ciphertext feedback (CFB)
What is ciphertext feedback (CFB)?
In cryptography, ciphertext feedback (CFB), also known as cipher feedback, is a mode of operation for a block cipher. Ciphertext refers to encrypted text transferred from plaintext using an encryption algorithm, or cipher. A block cipher is a method of encrypting data in blocks to produce ciphertext using a cryptographic key and algorithm.
Like cipher block chaining (CBC), ciphertext feedback uses an initialization vector (IV). CFB uses a block cipher as a component of a random number generator. In CFB mode, the previous ciphertext block is encrypted and the output is XORed with the current plaintext block to create the current ciphertext block. The XOR operation conceals plaintext patterns. Plaintext cannot be directly worked on unless the blocks from either the beginning or end of the ciphertext are retrieved.
The entropy that results can be implemented as a stream cipher, a method of encrypting text whereby a cryptographic key and algorithm are applied one bit at a time to each binary digit in a data stream. CFB is primarily a mode to derive some characteristics of a stream cipher from a block cipher. Similar to CBC mode, changing the IV to the same plaintext block in CFB results in different output. Though the IV need not be secret, some applications would consider this desirable. Chaining dependencies are similar to CBC in that reordering ciphertext block sequences alters decryption output, as decryption of one block depends on the decryption of the preceding blocks. This means that a corrupted bit that has been manifested during transmission will propagate that error, affecting transmitted bits in the block -- usually one to two bytes that follow.
How is cipher feedback used?
CFB is used in encryption algorithms such as Data Encryption Standard (DES), Triple DES and Advanced Encryption Standard (AES). If CFB mode is used within the encryption algorithm, it's often used to encrypt the following services:
- Wi-Fi communications
- secure websites
- chip-based security
- file encryption
- Secure Sockets Layer or Transport Layer Security encrypted virtual private network tunnels
- Simple Mail Transfer Protocol email
- messaging services based on the Extensible Messaging and Presence Protocol
- secure FTP
- Secure Shell
- Voice over IP
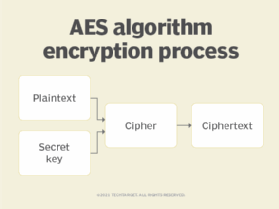
The AES algorithm below shows where the cipher modes, including CFB, fit into the encryption process. The unencrypted plaintext is combined with a secret key and encrypted using one of five supported cipher modes, including CFB. The output is an encrypted ciphertext that can be securely transported across unsecure networks.
What is the difference between CBC and CFB?
CBC and CFB perform the same general data encryption duties, with a few notable exceptions. First, CFB mode data is encrypted in units that are smaller than a predefined block size cipher unit, which is usually 64 bits, as is the case with CBC. Instead, CFB encrypts units in 1- or 2-byte (8- or 16-bit) block sizes and processes each bit at a time as opposed to the entire 64 bits. Therefore, using CFB mode, no padding process is needed when the data size is less than 64 bits and needs appending to meet the 64-bit length requirement.
Another major differentiator between CBC and CFB is how they encrypt plaintext data. Unlike CBC, which directly encrypts plaintext blocks, CFB encrypts the previously encrypted plaintext block and then adds this to the next plaintext block. This means that the same algorithm used to encrypt the data can be used to decrypt it, which simplifies the decryption process of CFB.






