportunity for attackers to exploit elevated permissions and aligns with the principles of a zero-trust security model.
- Conduct continuous monitoring and auditing. CIEM shouldn't be treated as a one-time setup. Organizations must continuously monitor access patterns, entitlement changes and user behavior. Regular audits and permission reviews are essential to detect privilege creep and malicious activities. As cloud environments are constantly evolving, continuous monitoring ensures that entitlements remain aligned with the POLP and supports real-time threat detection.
- Integrate CIEM with broader security tools. Organizations should integrate their CIEM tools with existing IAM, privileged access management, CSPM and security information and event management (SIEM) systems. This integration creates a more holistic and intelligent security ecosystem that enhances threat detection, automated response workflows and centralized security insights.
To demonstrate CIEM value and benchmark progress, organizations should also track the following KPIs:
- Mean time to detect for entitlement risks. MTTD is the measure of how quickly entitlement anomalies or excessive permissions are discovered.
- Mean time to respond to entitlement anomalies. MTTR measures the duration from anomaly detection to remediation.
- Percentage of entitlements managed automatically. This metric tracks the proportion of entitlement tasks, such as provisioning or deprovisioning, that are handled by CIEM vs. manually.
- Entitlement review completion rate. This tracks governance maturity and audit readiness.
- Cross-cloud policy consistency score. This evaluates how uniformly policies are applied across providers.
Organizations should also be aware of the following mistakes and avoid them when implementing CIEM:
- Lift and shift of on-premises policies. Organizations should avoid blindly transferring on-premises access control policies to the cloud. Cloud environments have different architectures, a high number of nonhuman identities and unique attack vectors that require cloud-native security approaches and controls.
- Ignoring nonhuman identities. Service accounts, application programming interfaces and automated processes drive a large share of cloud access. Excluding these nonhuman identities from a CIEM strategy introduces a security gap, as many breaches originate from compromised machine credentials. An effective CIEM approach must treat the entitlements of applications, services and workloads with the same level of scrutiny and priority as those of human users.
- Lack of continuous monitoring. Treating CIEM as a one-time setup undermines its effectiveness. Given the highly dynamic nature of cloud environments where permissions frequently change, continuous monitoring is essential to prevent privilege creep.
- Insufficient stakeholder buy-in. Without alignment and support from leadership, security and especially development and DevOps teams, CIEM initiatives can face internal resistance due to concerns about agility. Clear communication of benefits and early involvement of stakeholders are critical to success.
- Over-reliance on manual processes. Managing entitlements manually at cloud scale isn't sustainable and increases the risk of errors. Organizations should use the automation capabilities of CIEM tools to streamline entitlement governance and reduce operational burden.
How to choose the right CIEM
When selecting a CIEM tool, organizations should assess it against the following key criteria:
- Cloud footprint compatibility. Organizations should select a CIEM that aligns with their existing cloud footprint, ensuring support for all relevant providers such as AWS, Azure and Google Cloud. The platform should offer normalized entitlement views to streamline access management across environments. Additionally, agentless deployment capabilities are preferred to minimize implementation complexity and reduce operational overhead.
- Depth of visibility. Organizations should prioritize products capable of mapping not only direct access but also inherited and transitive entitlements. Advanced platforms often provide graph-based visualizations to help security and risk teams understand access paths, privilege escalations and the broader implications of complex identity relationships across cloud environments.
- Risk-based prioritization. Organizations should choose a platform that incorporates behavioral analytics and entitlement risk scoring to spotlight the most critical vulnerabilities. Features such as anomaly detection and alerts for toxic permission combinations let security teams prioritize remediation efforts effectively and align entitlement controls with overall risk management objectives.
- Automation and workflow integration. Organizations should evaluate platforms that streamline entitlement discovery, periodic reviews and remediation through automation. Seamless integration with IT service management tools, security orchestration, automation and response platforms, and ticketing systems such as ServiceNow or Jira can enhance operational efficiency and reduce response time to access-related threats.
- Policy customization and enforcement. Organizations should opt for approaches that support customizable access policies aligned with their governance requirements, including role-based access control and attribute-based access control. CIEM tools enable fine-grained policy enforcement and support features, such as just-in-time access and temporary privilege elevation. This reduces standing privileges without disrupting productivity.
- Audit and compliance support. Organizations should seek platforms that deliver comprehensive logging, real-time reporting and detailed audit trails to meet regulatory requirements, such as ISO 27001, SOC 2 and the Health Insurance Portability and Accountability Act. These capabilities not only support external audits and internal governance but also enhance visibility into entitlement changes and policy enforcement activities.
- Vendor ecosystem and roadmap. Organizations should assess providers based on their reputation, the strength of their customer support and how well their product integrates with existing security tools. Additionally, evaluating the vendor's innovation trajectory, such as plans for AI-driven entitlement analysis and alignment with DevSecOps practices, can ensure the product meets future needs and is scalable with evolving enterprise needs.
CIEM vs. SIEM vs. CSPM
CIEM, SIEM and CSPM are three important security approaches in modern cloud and cybersecurity strategies. These three approaches complement each other in a layered cloud security strategy. CIEM governs who can access what, CSPM ensures the environment is properly configured, and SIEM keeps watch for threats in real time. Together, they create a holistic approach to cloud security management. The following descriptions provide more detail on their functions:
- CIEM focuses on managing who has access to what within cloud environments. It prevents privilege creep and enforces POLP access by continuously analyzing and controlling entitlements across multiple cloud platforms. CIEM supports identity governance, access rightsizing and privilege escalation detection.
- SIEM is designed to collect and analyze security event data from across an organization's IT infrastructure. By aggregating logs and security alerts from diverse sources such as firewalls, servers and endpoints, SIEM enables threat detection, investigation and incident response. In this sense, it constantly monitors activity, sending alerts when suspicious behavior occurs.
- CSPM identifies and remediates misconfigurations in cloud infrastructure. It ensures that cloud environments adhere to best practices and compliance requirements by continuously auditing policies and configurations. CSPM checks that every virtual access point and firewall is secured to prevent accidental exposures.
CIEM vs. CNAPP
As cloud environments have expanded in complexity, so too have the practices, policies and tools developed to manage and secure them. Consequently, organizations often find themselves deploying a fragmented array of individual technologies, such as CSPM and CWPP, to bring order and enhance the security of their cloud tech stacks. While these different technologies each have unique strengths and capabilities, they also frequently come with overlapping functionalities and benefits.
In response to this growing complexity and fragmentation, CNAPP has gained increasing prominence. According to Gartner's research, CNAPPs address the full lifecycle protection requirements of cloud-native applications, from development to production. CNAPPs unify multiple capabilities into a single, comprehensive platform, simplifying cloud security. This integration offers a consolidated alternative to disparate tools such as CSPM, CWPP and CIEM.
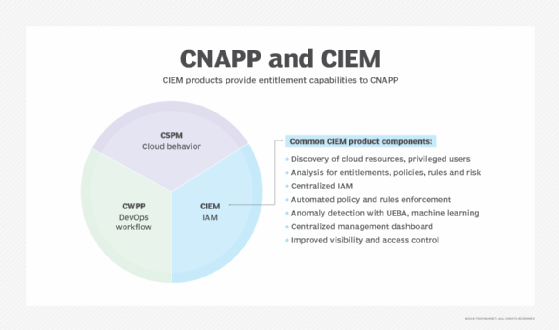
A CIEM is specific to entitlement management. CNAPPs, on the other hand, bring together the CIEM, CSPM and CWPP capabilities to create a holistic, integrated set of security and compliance capabilities for cloud-native applications. As such, CNAPPs deliver features that CIEM systems don't, such as the ability to scan containers and infrastructure as code.
Learn how to conduct a cloud security assessment to identify risks, evaluate controls and ensure your organization is keeping up with evolving cloud threats.







